A global phishing campaign is underway, exploiting a legacy Microsoft authentication system to steal user credentials and bypass multi-factor authentication (MFA), targeting over 150 organizations.
A sophisticated phishing campaign is exploiting vulnerabilities in Microsoft’s Active Directory Federation Services (ADFS) to compromise user accounts and bypass multi-factor authentication (MFA), as revealed in research by Abnormal Security.
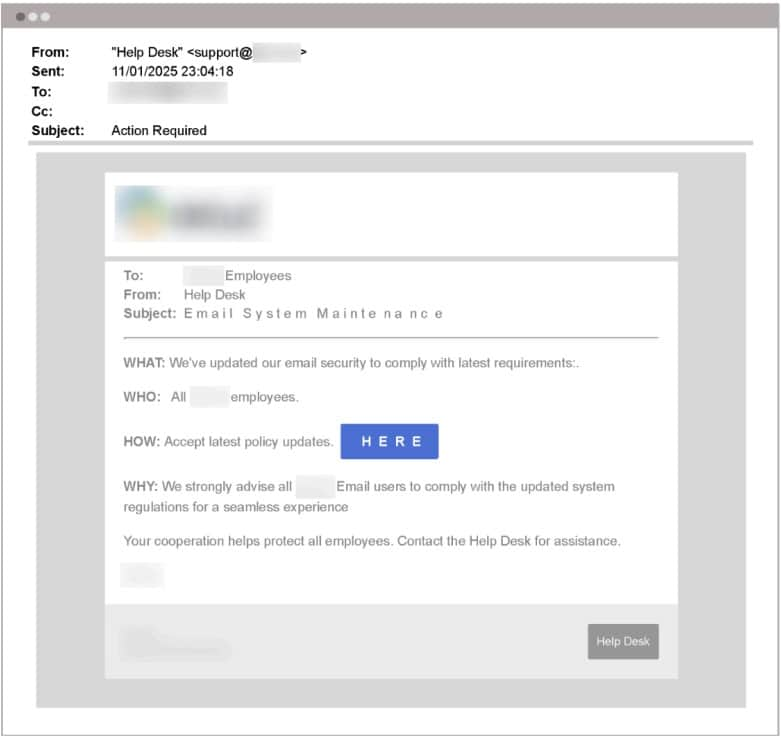
The attackers employ a combination of social engineering and technical manipulation. Phishing emails, mimicking legitimate notifications, lure victims to spoofed ADFS login pages. These emails often use urgent tones, warn of supposed updates or policy changes, and incorporate legitimate branding, logos, and even contact information to appear genuine.
URL obfuscation and shortened links further conceal the malicious destination. It is worth noting that the attackers personalize the phishing pages to match the target organization’s specific MFA setup, such as tailoring prompts for push notifications, and mechanisms like Microsoft Authenticator, Duo Security, and SMS verification.
The phishing landing page replicates the organization’s ADFS portal, dynamically pulling logos and design elements, creating a convincing counterfeit. While some client-side validation might exist, the page does not verify credentials against the organization’s systems since any username and password combination is accepted.
The next step involves capturing the user’s second-factor authentication. Phishing templates are designed to collect various MFA factors, including codes from authenticator apps, SMS messages, or even push notifications. This information, coupled with the stolen credentials, is relayed to the attackers.
To complete the deception, the victim is redirected to the genuine ADFS login page after submitting their information, reinforcing the illusion of a successful login. With the stolen credentials and MFA details, the attackers proceed with account takeover (ATO), often using VPNs to mask their location. Post-compromise activity typically includes internal reconnaissance, setting up mail filter rules to conceal their presence, and launching lateral phishing attacks.
Lateral phishing, sent from the compromised account, leverages established trust relationships within the organization. These emails often mimic legitimate communication patterns, targeting colleagues and associates. The mail filter rules, often with deceptive names and obfuscated keywords (e.g., “Hish” for “Phish”), help the attackers remain undetected.
“This approach leverages nuanced psychological tactics to exploit human vulnerabilities and reinforce a false sense of legitimacy,” Abnormal Security’s report read.
Research reveals that this campaign has targeted over 150 organizations in various sectors. The education sector is most impacted with 50% of attacks followed by healthcare (14.8%), government (12.5%), technology (6.3%), and transportation (3.4%). Geographically, the attacks are largely focused on the United States, but incidents have also been reported in Canada, Australia, and Europe.
The report suggests that attackers are exploiting the fact that many organizations have not switched to Microsoft’s modern identity platform, Entra. ADF reliance is particularly prevalent in sectors with slower technology adoption, emphasizing the need for prioritizing migration to modern solutions and employing a multi-layered security approach.
Roger Grimes, a data-driven defence evangelist at KnowBe4, commented on the issue, telling Hackread.com that this is the first time they have heard about fake ADFS login pages hinting at the sophistication of this campaign.
“I’m a 36-year cybersecurity expert and author of 15 books (one on hacking MFA and over 1,500 articles. This is the first time I’ve read about fake ADFS login pages, but ADFS has been involved in bypassing MFA authentication before, so it’s not completely new to use in the hacker scene.“
“All users should use phishing-resistant MFA whenever they can,“ Roger warned. “Unfortunately, most of today’s most popular MFA solutions, including Microsoft Authenticator, Google Authenticator, Duo, push-based MFA, OTP, and SMS-based MFA are very phishable and subject to the exact type of attack reported here.“