Group-IB has uncovered Lazarus group’s stealthy new trojan and technique of hiding malicious code in extended attributes on macOS. Learn how this advanced persistent threat (APT) is evading detection and the steps you can take to protect yourself.
Cybersecurity researchers at Group-IB report that the North Korean state-backed APT Lazarus group, is now deploying a new macOS trojan called “RustyAttr.” This malware, along with a new evasion technique, lets Lazarus carry out its operations while remaining undetected.
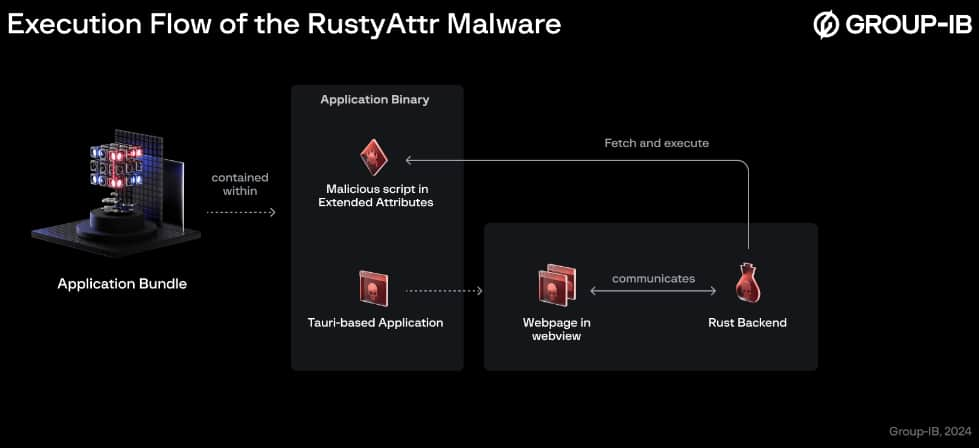
Since May 2024, the Lazarus Group has been employing a technique that hides malicious code within the extended attributes (EAs) of files on macOS systems, utilizing the RustyAttr trojan. Extended attributes are hidden data containers attached to files, enabling the storage of additional information beyond standard attributes such as size or creation date.
This method is particularly tricky because these attributes are invisible by default in applications like Finder or Terminal. However, using the .xattr command, attackers can easily access and exploit this hidden data.
In 2020, Bundlore adware used a similar technique to hide its payload in resource forks which stored structured data on older macOS systems, researchers noted in the blog post shared with Hackread.com.
The possible attack scenario involves a legitimate-looking malicious application, built using the Tauri framework. It displays fake PDF files related to job opportunities or cryptocurrency, a theme consistent with Lazarus.
For your information, the Tauri framework is a web-based tool for creating lightweight desktop applications, enabling developers to use HTML, CSS, JavaScript, and Rust for front and backend, respectively, to execute malicious scripts.
The shell scripts reveal two types of decoys: one fetches a PDF file from a file hosting service, containing questions related to game project development and funding, and the other displays a dialogue stating that the app does not support the specified version, while a web request to the staging server processes in the background. The malicious script is hidden within a custom extended attribute named “test”.
The application leverages a JavaScript file named “preload.js” to interact with the hidden script. This JavaScript code, using Tauri’s functionalities, retrieves the script from the extended attribute and executes it.
“Interestingly, the next behaviour is as follows – if the attribute exists, no user interface will be shown whereas, if the attribute is absent, the fake webpage will be shown,” the researchers revealed.
The malicious components are hidden within the extended attributes, making them invisible to antivirus scanners. The applications were initially signed with a leaked certificate (revoked by Apple now) but remained unnotarized, bypassing another layer of possible detection.
While the researchers haven’t identified any confirmed victims yet, they believe Lazarus might be experimenting with this technique for future attacks. This discovery is important because it’s a completely new tactic, not yet documented in the MITRE ATT&CK framework, a standard reference for attack techniques.
The Lazarus group’s sophistication and continuous expansion of tactics show their efforts to evade detection and compromise systems. To stay safe, verify the source and legitimacy of files before downloading or executing them, and avoid downloading harmless content like PDFs without checking even if it appears legitimate.
Keep macOS Gatekeeper on as it prevents the execution of untrusted applications. Lastly, utilize advanced threat intelligence solutions to remain aware of emerging threats and develop effective protection strategies.