A new cyberattack campaign discovered by FortiGuard Labs, Fortinet’s threat intelligence and research unit, leverages a combination of social engineering, multi-stage malware, and the manipulation of trusted cloud services to achieve control over compromised systems.
According to FortiGuard’s investigation, shared with Hackread.com ahead of its publishing on Monday, the campaign targets Microsoft Windows users and has a high severity level. Their most crucial observation is that the attackers have innovated by integrating a modified version of the Havoc framework, Havoc Demon Agent, with the Microsoft Graph API, effectively hiding their malicious communications within the legitimate traffic of well-known cloud services.
For your information, Havoc is an open-source post-exploitation command and control framework used in red teaming exercises and attack campaigns to obtain full control of the target system.
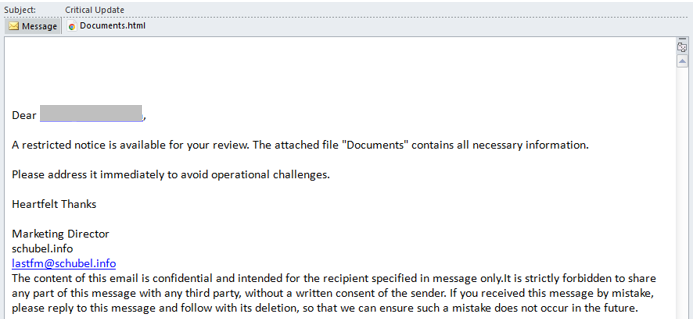
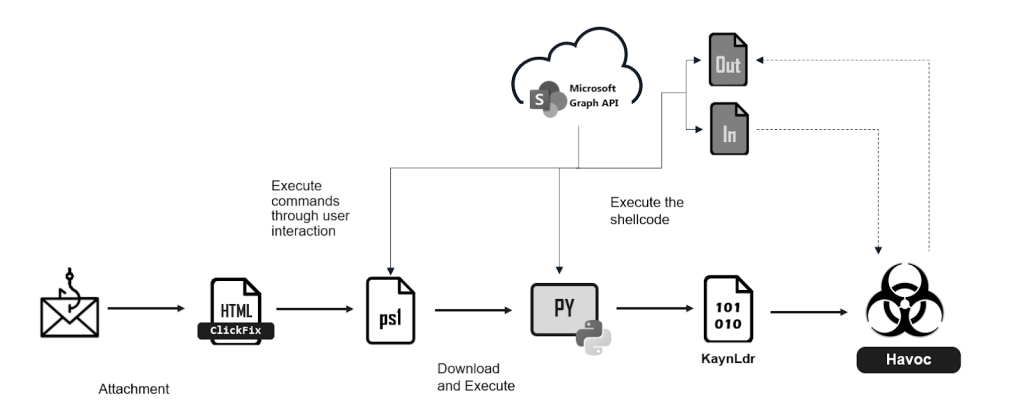
The initial point of entry for this attack is a carefully crafted phishing email, which contains an HTML attachment designed to deceive the recipient into executing a malicious PowerShell command.
Through a technique known as “ClickFix,” in which users are tricked into executing malicious commands, the attachment presents a fake error message, prompting the recipient to copy and paste a seemingly harmless command into their system’s terminal. However, this command initiates a chain of events that leads to the downloading/execution of further malicious scripts, which are strategically hosted on a SharePoint site, probably to obscure the malicious operation within a trusted cloud environment.
The initial PowerShell script performs checks to evade sandbox detection and then proceeds to download/execute a Python script, also hosted on SharePoint. This Python script acts as a shellcode loader and injects and executes a malicious DLL, KaynLdr, which reflectively loads an embedded DLL, and further complicates analysis by using API hashing.
The core of the attacker’s C2 infrastructure relies on the modified version of the Havoc Demon DLL as it leverages the Microsoft Graph API to establish communication channels that blend seamlessly with legitimate cloud traffic. The “SharePointC2Init” function within the DLL obtains access tokens for the Microsoft Graph API and creates two files within the victim’s SharePoint document library, each named with a unique identifier derived from the compromised system.
These files act as channels for transmitting victim information and receiving C2 commands, while the entire communication is handled by the modified “TransportSend” function and encrypted using AES-256 in CTR mode. The agent then parses and executes these commands, which include a wide range of post-exploitation capabilities, such as information gathering, file operations, and token manipulation.
FortiGuard Labs’s discovery highlights the evolution of open-source C2 frameworks to create new, difficult-to-detect attacks and the growing need for adopting advanced security measures against such attacks.
“In addition to staying alert for phishing emails, guided messages that encourage opening a terminal or PowerShell must be handled with extra caution to prevent inadvertently downloading and executing malicious commands,” FortiGuard’s researchers concluded.
In a comment to Hackread.com, Thomas Richards, Principal Consultant and Network and Red Team Practice Director at Black Duck, a Burlington, Massachusetts-based application security provider, noted that hackers are using trusted Microsoft services to evade detection, showing a high level of sophistication, but what stands out is that their attack method requires more manual action from the victim than usual.
“These bad actor groups aim for obfuscation so they can achieve their goals. It’s not unusual to see them use open-source frameworks, however, the use of legitimate Microsoft services shows a level of sophistication that is concerning. Using those services allows them to hide in plain sight and have the benefits of being trusted servers,“ Thomas explained. “What is surprising about this is the level of manual intervention needed on the victim for the attack to be a success. Usually with these campaigns, the bad actors want as little interaction as possible on the victim’s part aside from clicking on a link.“