In its latest research report, cybersecurity firm Veriti has spotted active exploitation of a vulnerability within “OpenAI’s ChatGPT infrastructure” but there is no evidence that OpenAI itself has been breached.
Their research, shared with Hackread.com, focuses on CVE-2024-27564, a Server-Side Request Forgery (SSRF) flaw, which despite its classification as a medium-severity issue, is being actively exploited in real-world scenarios.
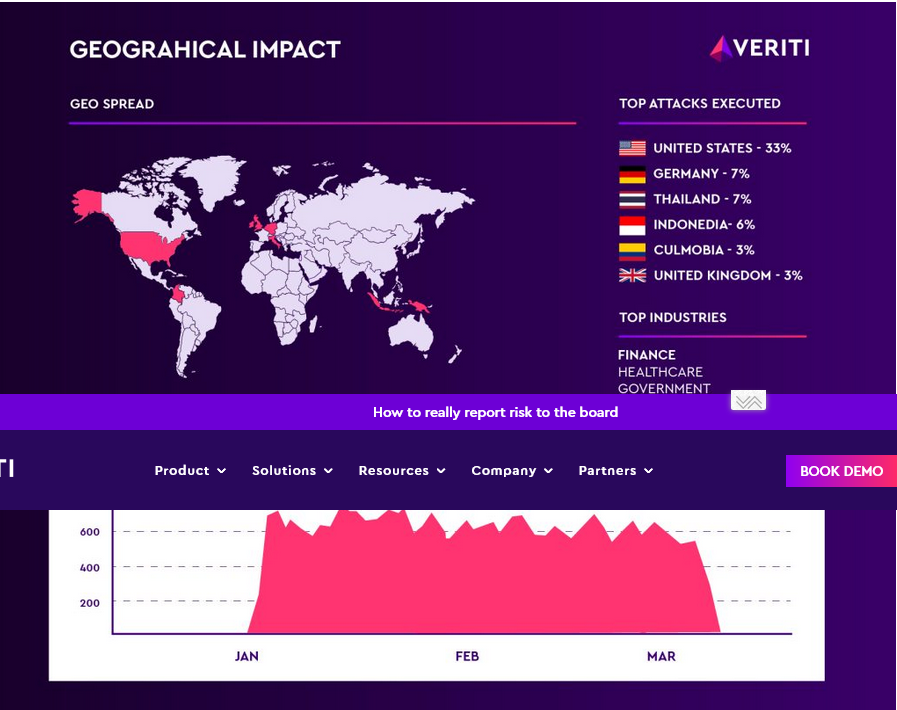
Veriti’s investigation has revealed some troubling findings. One notable discovery is the very volume of attack attempts, with 10,479 attack attempts recorded in a single week originating from a just “single malicious IP address.”
Furthermore, a significant portion of organizations, specifically 35%, are found to be inadequately protected due to misconfigurations in their security systems, including Intrusion Prevention Systems (IPS), Web Application Firewalls (WAF), and traditional firewalls.
This attack has a global impact, with the United States experiencing the highest concentration of attacks at 33%, followed by Germany and Thailand, each at 7%. Other affected regions include Indonesia, Colombia, and the United Kingdom. The following graph depicts the attack trend over time, showcasing a surge in activity during January, followed by a decrease in February and March.
The research specifically identifies the financial sector as a primary target for these attacks. This is attributed to the heavy reliance of banks and fintech companies on AI-driven services and API integrations, which makes them susceptible to SSRF attacks that can compromise internal resources and sensitive data. Additionally, government organizations in the US have also been targeted, according to Veriti’s findings.
Video Demonstration of the Exploit
The potential consequences for financial institutions include data breaches, unauthorized transactions, regulatory penalties, and massive reputational damage. Additionally, researchers noted a critical point: “No vulnerability is too small to matter, attackers will exploit any weakness they can find.” They emphasize that overlooking medium-severity vulnerabilities can be a costly mistake, particularly for these high-value organizations.
Typically, in security practices, priority is often given to critical and high-severity vulnerabilities. However, as Veriti’s research demonstrates, attackers are opportunistic, exploiting any weakness they encounter, regardless of its severity ranking. Therefore, vulnerability prioritization should not solely rely on severity scores, as attack trends can shift rapidly, and vulnerabilities once considered insignificant can become favoured attack vectors.
Veriti has also identified a list of IP addresses actively involved in exploiting this vulnerability, providing valuable intelligence for security teams. To mitigate the risks associated with CVE-2024-27564, researchers recommend that security teams immediately review their IPS, WAF, and firewall configurations. They should also actively monitor logs for attack attempts originating from the identified malicious IP addresses and prioritize the assessment of AI-related security gaps in their risk management strategies.
UPDATE (21st March, 2025)
OpenAI has reached out to Hackread.com regarding Veriti’s recent report on CVE-2024-27564, stating that the report contains incorrect information. According to OpenAI, the vulnerability in question links to a GitHub repository from 2023 that is not related to ChatGPT’s systems or services. They have confirmed that the reported vulnerability does not affect ChatGPT and have already worked with NIST NVD to correct the issue.
We are currently reaching out to Veriti for clarification on this matter. We will update our readers as more information becomes available.