Veriti Research reveals 40% of networks allow ‘any/any’ cloud access, exposing critical vulnerabilities. Learn how malware like XWorm and Sliver C2 exploit cloud misconfigurations.
Recent research conducted by Veriti shared with Hackread.com, sheds light on the alarming trend of cybercriminals exploiting cloud infrastructure for malicious purposes. The study reveals that cloud platforms are increasingly being used not only to host and deliver malware payloads but also to serve as command-and-control centres.
A particularly concerning finding is that over 40% of networks permit unrestricted communication with at least one major cloud provider. This “any/any” configuration creates a significant security vulnerability, allowing attackers to easily exfiltrate data and deploy malware from seemingly trusted cloud sources.
Veriti’s research highlighted specific instances of malware campaigns leveraging cloud storage. The most noteworthy instances include the XWorm malware’s utilization of Amazon Web Services (AWS) S3 storage to distribute its malicious executables. Similarly, a Remcos campaign employed malicious RTF files, exploiting known vulnerabilities, with payloads also hosted on AWS S3.
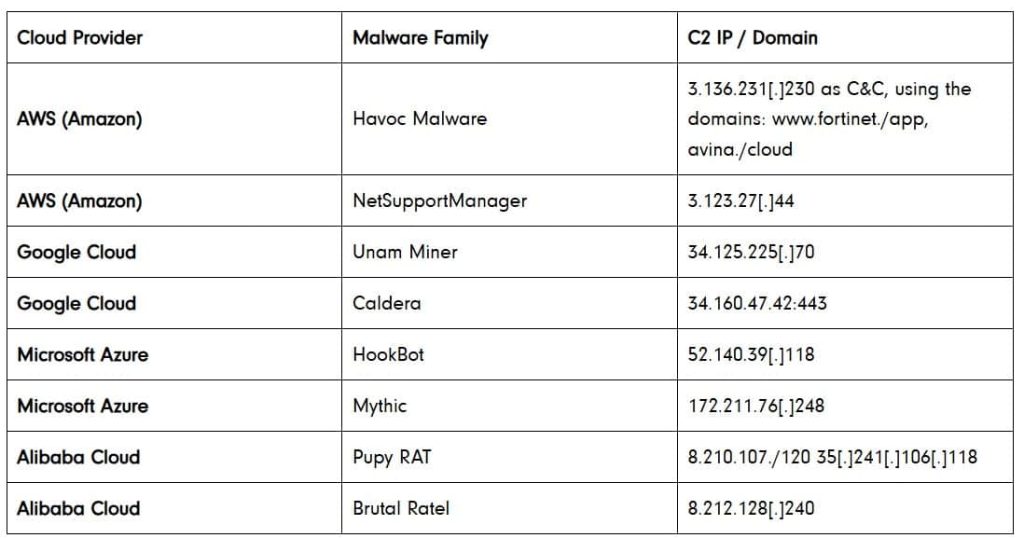
Beyond malware distribution, cloud platforms are being actively used as command-and-control (C2) servers. Various malware families, including Havoc, NetSupportManager, Unam Miner, Mythic, Pupy RAT, Caldera, HookBot and Brutal Ratel, were observed utilizing infrastructure from major cloud providers like AWS, Google Cloud, Microsoft Azure, and Alibaba Cloud for C2 operations.
Researchers also documented malware strains commonly found in cloud-based attacks, such as Mirai and njRAT, further emphasizing the growing abuse of cloud environments. Another concerning development is the increasing use of Sliver C2, which is being weaponized by Advanced Persistent Threat (APT) groups for stealthy C2 operations and post-exploitation tactics, Veriti’s report revealed.
For your information, Sliver C2 is an open-source command-and-control framework, initially developed for penetration testing but is now being weaponized by threat actors. It is often used with Rust-based malware to establish backdoors and exploits zero-day vulnerabilities, including recent Ivanti Connect Secure and Policy Secure vulnerabilities.
Furthermore, the study revealed critical vulnerabilities affecting cloud-hosted services across AWS, Azure, and Alibaba Cloud. These vulnerabilities, identified by CVE numbers, highlight the need for organizations to adopt a proactive approach to cloud security.
The increasing abuse of cloud services demands a shift towards a security-first approach to protect against these evolving threats, researchers noted.
“Veriti Research’s findings emphasize the critical need for organizations to rethink cloud security strategies. The increasing abuse of cloud services for malware hosting, C2 operations, and exploitation calls for a proactive, security-first approach,” the report read.
This should include restricting “any/any” network rules, implementing cloud-native security solutions for threat monitoring, and enforcing stronger cloud security policies.