The new phishing scam redirects users multiple times and also uses CAPTCHA before stealing credentials.
Since the advent of phishing in itself, different types of scams have existed ranging from one-fits-all emails to targeted spearphishing campaigns. One such type happens to fall into the category of subpoena themed emails in which the attacker claiming to be an authority, tries to convince the victim into falling for their trap.
These although not so common have occurred from time to time. An example is of November last year when malicious actors targeted users posing as the UK’s Ministry of Justice and tried to infect them with a malware named “Predator the Thief.”
See: Microsoft, PayPal & Facebook most targeted brands in phishing scams
Similarly, just a couple of days ago, Armorblox – an email protection company – has released a report on how this time threat actors are sending fake emails purportedly from the UK’s supreme court.
Here is a screenshot of the phishing email:
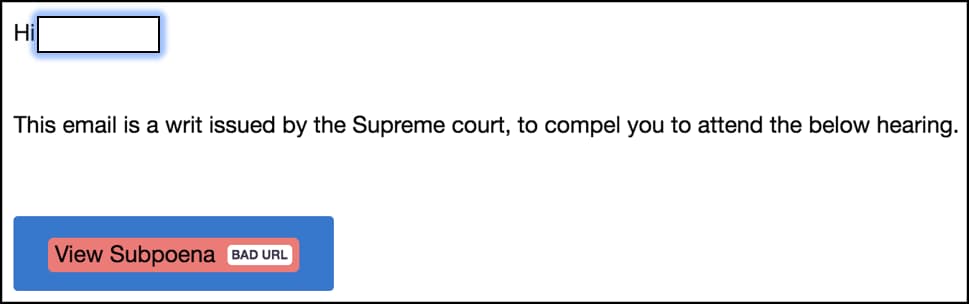
To make sure, it evades regular security filters, the attackers only send the email to specific users instead of bulk-messaging which ensures that it isn’t “caught in the bulk email filters of Exchange Online Protection (EOP).”
For the unacquainted, EOP is Microsoft’s own email protection service aimed towards removing malicious content from email messages & even filtering spam. Therefore, by employing this low quantity technique, the phishers are able to stay under the radar.
See: How Phishing Has Evolved in 2019
Coming to the emails themselves, they contain a “zero-day link” that redirects the user through a series of steps in a bid to increase the apparent legitimacy of the message. This first involves going through a typical captcha as shown below. According to an in-depth blog post published Armorblox,
The inclusion of CAPTCHA also makes it harder for security technologies relying just on URL redirection abilities to follow the URL to its final destination.
A few anomalies are present in the captcha here but nonetheless, no user really has the time to scrutinize them which lowers its detection rate. For example, the text above the captcha states, “Kindly verify you human” which being grammatically wrong would clearly not be the work of a Supreme court-based page.
See: 10 Crucial Security Tips to Reduce Data Loss in Microsoft Office 365
Moreover, the researchers add by stating that the “master domain of the pages is ‘docketsendercom’ that, while not malicious, doesn’t seem like a legitimate domain.”
Then moving on, at the very end, a Microsoft Office 365 page is presented which asks the user of their credentials. Located at an attacker owned domain name, invoicesendernowcom, it would be discernible to any user paying attention but again, quite a lot of times, users seldom care to double-check.
Here are the screenshots of the phishing scam:
How Armorblox detected this campaign was through a series of monitoring techniques which include analyzing the tone of email messages, the frequency of the email addresses’ communication in the past with the receiver, and if only specific users instead of the entire company were being emailed which would ring some spearphishing alarms.
See: Simple Tips to Manage and Prevent Social Engineering Attacks
To conclude, as a user to remain safe from such attacks, no rocket science is needed. A few simple precautions would suffice:
- Carefully check the sender’s email address once you receive an email as the name can be easily impersonated as it was done in this case.
- If it seems necessary to open a link contained within the email, check the domain names of the redirected pages carefully.
- If you’re unsure about the legitimacy of a certain email, don’t take risks. It is better to consult an IT professional in your organization or perhaps an outside one.
By following these simple yet effective steps, you can remain safe for long.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.












