In a major discovery, cybersecurity researchers at Kaspersky Securelist have found a new espionage activity targeting government offices across Southeast and East Asia. The campaign, which likely began in February 2025, uses a rootkit to hide deep inside a computer’s core, making it invisible to standard security tools.
Kaspersky links the attack to a group known as HoneyMyte (aka Bronze President or Mustang Panda). According to their analysis, the hackers are specifically targeting Myanmar and Thailand using a malicious driver file named ProjectConfiguration.sys.
Bypassing the Digital Guard
As we know it, most antivirus programs scan for suspicious files on the surface. However, they fail to identify this attack because the driver registers as a mini-filter, a tool that sits deep in the system’s traffic control.
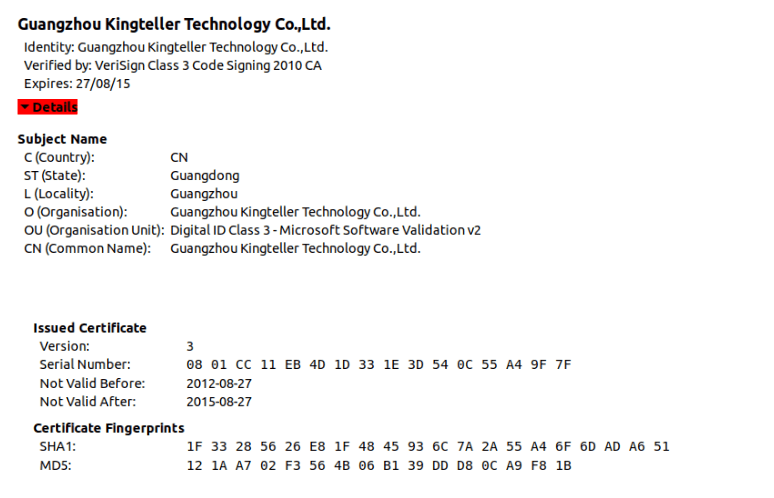
To look legitimate, the hackers used a stolen digital certificate from Guangzhou Kingteller Technology (Serial: 08 01 CC 11 EB 4D 1D 33 1E 3D 54 0C 55 A4 9F 7F), which, although expired in 2015 but still helps the malware bypass internal warnings.
To further hide its tracks, the driver uses dynamic resolution, a technique that scrambles its internal code so security software can’t easily understand what it’s doing. Further probing revealed the driver is incredibly stubborn. If an antivirus tries to delete or rename it, the driver simply blocks the action. It even “blinds” Microsoft Defender by tampering with its “altitude” settings. This basically allows the malware to sit “below” the antivirus in the system, intercepting commands before the security software even sees them, the blog post explains.
The ToneShell Backdoor
The ultimate goal of this intrusion is to drop a spy tool known as the ToneShell backdoor, which acts as a secret gateway for hackers to steal files, download data, or run remote commands.
A noteworthy finding is that the group registered their control servers (avocadomechanism.com and potherbreference.com) via NameCheap back in September 2024, months before the actual attacks began.
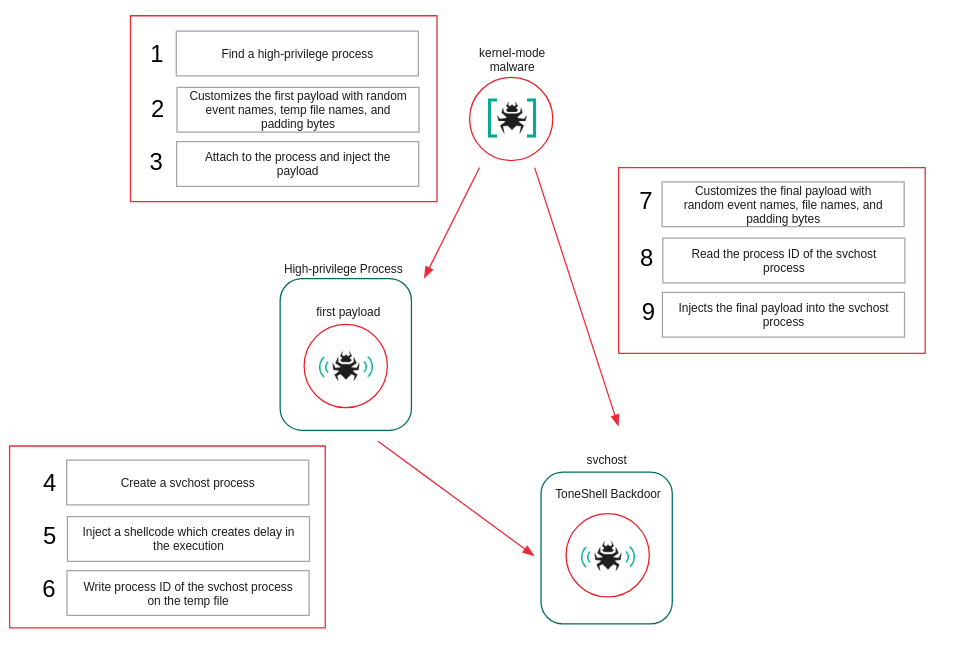
“This is the first time we’ve seen ToneShell delivered through a kernel-mode loader,” researchers noted, explaining that it gives the spy tool a high level of protection from being caught.
During the attack, the driver delivers two payloads: first, it creates a “host” process (svchost) to act as a decoy, and then it injects the ToneShell backdoor into that process. To keep their communication secret, ToneShell uses a Fake TLS trick, mimicking the markers of secure TLS 1.3 traffic.
Interestingly, most victims were already infected with older HoneyMyte tools like the ToneDisk USB worm or PlugX. Because the malware runs entirely in the computer’s memory and uses shellcodes to protect its own processes, it is very hard to detect. Therefore, Kaspersky researchers recommend deep memory audits and careful monitoring of network traffic to catch these fake connections.