CloudSEK uncovers a sophisticated malware campaign where attackers impersonate PDFCandy.com to distribute the ArechClient2 information stealer. Learn how this scam works and how to protect yourself.
Cybersecurity researchers at CloudSEK have a new campaign exploiting the popularity of PDFCandy.com, an online file conversion tool used by over two and a half million people, including over half a million from India alone.
As per their research, shared with Hackread.com, attackers are distributing ArechClient2 malware to steal private information like browser usernames and passwords. It is a SectopRAT family malware active since 2019 and is spread through deceptive online advertising via Google Ads or fake software updates.
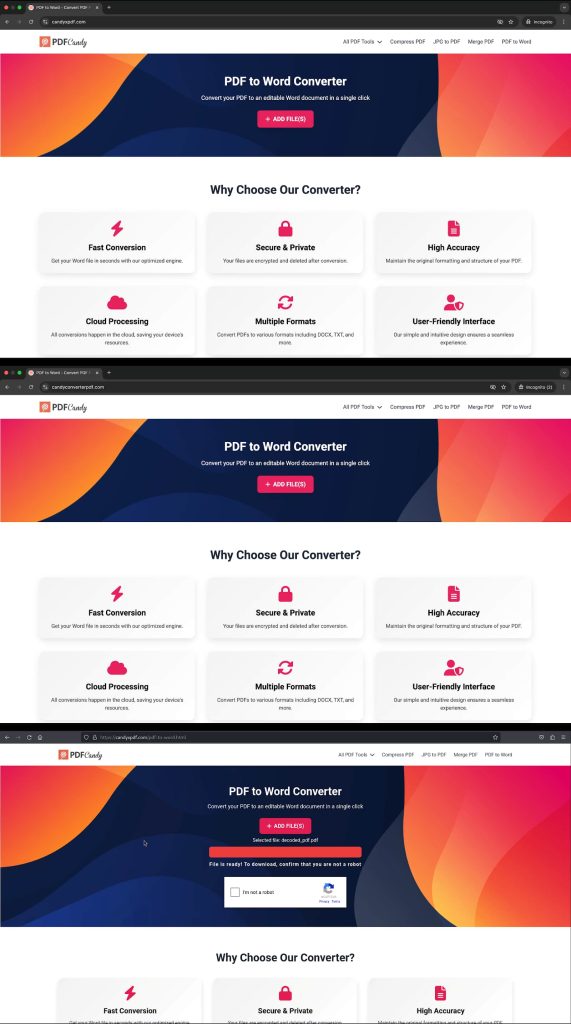
Reportedly, attackers have created a fake PDF to DOCX converter that is similar to the legitimate pdfcandy.com. They have gone to great lengths to copy the look and feel of the real website. Such as they use similar web addresses to trick unsuspecting users and have “meticulously replicated the user interface of the genuine platform and registered similar-looking domain names to deceive users,” CloudSEK’s researchers noted in the blog post.
Once a user lands on one of these fake sites, they are immediately asked to upload a PDF file for conversion, playing on a common need of many internet users. It even shows a fake loading animation as if a real conversion is happening, probably to build trust.
Then, unexpectedly, it presents a CAPTCHA verification, similar to what legitimate websites use for security. This marks a critical step in the attack where “social engineering transitions to system compromise,’ the report reads. This means the attack relies on manipulating how users typically interact with websites.
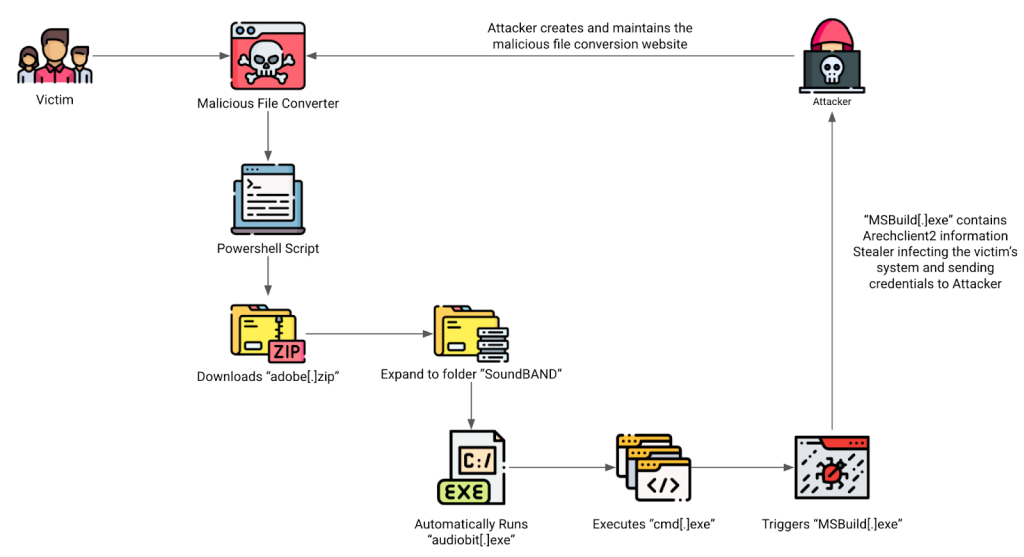
Introducing CAPTCHA serves two purposes: making the fake site appear more real and allowing users to click without thinking. Next, the website instructs users to run a command using Windows’ built-in tool PowerShell, leading to a system compromise. The command analysis reveals a series of redirects, starting with an innocent link and leading to a file named “adobe.zip,” hosted on 1728611543, which has been flagged as malicious by multiple security services.
The file contains a folder called “SoundBAND” with a dangerous executable file called “audiobitexe.” The attacker launches a multi-stage attack using a legitimate Windows program and a Windows tool, launching ArechClient2 information-stealing malware.
It is worth noting that the FBI warned on March 17, 2025, about malicious online file converters being used to distribute harmful software, so this threat is not new.
“Cybercriminals across the globe are using any type of free document converter or downloader tool. This might be a website claiming to convert one type of file to another, such as a .doc file to a .pdf file. It might also claim to combine files, such as joining multiple .jpg files into one .pdf file. The suspect program might claim to be an MP3 or MP4 downloading tool,” the agency explained.
To protect against such threats, you should be cautious when using online file conversion services, verify website legitimacy before uploading files, pay attention to URLs, and be wary of unexpected prompts.