Dubbed InterPlanetary Storm; the malware has been active since May 2019 but its new variant targets both macOS and Android-based devices.
Yesterday, we saw a threat group named APT-C-23 introducing a new Android variant of their malware. Turns out, they’re not the only ones being innovative.
In the latest, a research report from Barracuda reveals how a previously known malware named InterPlanetary Storm, active since May 2019 now has a new variant that targets both macOS and Android-based devices, a step ahead from only Windows and Linux based devices.
See: Monero Mining Malware Infecting Android Smart TVs & Smartphones
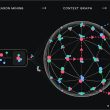
Coming to the scope of the malware, it is based on building a huge botnet that targets user machines globally in about 84 countries but predominantly from Asia. In fact, 59% of the 13500 infected machines come from only 3 countries: Hong Kong, South Korea, and Taiwan.

The rest are spread out across the world with the malware currently focusing on IoT devices allowing it to use them later for nefarious purposes such as crypto-mining, distributed denial of service (DDoS) attacks, and other vectors that make use of large scale machines.
Examples of the infected devices include televisions for Android-based ones and “routers with ill-configured SSH service” for Linux.
How it works is by attacking machines through brute-forcing SSH servers (just like LUA bot did it past) and trying to gain access to Android Debug Bridge servers as well. Furthermore, to improve upon its execution, the use of both reverse shell and bash shell was found.
See: Smart TVs make screenshots every second & send them to the server
Other features include the ability to evade honeypots, killing system processes that would threaten its running such as that of a debugger, and also auto-updating itself.
As for how the malware was named so, the researchers offer a bit of light on this:
The malware is called InterPlanetary Storm because it uses the InterPlanetary File System (IPFS) p2p network and its underlying libp2p implementation. This allows infected nodes to communicate with each other directly or through other nodes (i.e. relays).
To conclude, in order to protect yourself from InterPlanetary Storm, the researchers recommend 2 main approaches. The first one is to make your SSH servers much more secure through mechanisms such as replacing passwords with keys.
Secondly, a cloud security management tool which could help monitor the access of different users to SSH. Explaining, the researchers stated in a blog post that,
To provide secured access to shells if needed; instead of exposing the resource on the internet, deploy an MFA-enabled VPN connection and segment your networks for the specific needs instead of granting access to broad IP networks.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.