SUMMARY
- Fake PoCs on GitHub: Cybercriminals used trojanized proof-of-concept (PoC) code on GitHub to deliver malicious payloads to unsuspecting users, including researchers and security professionals.
- Credential Theft: The attackers stole over 390,000 WordPress credentials, AWS access keys, SSH private keys, and other sensitive data from compromised systems.
- Stealth Techniques: The campaign employed methods like backdoored configuration files, malicious PDFs, Python dropper scripts, and hidden npm packages to deploy the malware.
- Phishing Campaigns: The attackers also targeted academics through phishing emails, tricking them into installing malware disguised as a fake kernel upgrade.
- Supply Chain Impact: By leveraging trusted platforms like GitHub and popular tools, the attackers exploited the software supply chain, posing risks to professionals trusting these resources.
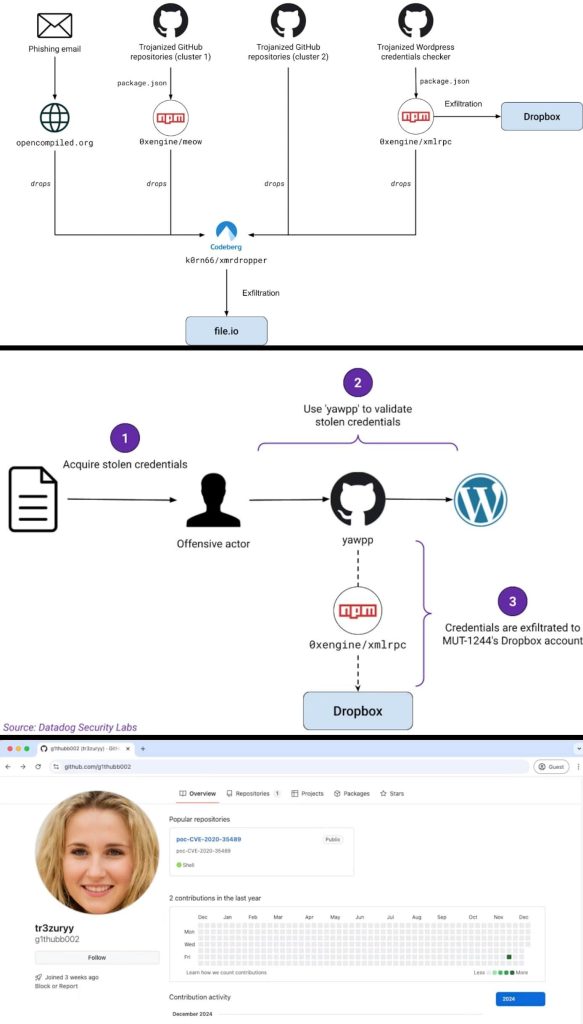
Datadog Security Labs’ cybersecurity researchers have discovered a new, malicious year-long campaign from a threat actor identified as MUT-1244, which resulted in the theft of over 390,000 WordPress credentials.
According to Datadog Security Labs’ research, the actor used a trojanized WordPress credentials checker to steal data. SSH private and AWS access keys were also stolen from the compromised systems of hundreds of victims. The attackers’ key targets included red teamers, penetration testers, security researchers, and even other malicious actors.
Use of Phishing and Trojan
Researchers observed that MUT-1244 has employed two main methods to gain initial access to victim systems including phishing and trojanized GitHub repositories.
Phishing Campaign: The campaign targeted academics, specifically those researching high-performance computing (HPC). The email urged them to install a fake kernel upgrade, leading to the download of malicious code.
Trojanized GitHub Repositories: MUT-1244 created numerous fake repositories on GitHub. These repositories disguised themselves as proof-of-concept (PoC) codes for known vulnerabilities. However, they contained hidden malicious code that infected victims who downloaded and ran them.
Fake PoCs: A New Yet Familiar Weapon
It is worth noting that the use of fake PoCs has emerged as a new weapon for cybercriminals to target cybersecurity researchers and unsuspecting users. In June 2023, scammers were caught impersonating real cybersecurity researchers to spread malware disguised as PoCs on GitHub and X (formerly Twitter).
In July 2023, a similar campaign was discovered in which fake GitHub repositories were used to distribute malware posing as PoCs. Interestingly, the stolen identity used in that attack belonged to Shakhriyar Mamedyarov, an Azerbaijani chess grandmaster.
By September 2023, another malicious campaign surfaced, utilizing a fake proof-of-concept script to trick researchers into downloading and executing a VenomRAT payload. This attack exploited the WinRAR vulnerability (CVE-2023-40477).
Techniques used in the trojanized repositories:
The techniques used in the trojanized repositories included multiple methods to hide and deliver malicious payloads. Some repositories contained legitimate exploits but hid malicious code within lengthy, backdoored configuration files.
In other cases, the malicious code was embedded inside PDF files; once opened, the fake exploit would extract and execute the hidden payload. A few repositories employed Python dropper scripts to decode base64-encoded payloads, write them to disk and execute them.
Additionally, some repositories indirectly infected victims by incorporating malicious npm packages into their code, which then downloaded and executed the attacker’s payload.
The ultimate goal of these attacks was to steal sensitive information from victims, including private SSH keys, AWS credentials, and command history. Moreover, research revealed the malicious code contained hardcoded credentials for Dropbox and file.io services. These credentials allowed the attacker to access and download the stolen data from infected machines.
390,000 WordPress Credentials
Another shocking disclosure was the attacker’s ability to access over 390,000 WordPress credentials. Researchers believe these credentials were originally obtained by other malicious actors and subsequently compromised when the attackers used a trojanized tool called “yawpp” to validate them.
“We assess with high confidence that before these credentials were exfiltrated to Dropbox, they were in the hands of offensive actors, who likely acquired them through illicit means,” Datadog’s report read.
Yawpp was advertised as a legitimate WordPress credentials checker, making it a perfect lure for attackers unaware of its malicious nature. Nevertheless, the MUT-1244 campaign shows that cybercriminals are finding new ways to trick users, making it vital for individuals to improve their skills. This is especially true for employees with cybersecurity training, as staying alert can help prevent risks to themselves and their organizations.
Experts Comments
Casey Ellis, Founder and Advisor at Bugcrowd, a San Francisco, Calif.-based leader in crowdsourced cybersecurity commented on the issue stating, “Targeting red-teamers and security researchers through fake POCs is a troll technique as old as security research itself, however, as this attack demonstrates, it can also be an effective approach to watering-hole attacks.“ Casey added, “This is a good reminder for those who provide offensive security services that they themselves are part of an exploitable supply-chain, and that malicious attackers know this.“