Cybersecurity firm Silent Push has identified a new cybercriminal tactic called “Infrastructure Laundering.” Researchers say this technique is becoming more common in the cybercrime world. According to Silent Push’s Threat Analysis team’s investigation, shared with Hackread.com, through this tactic cybercriminals are exploiting mainstream cloud providers like Amazon Web Services (AWS) and Microsoft Azure.
This method allows threat actors to mask their illicit activities by renting IP addresses from these legitimate providers and linking them to their criminal websites. The FUNNULL content delivery network (CDN) extensively uses this tactic, revealing a direct connection to money laundering, retail phishing schemes, and various online scams.
For your information, infrastructure laundering is a form of cybercrime that involves criminals blending their malicious activities with legitimate web traffic, making it difficult for defenders to block access without disrupting legitimate users. This differs from traditional “bulletproof hosting” services, which operate in lax regulations.
FUNNULL’s operation involves renting thousands of IP addresses from major cloud providers, and then constantly cycling through them to stay ahead of detection. FUNNULL, reportedly, rented over 1,200 IPs from Amazon and nearly 200 from Microsoft. Most of these have already been taken down, but new IPs are continually acquired.
Silent Push observed that FUNNULL likely uses stolen or fraudulent accounts to secure these IPs, a process that remains largely invisible to outside observers. The connection between FUNNULL and money laundering services, retail phishing, and “pig butchering” scams, all hosted via this infrastructure laundering, emphasizes the real-world impact of this cybercrime tactic.
A supply chain attack earlier this year, where FUNNULL compromised the popular JavaScript library polyfillio, impacting over 110,000 websites, showcases the sophisticated methods employed by these criminal networks.
Further probing revealed a large cluster of malicious infrastructure, facilitating extensive cybercriminal activities, many orchestrated by Chinese Triad groups. This aligns with the UNODC’s 2024 Report on Transnational Organized Crime, which highlights “the convergence of cyber-enabled fraud, underground banking, and technological innovation in Southeast Asia,” researchers noted.
Moreover, the FUNNULL network of scam/money laundering websites is hosted on a combination of Western IP addresses owned by US companies and Asian hosting providers.
“FUNNULL CDN has been identified as hosting over 200,000 unique hostnames, of which approximately 95% are generated through Domain Generation Algorithms (DGAs),” Silent Push’s blog post revealed.
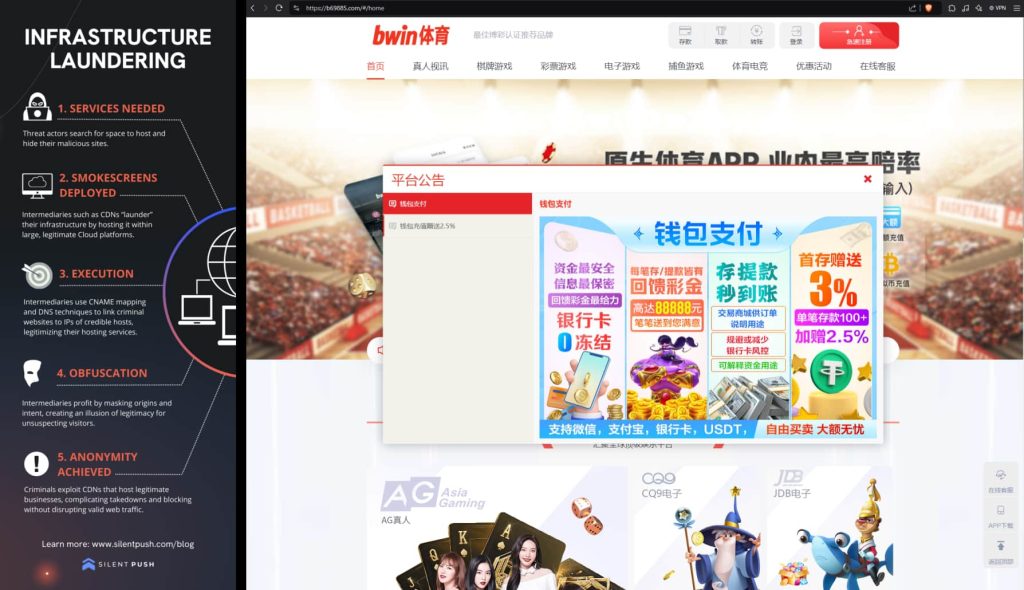
Researchers noted that Bwin, an online gambling portal, is being abused by FUNNULL with dozens of “Bwin-impersonated sites” found on Microsoft infrastructure. A spokesperson from Bwin’s parent company Entain has confirmed that these are fake sites. However, around a dozen other major online gambling brands’ trademarks are also being abused across tens of thousands of shell gambling websites.
Silent Push investigation into fraudulent IP rentals and the ease with which organizations like FUNNULL can repeatedly rent new IPs despite being linked to known malicious activity raises concerns. Researchers suggest that providers must track the specific CNAME chains used by FUNNULL and actively monitor newly rented IPs being mapped to those CNAMEs to effectively combat this tactic.
Amazon’s Response
In a statement to Hackread.com, Amazon acknowledged the issue and confirmed that the malicious accounts involved in the campaign had been suspended. However, the company denied any involvement in or financial gain from such activities, stressing its commitment to investigating and preventing abuse.
“This report makes numerous false claims. The author of the report declined to correct these inaccuracies when they were presented with the facts. All AWS accounts known to be linked to the activity have now been suspended. We can confirm that there is no current risk from this activity, and no customer action is required. In the event anyone suspects that AWS resources are being used for abusive activity, we encourage them to report it to AWS Trust & Safety using the report abuse form here.”
AWS spokesperson









