KEY SUMMARY POINTS
- Focus Shift to Nuclear Industry: The Lazarus Group, linked to North Korea, has shifted its targets to the nuclear industry, marking a potential escalation from its earlier focus on defense, aerospace, and cryptocurrency.
- Fake Job Posting Tactics: Their attacks, observed in January 2024, employ fake job postings (Operation DreamJob) to deliver malicious files disguised as job assessments, gaining access to victims’ systems.
- Advanced Malware Techniques: The group uses sophisticated tools like Ranid Downloader and a novel plugin-based malware, “CookiePlus,” which operates in memory, making it harder for security systems to detect.
- Exploitation of Vulnerabilities: Lazarus continues refining its tactics, exploiting vulnerabilities like Google Chrome zero-day and leveraging innovative malware like “RustyAttr” on macOS.
- Call for Caution: The increasing sophistication and activity of the Lazarus Group underscore the need for heightened cybersecurity measures, particularly in sensitive industries.
Securelist by Kaspersky has published its latest threat intelligence report focused on the activities of the notorious Lazarus hacking group, which, as we know it, has links to the North Korean government.
According to Securelist’s research, the Lazarus Group has shifted its focus to targeting individuals within the nuclear industry lately. This indicates an upcoming escalation in their operations, as they previously concentrated on sectors like defense, aerospace, and cryptocurrency.
“We observed a similar attack in which the Lazarus group delivered archive files containing malicious files to at least two employees associated with the same nuclear-related organization over the course of one month,” the report read.
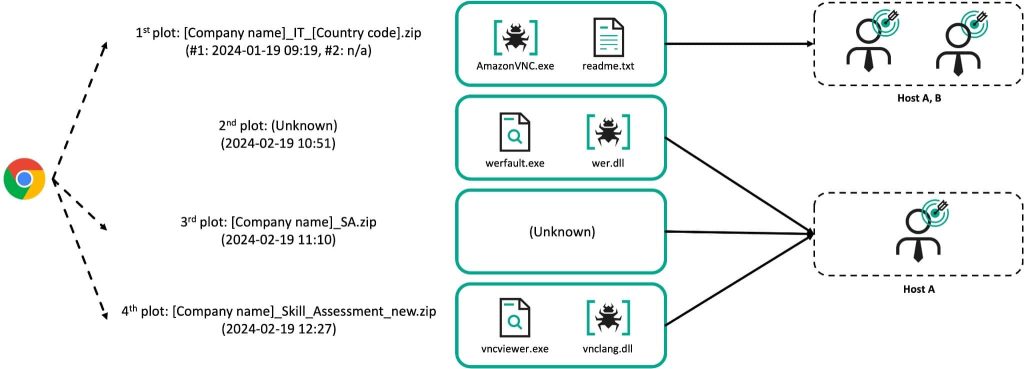
The attacks observed by Kaspersky occurred in January 2024 and followed the pattern of using fake job postings, a tactic known as the DeathNote campaign or “Operation DreamJob.”
This involves creating fake job postings and enticing potential victims with tempting career opportunities. During the “interview” process, malicious files are subtly introduced, often disguised as legitimate assessment tests.
The attack starts with an initial file disguised as job assessments for prominent companies, which contains a ZIP archive with malicious executables or trojanized legitimate tools like VNC viewers.
Once executed, the trojan prompts the victim to enter an IP address provided by the attackers via separate communication channels like messenger apps. This grants the attackers unauthorized access to the compromised machine, enabling them to move laterally within the network and potentially steal sensitive data or disrupt critical operations.
An XOR key is generated based on the IP address to decrypt the internal resources of the VNC executable and unzip the data. The unzipped data is then downloaded by Ranid Downloader, which fetches further malicious payloads like MISTPEN, RollMid, LPEClient, Charamel Loader, ServiceChanger, and CookiePlus. The payload type (DLL or shellcode) is determined by a flag within the data structure. The execution results of these plugins are encrypted and sent back to the C2 server.
A key innovation in these recent attacks is the introduction of “CookiePlus,” a novel plugin-based malware. This downloader operates primarily in memory, loading malicious payloads dynamically. This evasive technique makes it harder for traditional security solutions to detect and mitigate the threat.
The development of CookiePlus demonstrates the Lazarus Group’s continuous efforts to refine its tools and evade detection. By introducing new modular malware and adapting their tactics, they aim to maintain a persistent presence within targeted networks and achieve their objectives.
The group has been particularly active lately. In November Group-IB discovered the Lazarus group’s new trojan, “RustyAttr,” which hides malicious code in extended attributes on macOS systems and in October the group exploited a Google Chrome zero-day vulnerability to target cryptocurrency investors with a deceptive NFT game. This calls for continuous vigilance to safeguard your digital assets.