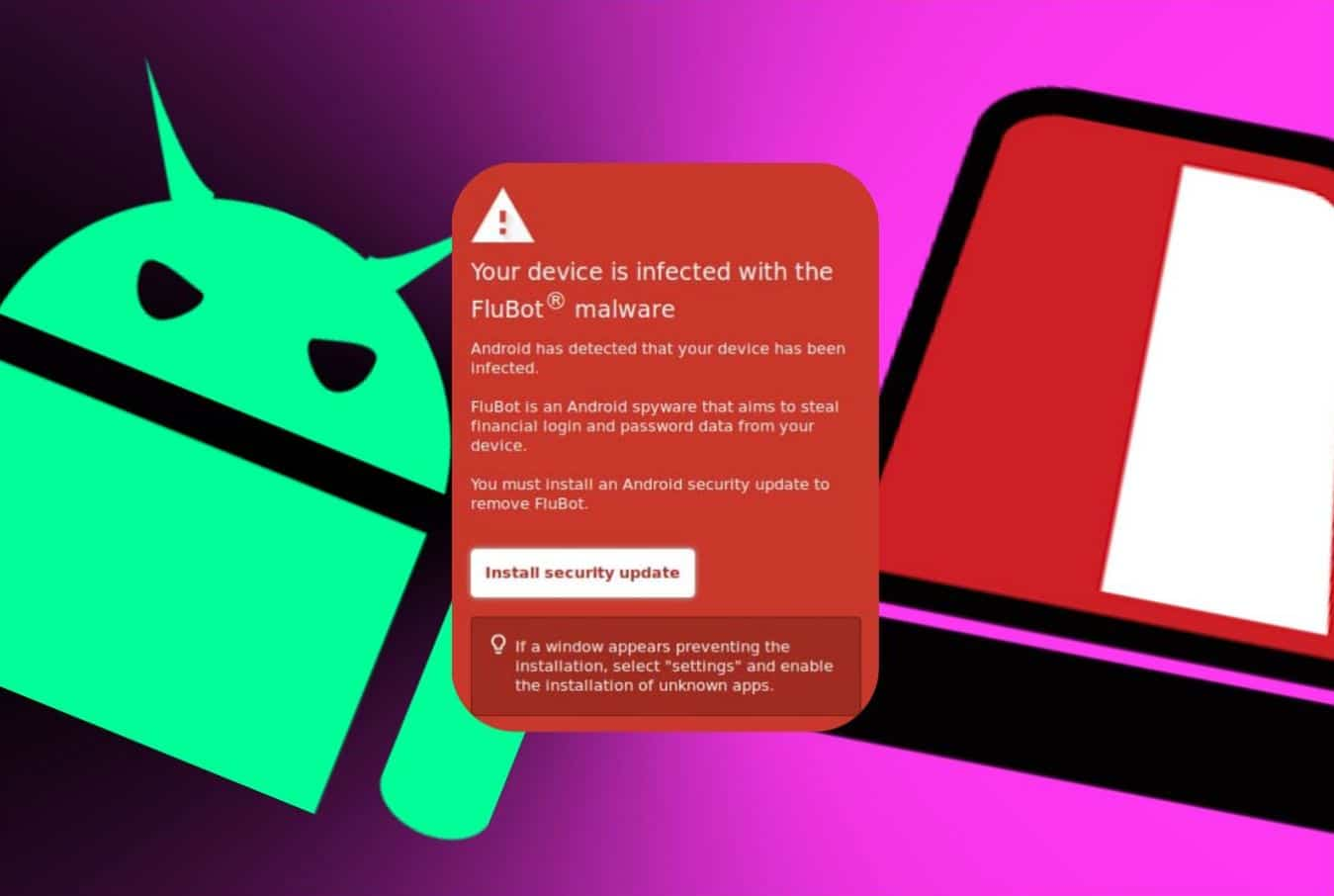
The security update is obviously phony but looks authentic that can deceive users into installing Flubot malware on their devices.
New Zealand’s Computer Emergency Response Team (Cert NZ) has issued a new warning involving the spread and infection of the infamous Flubot malware known for its password stealing capabilities.
According to authorities, the threat actors are now trying to trick users into believing that their devices are infected with Flubot malware by displaying a fake security warning message.
SEE: GriftHorse Android malware hit 10 million devices in 70 countries
The warning is obviously phony that may become a reality if the recipient of this message clicks on the Install Security Update button that’s part of the message.
Flubot Strikes Again
CERT NZ released an advisory to warn users about a deceptive text message that reads: “Android has detected that your device has been infected.” The message contains further instructions on how to install a security update to remove the malware.
However, when the recipient clicks on the install security update button, this action triggers the Flubot infection. CERT NZ also mentioned that Flubot malware message is targeting Android phones, and the content of these messages is constantly changing.
For instance, previously, the message was supposedly sent by a courier company, alerting users to click on an enclosed URL or download an app to know parcel delivery details.
Flubot Looking to Steal Banking Information
According to New Zealand’s Telecommunications Forum’s chief executive, Paul Brislen, the payload resends the text through the users’ address book. Additionally, it asks for banking information.
“Needless to say at a time when everyone is using courier delivery services, this has the potential to cause a lot of damage,” Brislen said.
Threat Actors Also Using Your Photos to Install Flubot
In addition to fake text messages from the courier service, the Flubot banking trojan is tricking Android users into downloading malicious software in the disguise of fake Flubot deleting the app or upload photos of the victims as well. A fake text is sent to random Android users stating that the recipient’s photos have been uploaded.
Flubot against Android smartphones
Flubot malware was initially observed in Spain in late 2020 and within months its infection was found spreading Android devices globally including Australian banks.
However, in March 2021, the malware was caught with additional capabilities including mimicking popular apps like FedEx, DHL, Correos, and Chrome to steal user data.
How to Stay Protected?
Since threat actors continually update their attack tactics, CERT NZ urges users not to fall prey to this scam and forward the texts to 7727 before deleting the message.
“Given that the wording of these texts has changed within a short timeframe, it is likely the wording will change again. Be wary of any suspicious text messages you receive, asking you to click on a link, and forward any new suspicious texts to 7726.” advisory from CERT NZ read.
Forwarding them to 7726 helps CERT NZ and the Department of Internal Affairs to permanently shut down the links provided in the message and contact users who have been infected by the app.
It is important to note that only Android users can be targeted with these fake texts, while iOS devices may receive the message but won’t get infected with Flubot.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.