New Golang botnet “Zergeca” evades detection and launches DDoS attacks. Ensure your IoT devices are fully patched against vulnerabilities and are using secure passwords to prevent infection.
Cybersecurity researchers at QiAnXin XLab have identified a new Golang-based botnet “Zergeca.” The botnet, discovered through the efforts of XLab’s Cyber Threat Insight Analysis (CTIA) system, can execute advanced distributed denial-of-service attacks (DDoS attacks) and boasts a range of other malicious functionalities.
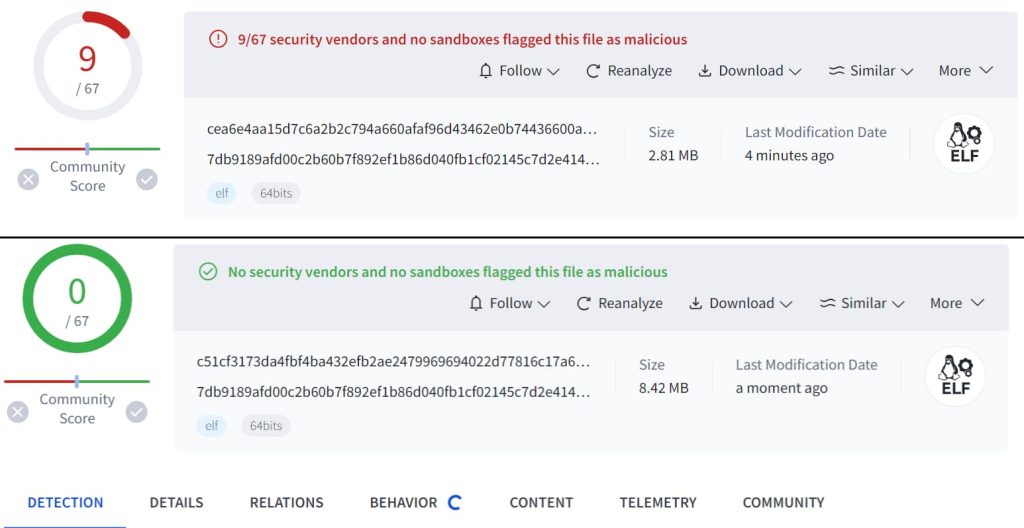
The discovery began on May 20, 2024, when a suspicious file was flagged by the CTIA system. The file, which had been uploaded to VirusTotal from Russia, was packed with a modified UPX and initially evaded detection by antivirus engines.
Later that same day, another file with the same characteristics was uploaded from Germany, raising further suspicions. Upon thorough analysis, researchers confirmed that the file was part of a sophisticated botnet implemented in Golang.
According to QiAnXin XLab’s report, Zergeca is not just a typical botnet. It supports six different DDoS attack methods and offers capabilities for proxying, scanning, self-upgrading, persistence, file transfer, reverse shell, and collecting sensitive device information.
Additionally, the botnet uses unique network communication techniques, including multiple DNS resolution methods with a preference for DNS over HTTPS (DoH) and the Smux library for encrypted command and control (C2) communication.
The botnet’s C2 infrastructure has a notable history. The main C2 IP address, 84.54.51.82, has been linked to two Mirai botnet variants since September 2023. This suggests that the creator of Zergeca has significant experience with botnet operations, having previously managed Mirai-based attacks.
In early June, XLab’s command tracking system detected a new DDoS command, vector 7, which was not supported by the current Zergeca samples. This indicated that the botnet’s author was actively developing and updating its capabilities. On June 19, a new Zergeca sample supporting this new vector was captured, confirming ongoing development efforts.
Despite its extensive functionality, Zergeca samples have a low detection rate. Analysis showed that most antivirus solutions classify the malware based on file hashes. Thus, any change in the file’s hash, such as appending additional bytes, significantly reduces the detection effectiveness. This was demonstrated when the detection rate of a Zergeca sample dropped to zero after being unpacked from its UPX-packed state.
The botnet’s persistence is achieved through system services that ensure the malware remains active even after device reboots or process terminations. Additionally, Zergeca’s “Silivaccine” module aggressively removes competing malware to maintain exclusive control over infected devices.
The primary method of Zergeca’s propagation includes exploiting weak Telnet passwords and known vulnerabilities (e.g., CVE-2022-35733, CVE-2018-10562). Recent DDoS attacks attributed to Zergeca have targeted regions including Canada, the United States, and Germany, with the ackFlood attack being the most prevalent.
RELATED TOPICS
- Mirai-like Botnet Targets Zyxel NAS Devices with DDoS Attacks
- Mirai-based NoaBot Botnet Hits Linux Systems with Cryptominer
- Goldoon Botnet Hit D-Link Devices by Exploiting 9-Year-Old Flaw
- Russian Hackers Target Ubiquiti Routers for Data, Botnet Creation
- Examining the US Government’s DDoS Protection Guidance Update