New zero-day attack bypasses antivirus, sandboxes, and spam filters using corrupted files. Learn how ANY.RUN’s sandbox detects and combats these advanced threats.
A new zero-day attack campaign has surfaced, leveraging corrupted files to slip past even the strongest security protection. Recently identified by cybersecurity researchers at ANY.RUN, this attack demonstrates how sophisticated modern cyber threats have become.
By bypassing antivirus software, sandbox environments, and email spam filters, these malicious files reach their targets with alarming efficiency. Let’s dive deeper into the details of this attack, explore why it’s so effective, and uncover how it can be identified to prevent further damage.
New Zero-Day Attack Overview
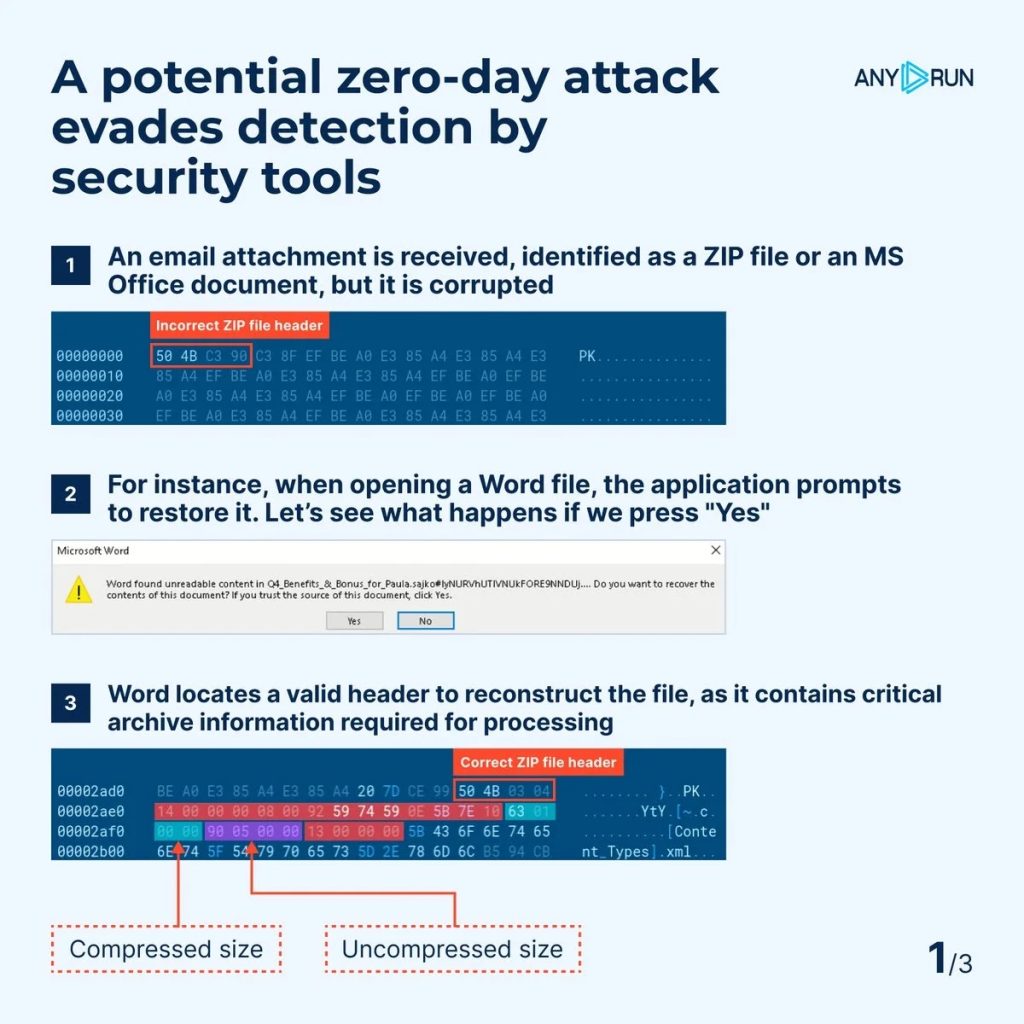
According to ANY.RUN research, this zero-day attack campaign has been active since at least August 2024. The research has uncovered that attackers are employing a unique technique: deliberately corrupting files to evade detection.
These corrupted files, often disguised as ZIP archives or Microsoft Office documents like DOCX, bypass traditional security measures by exploiting gaps in standard file-handling procedures.
Despite appearing damaged, the files remain fully functional, executing malicious code when opened in their intended programs. Here’s what makes this approach particularly dangerous:
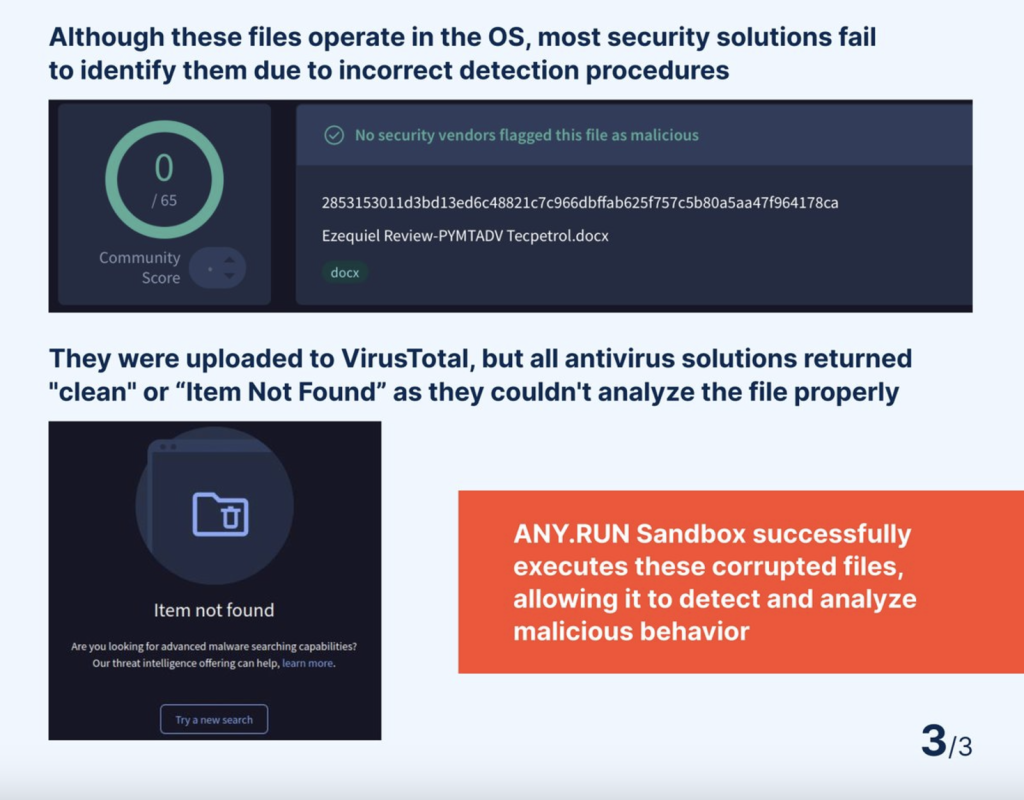
- Antivirus evasion: Traditional antivirus solutions struggle to scan corrupted files properly. As a result, many classify these files as clean or return a “not found” error.
- Sandbox resistance: Many static analysis tools fail to process these files because their corrupted structure prevents accurate identification.
- Spam filter bypass: Even Outlook’s robust spam filters can’t block these malicious emails, allowing the payload to slip straight into inboxes.
As a result, the corrupted files execute successfully on the victim’s operating system, remaining invisible to most defences.
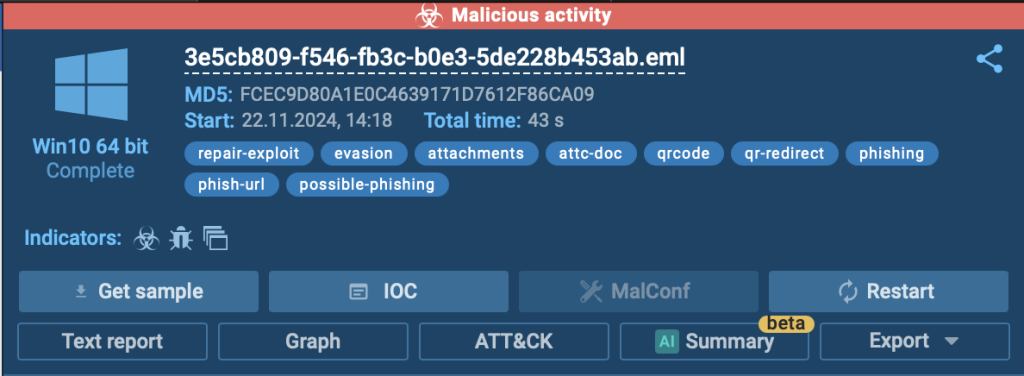
However, ANY.RUN’s interactive sandbox was able to overcome these challenges and detect malicious activity. Unlike other security tools, the sandbox dynamically analyzes corrupted files by interacting with them in real time. This allows it to uncover their true behaviour and accurately identify them as threats.
In the following analysis session, the sandbox successfully detects the threat and labels it as malicious activity, thanks to its automated interactivity feature. This advanced capability launches the corrupted files in their corresponding programs, allowing the sandbox to observe and identify malicious behaviour that traditional tools might overlook.
| Analyze cyber threats with ANY.RUN’s sandbox! Get 3 free ANY.RUN licenses this Black Friday! |
How the Zero-Day Attack is Executed
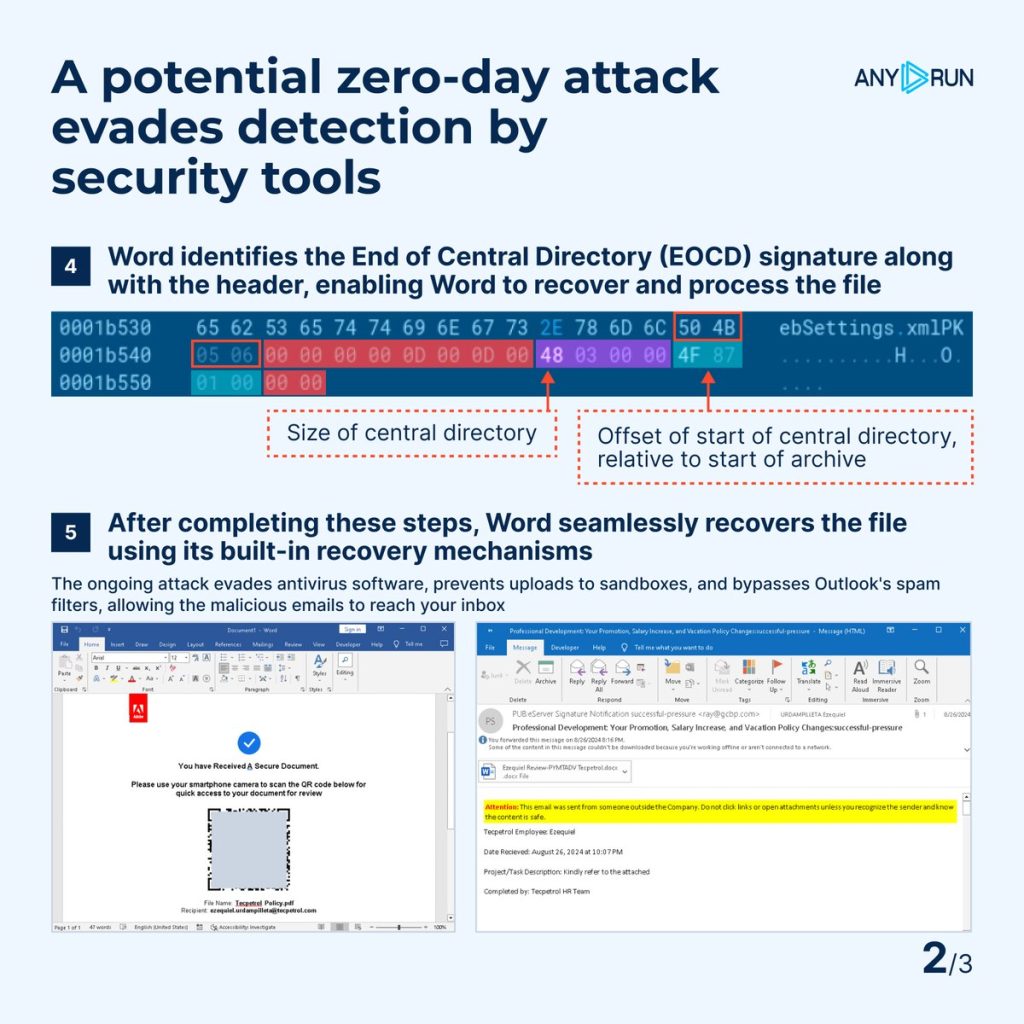
During this cyberattack campaign, attackers exploit user applications’ built-in recovery mechanisms to restore and execute damaged or corrupted files. Below you can find more details about these steps:
The analysis session revealed a corrupted file delivered via email, slipping past traditional detection systems. Security tools struggled to process the file, leaving it undetected.
However, ANY.RUN’s sandbox took a different approach by opening the file in its intended application. When built-in recovery features, like Microsoft Word’s repair mechanism, were activated, the malicious payload executed as expected.
The sandbox’s interactivity enabled it to identify this behaviour and flag the file as malicious, demonstrating its effectiveness in detecting threats that evade traditional tools.
Get Your Black Friday Deal from ANY.RUN
Combat advanced cyber threats like corrupted file attacks with ANY.RUN’s interactive sandbox. Its Automated Interactivity launches and analyzes even the most elusive files, revealing malicious behaviours that traditional tools miss.
With ANY.RUN, you can uncover the full picture of complex cyberattacks and protect your systems effectively. This Black Friday, take advantage of exclusive offers and strengthen your protection. Hurry, offers end December 8:
- For individual users: Get 2 licenses for the price of 1.
- For teams: Enjoy up to 3 licenses + an annual basic plan for Threat Intelligence Lookup, ANY.RUN’s extensive threat intelligence database.
See all offers and test the service with a free trial today →