Argentina’s immigration agency network was compromised with NetWalker ransomware.
Border crossings in Argentina were temporarily shut down after computer networks at the regional offices of Dirección Nacional de Migraciones, the Argentinean immigration agency, were attacked with ransomware. The hackers were demanding $4 million in Bitcoin.
The attack occurred on 27 August, and Unidad Fiscal Especializada en Ciberdelincuencia, the cybercrime agency of Argentina, was immediately notified. Authorities later identified the hackers as NetWalker ransomware operators.
“(The team) realized that it was not an ordinary situation, and evaluated the Central Data and Distributed Servers infrastructure, noting the activity of a virus that had affected the system’s MS Windows-based files (mainly ADAD SYSVOL and SYSTEM CENTER DPM) and Microsoft Office files (Word, Excel, etc.) in users’ jobs and shared folders,” said the complaint.
NetWalker is a ransomware operation that mainly targets corporate computer networks and encrypts all Microsoft applications, including MS Office. After encrypting all the data available on the victim’s system, the attackers demand a ransom to exchange the password.
Argentinean news service Infobae reported that the attack caused all country border crossings to shut down for almost four hours. During this time, the authorities shut down all the computer networks used at their regional offices and checkpoints.
See: Revil hackers hit State Bank of Chile with ransomware attack
The agency filed a criminal complaint stating that Netwalker ransomware hackers stole sensitive data after launching the attack. After successfully encrypting data, the hackers sent a ransom note to the immigration agency, with a link redirecting to a Tor payment page. The message read:
“Your files are encrypted…. The only way to decrypt your files is buy the decrypter program.”
Here’s a full preview of the ransom note:
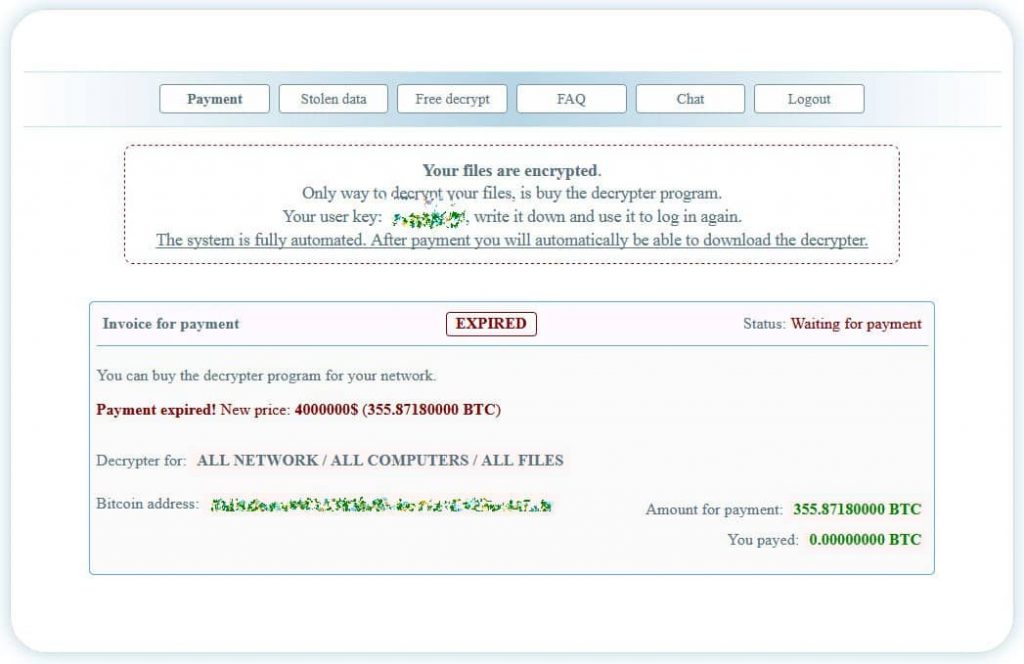
To prove their claims, hackers posted a batch of sensitive data they stole from the agency’s computers. Initially, the hackers demanded a $2 million payment for restoring the servers.
The agency did not give in to their demand for ransom. Therefore, after negotiating for one week, hackers increased the ransom amount to $4m or 355.8718 BTC. The authorities further stated that they aren’t concerned about recovering the data, but will continue to negotiate with the hackers.
See: Ransomware Hits Leading US Medical Debt Collector R1 RCM Inc.
Data theft is a common practice in around 1 in 10 ransomware attacks, while the number of ransomware groups is steadily growing. This is a worrisome development, hinting that such incidents will most likely become common in the near future.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.









