A good hacker with an excellent set of skills and a sense of humor.
Online users are frequently the target of botnet malware campaigns, as cybercriminals are always hunting for extorting money or stealing data to carry out a range of scams. Emotet is one of the most commonly used botnets nowadays, which is distributed via wireless networks and can load different types of malware.
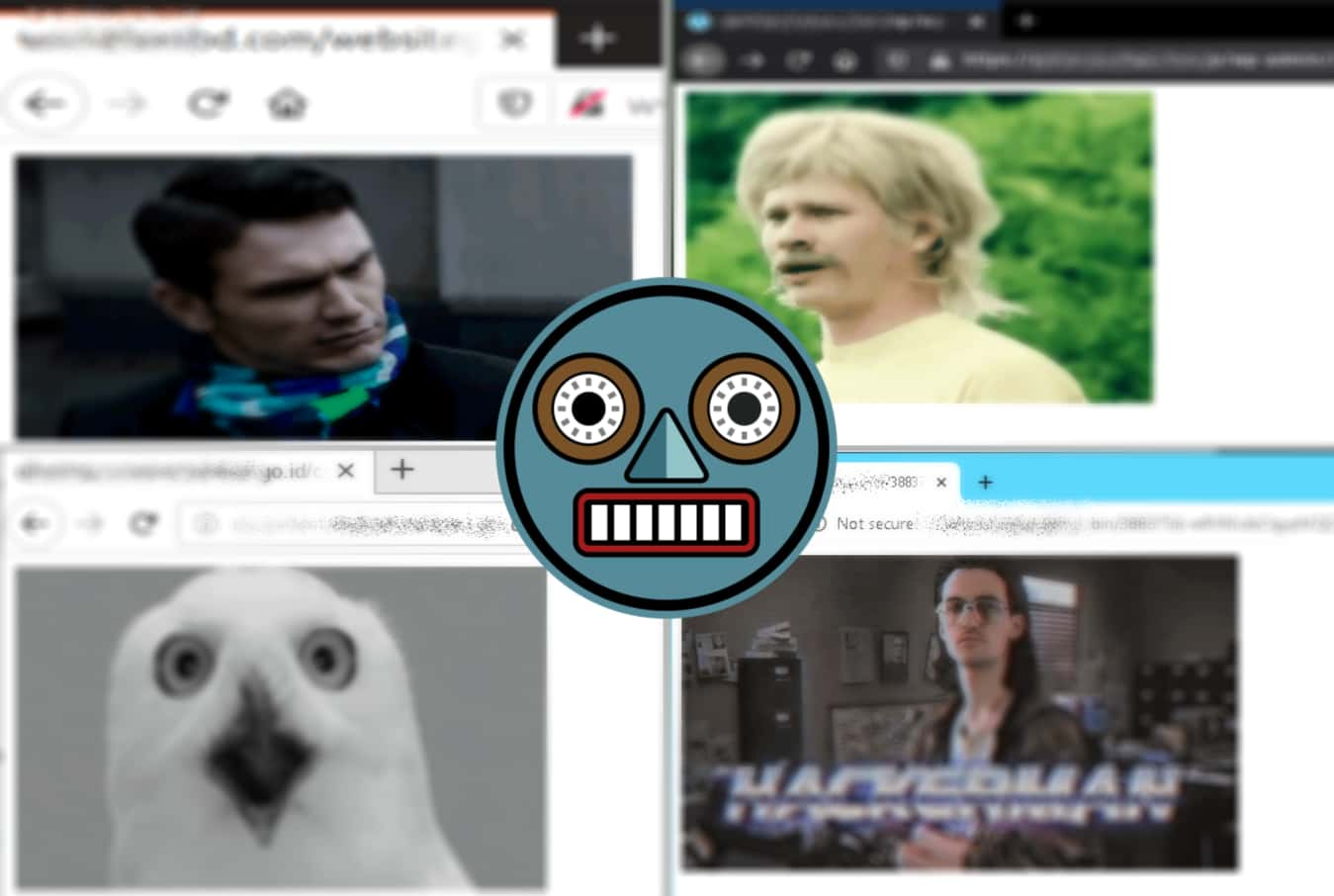
However, an unidentified genius hacker has come up with a hilarious twist on the use of Emotet by replacing Emotet’s malicious payloads with funny, animated GIFs and memes.
See: Hackers deface Roblox accounts with pro-Trump messages
Kevin Beaumont, Microsoft’s cybersecurity researcher, revealed in their blog post that the hacker has replaced around 25% of the botnet payloads so far, which has affected its operations drastically.
It is worth noting that the botnet bombards the victim’s computer with fake business-related emails containing infected Office documents or a URL of infected Office files. When the recipient downloads the infected files or clicks on the links that lead to compromised websites, the file displays the Enable Editing button to allow execution of macros, once executed the macros download Emotet malware onto the device.
In the absence of a payload, Emotet malware cannot infect the device. That’s why threat actors are currently busy finding a way to regain their lost control of the malware’s operations while the cybersecurity community is praising the hacker. Cryptolaemus researchers, known for their research on Emotet, have regarded the hacker as a White Knight.
Reportedly, the hacker is uploading images of James Franco, and the botnet’s hijacked websites are displaying the Hackerman meme.
Cryptolaemus researchers have posted a video illustrating what happens when someone opens the malicious documents or links. Interestingly, the payloads were getting replaced within less than an hour before the news made headlines. Now, the hacker is replacing the payload within two minutes.
Emotet operators were storing malware components on WordPress websites that they had hijacked. They used low-standard web shells and open-source scripts with the same password for all shells to control the hacked websites.
https://twitter.com/GossiTheDog/status/1210520720222097408
That’s how White Knight was able to identify the mechanism of Emotet botnet. After obtaining the password, it became easy for the hacker to change the payload with harmless GIFs and memes.
See: Emotet Trojan now exploits WiFi networks to infect nearby devices
As of July 27th, the malware operators were battling to restore the payloads while the hacker was continually replacing it with funny images. This had disrupted scammers’ expectations from Emotet to a great extent while the victims were having the last laugh as they stayed protected from getting scammed.
However, earlier today, Kevin updated their blog post revealing that:
Update 28/07/2020 – Emotet group has fixed their known insecurity issues, with payloads no longer being replaced by James Franco GIFs.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.