SUMMARY
- AppLite Trojan: A new, stealthy banking trojan targeting Android devices, capable of stealing banking credentials, crypto wallets, and sensitive data.
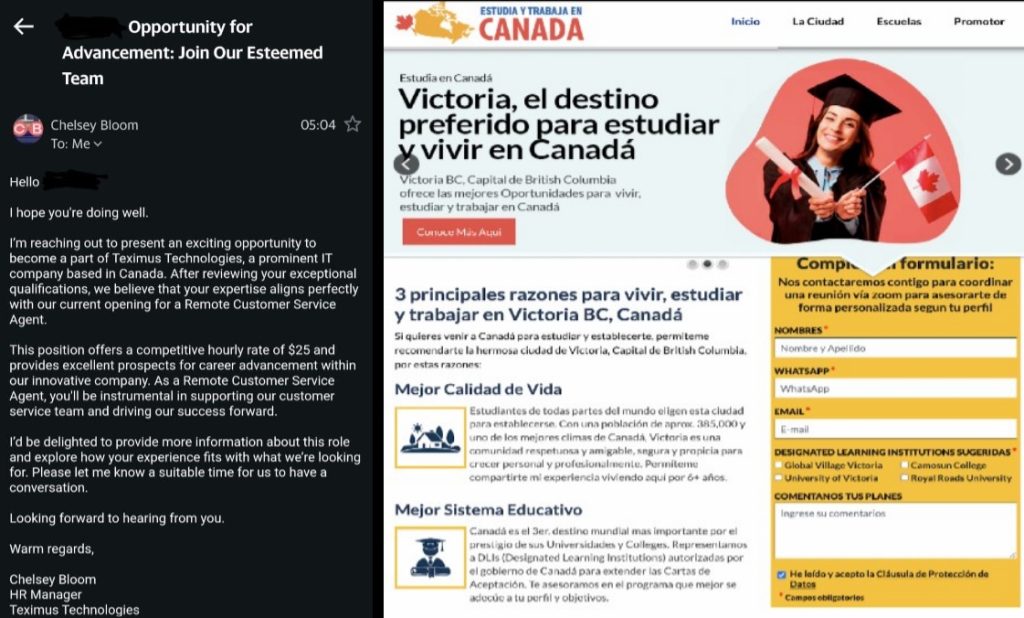
- Phishing Campaign: Delivered via fake job offer emails mimicking HR teams from reputable companies, tricking victims into downloading malware.
- Advanced Capabilities: AppLite intercepts SMS, logs keystrokes, captures screenshots, and bypasses two-factor authentication.
- Evasion Tactics: Employs obfuscation, dynamic behavior changes, and command-and-control updates to avoid detection.
- Safety Measures: Avoid suspicious links, download apps only from trusted sources, and keep devices updated with strong security protocols.
Zimperium’s zLabs has shared its latest research with Hackread.com, ahead of its publishing on December 10. According to their research, millions of job seekers are unknowingly falling victim to a new wave of mobile-targeted phishing (mishing) campaign. Report author Vishnu Pratapagiri explained that cybercriminals are targeting individuals seeking new opportunities by sending fraudulent emails disguised as job offers from HR teams at well-known companies.
This highly sophisticated mobile phishing campaign involves distributing a new variant of the dangerous Antidot banking trojan. This new strain, dubbed AppLite by Zimperium researchers, targets unsuspecting victims through cleverly crafted job offer emails.
Further probing reveals that AppLite is a particularly dangerous variant of the Antidot banking trojan. It’s designed to target mobile devices, primarily Android, and can steal sensitive information, including banking credentials and cryptocurrency wallet details.
For your information, in March 2024, Cyble researchers discovered an Android malware strain called “Antidot,” which disguised itself as a fake Google update and distributed through phishing campaigns, including SMSishing. Once installed, it stole sensitive banking information.
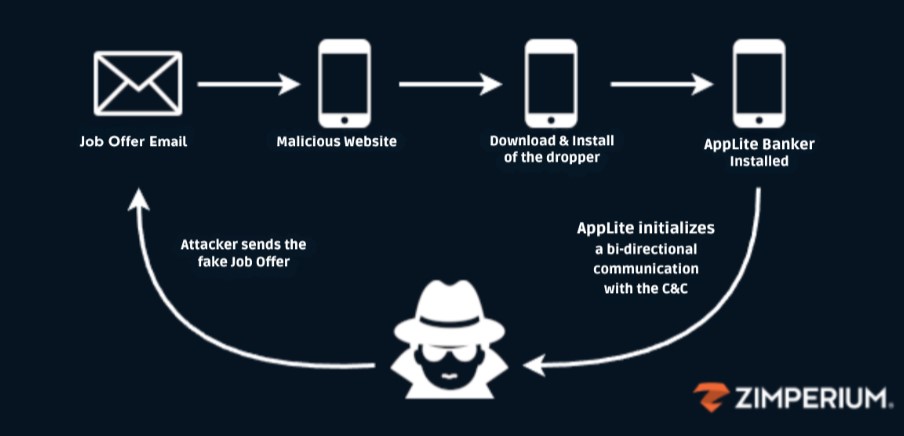
The attack begins with a well-crafted phishing email that mimics a job offer from a reputable company sent by the attackers posing as legitimate recruiters or HR representatives from the organization. Victims are tricked into visiting a legitimate job application page and downloading a seemingly harmless application, which acts as a dropper for the actual malware.
“In a subsequent communication, the threat actors direct victims to download a purported CRM Android application. While appearing legitimate, this application functions as a malicious dropper, facilitating the deployment of the primary payload onto the victim’s device,” researchers noted.
When this malicious app is installed, it secretly downloads and installs the AppLite trojan, which then requests extensive permissions, including Accessibility Services to get full control over the device.
AppLite’s capabilities are extensive. It can intercept SMS messages, log keystrokes, capture screenshots, and even control the device’s camera and microphone. It can also intercept two-factor authentication codes and steal sensitive information from banking and cryptocurrency apps.
The malware’s developers have implemented several techniques to evade detection. It uses obfuscation techniques to hide its malicious code and can modify its behaviour to adapt to different security measures. Additionally, it leverages a command-and-control server to receive updates and instructions from the attackers.
To stay safe, it is crucial to stay cautious when downloading apps, especially from unknown sources. Be wary of unsolicited emails and messages, and avoid clicking on suspicious links or downloading attachments. Keep your device’s operating system and security software up-to-date, and enable strong password protection and two-factor authentication.