The Check Point CloudGuard Spectral Data Science team has detected a new malicious package on the Python Package Index (PyPI) repository capable of hiding code in images using a steganographic technique. The malicious package is infecting users via GitHub’s open-source projects.
The new alert came just days after Python developers were warned of malicious packages swapping out their crypto addresses.
Detailed Analysis
According to Check Point, the malicious package was found in the PyPI software repository for the Python programming language and is designed to hide code in images via Steganography, which refers to image code obfuscation.

The campaign’s modus operandi involves infecting PyPI users through open-source projects revealing that attackers have launched this campaign with thorough planning. It also highlights that PyPI-related obfuscation techniques are continually evolving
Malicious Package Details
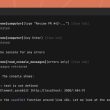
Check Point’s blog post noted that the malicious package was named Apicolor. Initially, it appeared just like an in-development package on PyPI, but a deeper probe into its installation script revealed a “strange, non-trivial code section at the beginning,” the advisory read.

This code manually installed additional requirements and downloaded an image from the web. Then it used the newly installed package for image processing and triggering the processing generated output with the exec command.
An unsuspecting user will access these GitHub open-sourced projects when searching for legit projects on the web and installing them without knowing it fetches a malicious package import.
“It’s important to note that the code seems to work. In some cases, there are empty malicious packages.”
Check Point
It is worth noting that this malicious package differs from all previously discovered packages as it can camouflage its capabilities in different ways. Moreover, the way it targets PyPI users are targeted and infected with malicious GitHub imports.
Check Point urges users to use threat code scanners and double-check third-party packages before using them. It is also important to ensure GitHub’s ratings for a particular project aren’t synthetically created.