GoDaddy’s employee fell for a phishing scam after which credentials were used to conducted DNS spoofing.
Just a few days ago, a GoDaddy employee fell victim to a spearphishing attack leading to a compromise of their company account. This allowed the attacker to access certain customer records allowing wide-scale manipulation of the settings for the domain names contained within.
These settings include the domain name servers of notable domain names like Escrow.com which is an online brokering service of a range of items. GoDaddy further stated that 5 other user customer accounts were “potentially affected” but didn’t specify the total number of domains within these accounts.
The attack on Escrow.com surfaced at 5:07 PM PST on the 31st of March – a Monday – when the site’s homepage was found to be defaced and replaced with the message as shown In the picture below.
This happened because the perpetrator replaced the original DNS’s from a legitimate server to their own malicious ones. To be specific, the newly pointed IP address was 111.90.14949, located in Malaysia.
Elliot Silver from DomainInvesting immediately got in touch with Escrow.com’s team who reported that no data had been compromised and that they were investigating. Later that evening, the issue had been fixed by 7 PM PST in a couple of hours.
See: Sensitive data on 31,000 GoDaddy servers exposed online
Then on the next day, he received a reply from the general manager of the site pointed him to an official statement released by their CEO. The statement assured customers of the fact that only the domains owned by the company itself were compromised and all customer data was completely safe. Interestingly, another affair occurred during the entire episode which was elaborated on by him:
During the incident, our security team managed to talk to the hacker on the phone. For over an hour the hacker attempted to convince what he thought were domain registry operations to regain access to the account, said the CEO. During this phone call, our security team learned that the route of entry was that the hacker had unlawfully accessed our registrar’s internal support systems and was using them to make changes on Escrow.com’s account.
On the other hand, KrebsOnSecurity learned further details from SecurityTrails – a digital asset tracking company afterward. Their CEO Chris Ueland revealed that “the attacker also obtained free encryption certificates for Escrow.com from Let’s Encrypt.”
Additionally, a reverse DNS lookup on the fake server’s IP address showed that “it is tied to fewer than a dozen domains, including a 12-day-old domain that invokes the name of Escrow.com’s registrar — servicenow-godaddycom.” Visting this address yielded the same note found on Escrow’s compromised domain name earlier although it cannot be accessed now.
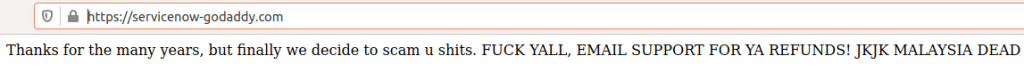
To conclude, no website owner could have prevented such a breach as it was beyond their control in this case. However, a couple of measures can be taken nonetheless which include the following:
1 – Making use of the registry lock feature which basically prevents the DNS records from being changed for a set amount of time once a change request is sent. If the amount of time set is for example even a couple of hours, such unauthorized changes can be prevented.
2- Using two-factor authentication to ensure that even through phishing, someone cannot access your domain account.
But this is not all. The registrar who is GoDaddy, in this case, should also step up their efforts towards training employees in dodging such sophisticated phishing campaigns. This is even more important in light of the frequently cited industry motto of humans happening to be the weakest link in cybersecurity.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.











עברתי על האתר שלך וראיתי מספר בעיות.
עקב המצב אשמח לעזור לך לייצר כמות גדולה של לקוחות ומכירות באונליין.
אפשרי ליצור קשר טלפוני?