New Backdoor ‘BugSleep’ Discovered in MuddyWater Phishing Attacks. Cybersecurity researchers uncover a custom-made backdoor used by the notorious MuddyWater hacking group to gain remote access to compromised systems. Learn about the new threat and how to protect yourself from phishing scams.
Iranian threat group ‘MuddyWater’, linked to the Ministry of Intelligence and Security, has intensified cyber warfare targeting the Middle East, particularly Israel, since the onset of the Israel-Hamas war in October 2023, reveals the latest report from Check Point Research.
For your information, MuddyWater (aka Mango Sandstorm and Static Kitten), is an infamous cyberespionage group known for using phishing emails to trick victims into clicking on malicious links or downloading infected attachments.
The group uses compromised email accounts to target various organizations in areas of interest, including Israeli municipalities, government entities, airlines, travel agencies, and journalists. MuddyWater is believed to be active since 2017.
BugSleep Backdoor – Saudi Arabia – Israel
Usually, MuddyWater’s campaigns involve the use of legitimate Remote Monitoring and Management (RMM)Tools like Atera Agent and Screen Connect, but this time they have deployed BugSleep, a custom monitoring tool with backdoor capabilities.
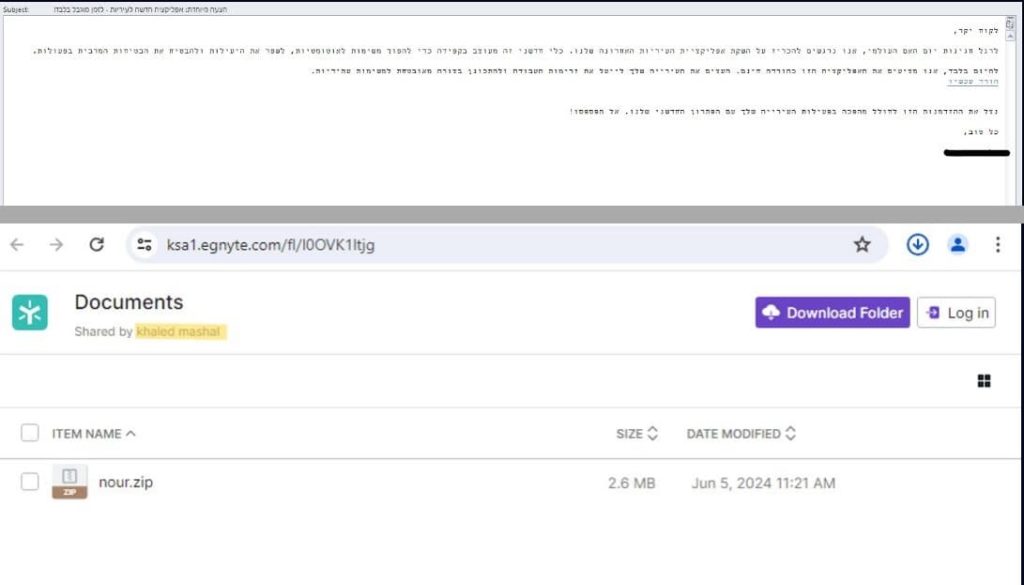
Initially, actors used a tailored lure in campaigns sent to dozens of targets in the same sector, such as municipalities, to download a new app. However, as per Check Point’s report, the group now use generic-themed phishing lures like webinars and online courses to reuse the same lure across different regions.
The group also use English more frequently now. Two emails identified by CP researchers used the same lure, one sent to Saudi Arabia and the other to Israel, with the main differences being email addresses and the final payload.
In Saudi Arabia, the payload was an RMM, while in Israel, it was BugSleep. Moreover, files related to this campaign, uploaded on VirusTotal were from IP addresses in Azerbaijan and Jordan, with the Azerbaijani language in the PDF lure allowing a correlation with the target.
BugSleep operates by first utilizing the Windows Sleep API multiple times, a tactic employed to evade detection by automated security programs known as sandboxes. It then proceeds to load the necessary functionalities required for its operation.
While the core functionality remains consistent across versions, Check Point highlights that BugSleep offers the attackers the ability to execute commands on the compromised machine and transfer files between the infected computer and a C&C server controlled by the attackers.
The malware is distributed through Egnyte, a secure file-sharing platform, and is triggered every 30 minutes daily. The updates, occurring within short intervals between samples, suggest a trial-and-error approach.
The discovery of custom-made malware demonstrates the evolving tactics of cybercriminals and MuddyWater’s commitment to bypassing traditional security measures. Therefore, it’s crucial to be cautious of unsolicited emails, verify the sender’s identity before opening them, regularly update your operating system and security software, use strong passwords, and enable multi-factor authentication whenever possible.
RELATED ARTICLES
- Iran’s Mint Sandstorm APT Hits Unis with Hamas-Israel Phishing Scam
- Iran’s Scarred Manticore Targets Middle East with LIONTAIL Malware
- Iran’s Peach Sandstorm Deploy FalseFont Backdoor in Defense Sector
- Iranian Hackers Posed as Israelis in Targeted LinkedIn Phishing Attack
- Microsoft reports two Iranian hacking groups exploiting PaperCut flaw