You know about cyber security and mobile network vulnerabilities. You’ve heard of DDoS attacks. You might have even moved on from your petsname123 password.
Reports show, however, that around one in three organizations have willingly sacrificed mobile device security for business performance. Although we’ve heard of these risks, their intangibility and a seeming lack of easy solutions mean we’re probably not doing enough to protect our company’s valuable data.
But hassle-free solutions are out there, so let’s break down what the real risks to our mobile security and discover what we can do to protect ourselves and the companies we work for.
Fake and vulnerable public networks
You’re on a business trip waiting to board your flight but you’ve got no signal. You need to send an email so you access the airport’s free wifi which asks you to create an account.
What you might not realize is that fake public networks can be set up to trick you into revealing your email and password. Once malicious actors have this information they can use it to access other accounts, especially if like many you’re using the same login details across a number of platforms. Now someone has access to your company’s systems.
Although we know that using a randomized password manager is crucial to online security, few businesses take up this recommendation.
Even if the public network is legitimate, it’s still a risk to access a public network with a device carrying company data. That’s because you become vulnerable to so-called “man-in-the-middle” attacks.
These attacks happen when hackers position themselves between the users of the public network and the connection point, intercepting your data and harvesting information.
Luckily, with more businesses cottoning on to mobile device vulnerabilities, there’s a growing number of security technologies that offer protection by anonymizing your device.
FirstPoint is an excellent solution for securing mobile devices that don’t install any software or hardware, operating instead at the cellular level. It’s fully agent-less, so it will automatically protect your personal and corporate information from the full array of attacks over the cellular network, including surveillance, sabotage, and data hacking.
Phishing & SMishing
We’re savvy enough by now not to click on the link in that dodgy email saying you won the lottery, but cybercriminals are getting better by the day at tricking us into revealing our data.
According to CSO, we’re much more likely to click on suspicious links on our smartphones rather than desktops.
It makes sense, since we’re often less attentive when on the go and using a mobile device. Couple that with smaller screens and increased email access and you’ve got yourself some phishy business.
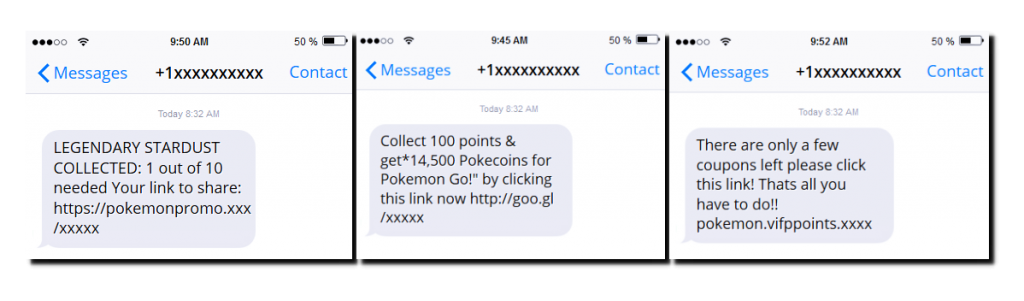
What’s worse is that cases of phishing via SMS are now becoming common. SMishing can take the form of text messages providing a dodgy link for you to click on or even directing you to make a call responding to an emergency. These scammers play on your emotions and once you’ve called the number, it’s not so difficult for fraudsters to trick you into giving up sensitive information.
It’s wise to make sure that all of your employees are trained to identify these risks. Ensure everyone in your company is trained to never click on a link sent by an unknown party, and to never call unknown numbers sent via text.
It’s also advisable to check whether emails and texts have really been sent by the company you believe it to be. Hackers will often send emails resembling legitimate companies, phishing for you and your employees to enter private account details. Remember to look out for low-resolution company logos and barely noticeable spelling mistakes in the email addresses.
Fake apps
This one is sneaky. All you wanted to do was shoot some zombies with some plants on your lunch break and now you’ve infected your work phone with malicious malware.
Once installed, fake apps that closely resemble the legitimate versions spread malware onto your device, posing a huge data security threat. Some are able to install tools that record your screen and even phone conversations, leaking both your company’s data and dinner plans with dad.
Make sure you never use third-party app stores. You even need to watch out on Google Play, which has its fair share of clones.
Anti-virus software might be the way to go. Unfortunately, with fake apps being hailed as the greatest mobile security threat of the year , there’s also been a proliferation of bogus anti-virus software that does more harm than good.
So if you do choose to use anti-virus software, make sure you opt for a reputable company. This handy guide compares the different software so you can make fully informed decisions when protecting your company’s data.






