Seculert, an Israeli based company that detects viruses and other Advanced persistent threats (APT), has claimed to detect two different spear-phishing attacks which were using a fake Mandiant report to spy on Chinese and Japanese journalists.
TheRegister reports that researchers are positive about the origin of these attacks is none other then China.
“We resolved it and found it was reporting to an IP address in China with the same physical location as the previous attacks. They are up to something, Same infected PDF files.” Seculert spokesman told the media.
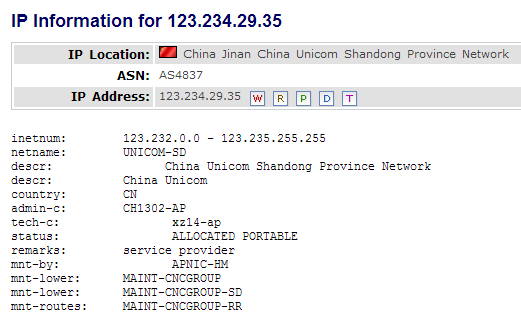
The researchers found out that a malware was trying to infiltrate into the Japanese government based website from an IP address (218.53.110.203) belonging to Korea but shocking enough for all, the IP address contacts another local IP address (123.234.29.35), which is a server located in Jinan, the capital of the Shandong province of China.
The malware was exploited as a result of recently patched Java vulnerability, sent via email in form of PDF attachment. Once the malware is downloaded and executed, it tries to download a new but a similar copy of itself and spreads like bacteria.
It is unclear who was behind this sophisticated attack, but researchers stand still on their claim and blame China for planning and conducting cyber attack against government of Japan.
However, the Chinese government had admitted to have a cyber warfare unit within the People’s liberation Army.
Via: TheRegister & Seculert