A hacker, previously linked to the Tracelo breach, now claims to have breached Twilio’s SendGrid, leaking and selling data on 848,000 customers, including contact and company info.
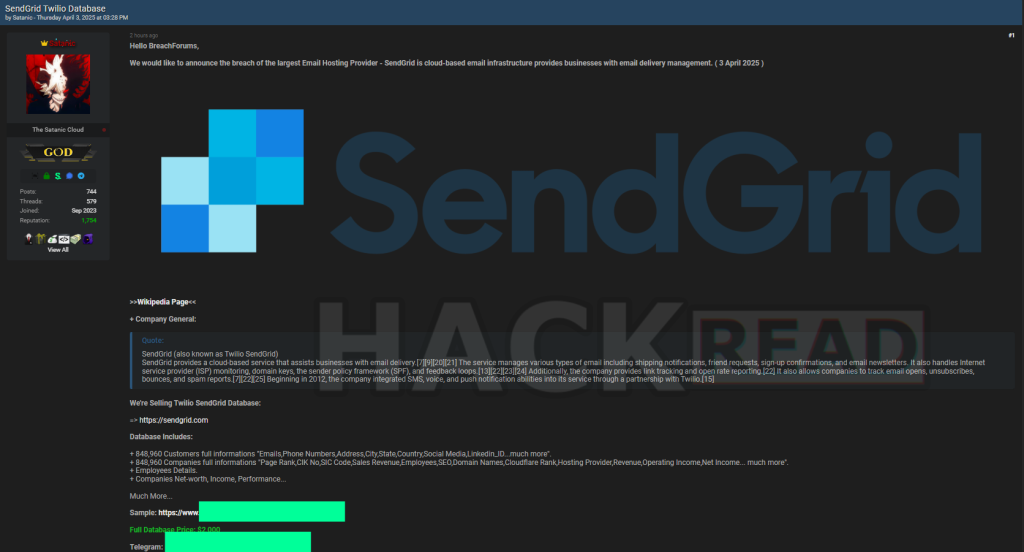
A hacker using the alias Satanic is claiming responsibility for what could be a major breach involving SendGrid, a cloud-based email delivery platform owned by Twilio.
According to a post made earlier today, Thursday, April 3, 2025, on Breach Forums, a popular cybercrime platform, Satanic is offering the allegedly stolen data for $2,000 and has shared a sample to support the claim. In the post, the hacker stated:
“We would like to announce the breach of the largest Email Hosting Provider – SendGrid is cloud-based email infrastructure provides businesses with email delivery management. (3 April 2025).”
What’s allegedly included in the breach?
Satanic claims the database includes full customer and company information for 848,960 entities. Hackread.com’s research team analysed the sample data provided by the hacker, which included the following information:
- Customer emails, phone numbers, physical addresses, cities, states, countries, social media profiles, and LinkedIn IDs
- Company-level data such as domain names, revenue, employee counts, SEO performance, hosting providers, and rankings from services like Cloudflare and Tranco
- Financials like revenue, operating income, net income, and other business metrics
- Employee data and some public-facing executive details
- Information on company tech stacks, including CMS platforms, payment solutions, and CRM tools
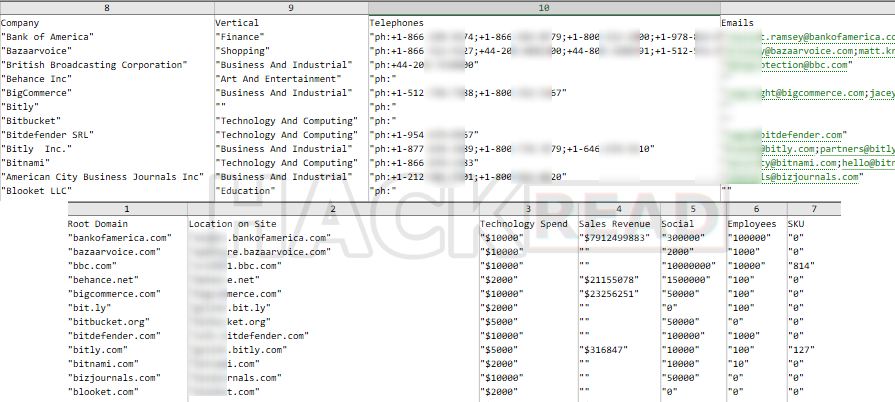
Additionally, among the companies listed in the sample data are Bank of America, Bazaarvoice, and the BBC. The data appears to be structured and highly detailed and includes dozens of metadata fields that go far beyond just contact information.
Each entry features web analytics metrics, internal email addresses (including those of high-level staff), phone numbers, geolocation data, and even insights into backend technologies and accessibility compliance. If the data is authentic, this could be more than a traditional leak.
Satanic’s track record
This isn’t the first time that Satanic has been tied to a major data breach. In September 2024, the same hacker was behind the Tracelo incident, where personal data on 1.4 million users of a smartphone geolocation tracking service was leaked online. Beyond high-profile breaches, Satanic is also known in underground communities for distributing infostealer logs via Telegram.
Twilio’s recent breach history
This would also not be the first time Twilio, SendGrid’s parent company, has been associated with data exposures. On July 4, 2024, the hacker group ShinyHunters leaked a dataset containing 33 million phone numbers belonging to users of Twilio Authy, a two-factor authentication app.
Then, in September 2024, a separate breach exposed 12,000 call records through a third-party tool used by a Twilio customer. While neither incident confirmed a direct compromise of Twilio’s infrastructure, they did raise questions about data security.
Casey Ellis, Founder at Bugcrowd, a San Francisco, Calif.-based leader in crowdsourced cybersecurity, commented on the alleged breach, stating: “This one feels kind of off, and the asking price seems very low for the size and richness of the purported content. Still, at this stage, it’s best to assume that it’s a valid leak, and if so, the comprehensiveness of the dataset is definitely cause for concern. I feel for the folks inside Twilio and SendGrid who are working to burn this down right now.”
UPDATE 1
In a statement to Hackread.com, a Twilio spokesperson said the company has found no evidence suggesting that either Twilio or Twilio SendGrid was breached.
“There is no evidence to suggest that Twilio or Twilio SendGrid was breached. To the best of our knowledge, after reviewing a sampling of this data, we believe that none of this data originated from SendGrid.”
A Twilio Spokesperson
UPDATE 2
Hackread.com attempted to reach Satanic via Telegram and Signal but received no response. However, on Breach Forums, the hacker shared a larger data sample, an additional 10,000 lines, while continuing to claim the data is legitimate and that SendGrid experienced a breach. The threat actor stated:
“They said the database wasn’t taken directly from Sendgrid’s servers. My response was to send them a massive sample to double-check. Whatever, I’m not looking for confirmation of anybody since the data is legit. It is not in my best interest to share the source and how it was hacked.”
UPDATE 3
Update: "Satanic" deleted their Breach Forums post and just like that the alleged SendGrid data is gone. They are now attempting to sell "SendGrid SMTP & API" access without explaining the original Twilio/SendGrid breach claim. No replies on Telegram or Signal. https://t.co/M1BrmAMAyJ
— Waqas (@WAK4S) April 6, 2025