A massive collection of compromised data, dubbed “ALIEN TXTBASE,” has been integrated into the Have I Been Pwned, (a website that alerts users about data breaches) database.
According to Have I Been Pwned’s founder Troy Hunt, this information was harvested from individuals whose devices were infected with infostealer malware designed to steal personal data. This addition comprises 1.5 terabytes of stolen credentials, containing 23 billion entries.
Analysis of this data reveals 493 million unique email and website combinations, impacting 284 million individual email addresses. Furthermore, 244 million previously unknown passwords have been added to the Pwned Passwords database, with updated frequency counts for another 199 million existing entries.
In addition to expanding the database, HIBP has introduced new APIs to enhance data accessibility for organizations. These APIs allow querying of stealer logs by email and website domain, enabling assessments of workforce exposure and identifying compromised customer credentials. These tools are available through a Pwned 5 subscription, which includes an API for email search and a free web UI for email log viewing. A new “IsStealerLog” flag is added for differentiated handling of stealer log data.
“This means that anyone programmatically dealing with data in HIBP can now easily elect to handle stealer logs differently than other breaches,” Hunt explained.
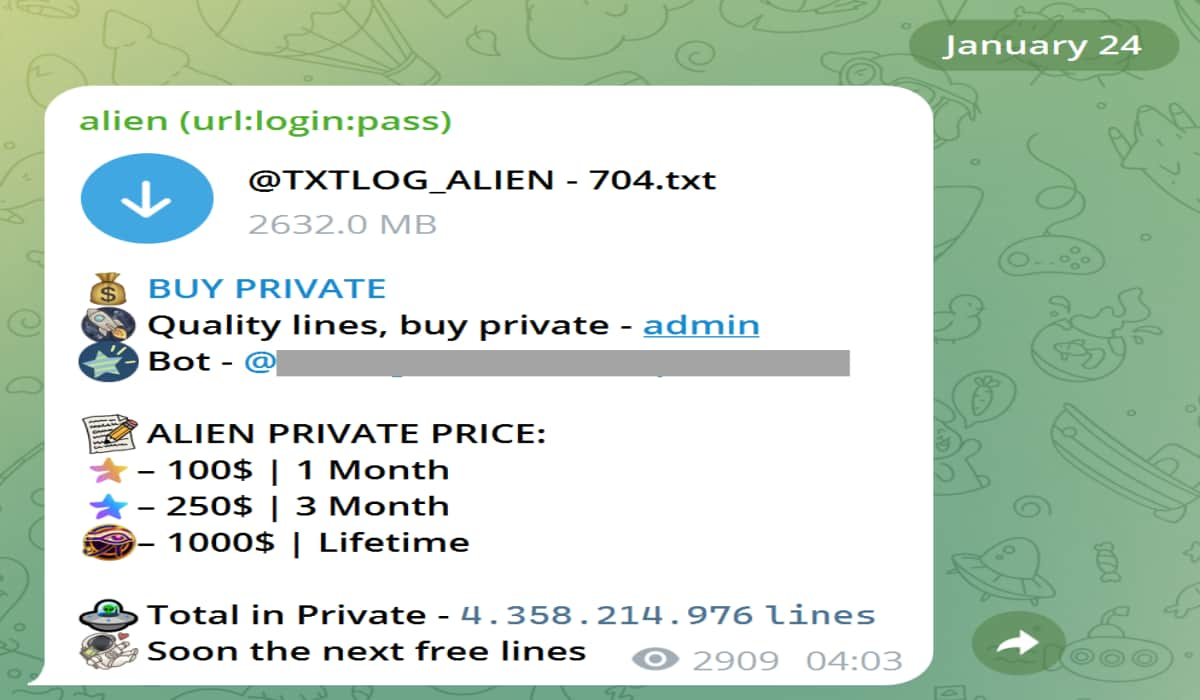
The ALIEN TXTBASE data originated from a Telegram channel distributing stolen credentials. This channel, one of many involved in such activities, came to light after a government agency alerted HIBP to its existence.
“The file in the image above contained over 36 million rows of data consisting of website URLs and the email addresses and passwords entered into them.”
The data is disseminated in individual files, a sample of which reveals the channel’s monetization strategy: offering free samples and then selling subscriptions for access to newly acquired stolen data. These credentials are typically obtained through malware infections, often spread via pirated software or disguised within seemingly legitimate downloads. Once a machine is compromised, the malware silently harvests user credentials as they are entered into websites, enabling further exploitation.
Unlike breaches from single sources like a specific website, the ALIEN TXTBASE breach involved credentials from a multitude of sites, making it challenging to verify their authenticity, Hunt noted.
Standard verification methods like password resets are complicated by geo-fencing implemented by some services, such as Netflix’s geo-restrictions. HIBP uses VPNs to verify compromised accounts, and direct contact with its subscribers helped validate data. While the data is largely legitimate, it may contain fabricated entries, making it difficult to distinguish valid from invalid information.
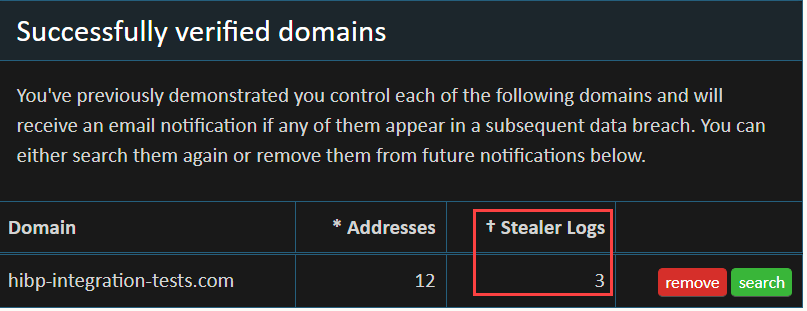
The ALIEN TXTBASE stealer logs are now accessible through existing HIBP search methods, along with the newly introduced domain-based APIs. This data empowers organizations and individuals to identify compromised credentials and take proactive steps to protect themselves. HIBP emphasizes that the free web UI for viewing stealer log results by email remains available. Users can access this feature by visiting the notification page and verifying their email address.








yeah thats cool and all, but haveibeenpwned dosent show WHICH website the account was linked to, only that it was part of the infostealer. So if you have same diffrent pw in diffrent places but same mail, you wont know which one was leaked in this entry……