Mandiant’s investigation unveiled that the attack was part of a larger operation known as “ClinkSink,” which employed a “Drainer-as-a-Service” (DaaS) model to steal Solana cryptocurrency.
Mandiant, a renowned cybersecurity firm and Google subsidiary found itself facing the very threat it combats on January 3rd, 2024. In an ironic twist, Mandiant’s own X account (formerly Twitter) was compromised through a brute-force attack, highlighting the ever-present vulnerability of even the most well-defended systems.
The Breach: Phishing for Profits
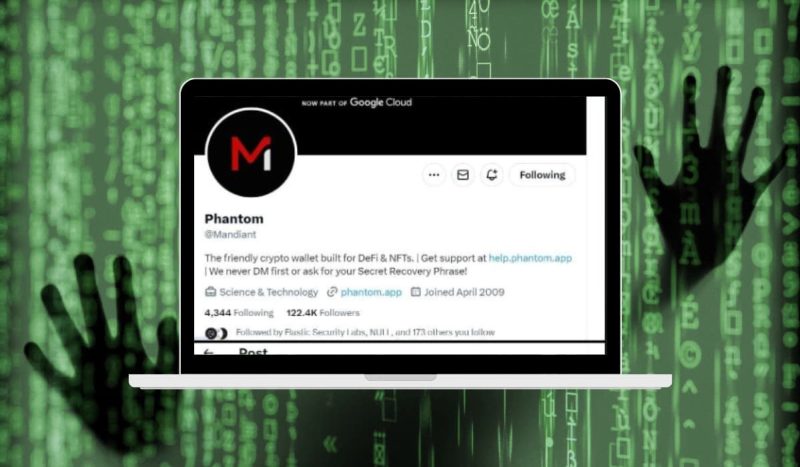
The attacker, leveraging a brute-force method, cracked Mandiant’s X account password and gained access. With control in hand, the perpetrator swiftly transformed the account into a malicious tool, spewing links to a cleverly disguised phishing webpage.
This page mimicked a legitimate X login portal, luring unsuspecting users to enter their credentials. Upon entering their information, users were unknowingly redirected to a hidden page that would siphon their cryptocurrency funds if signed in – a digital heist unfolding right under the noses of cybersecurity experts.
“On January 3, 2024, Mandiant’s X social media account was taken over and subsequently used to distribute links to a cryptocurrency drainer phishing page. Working with X, we were able to regain control of the account and, based on our investigation over the following days, we found no evidence of malicious activity on, or compromise of, any Mandiant or Google Cloud systems that led to the compromise of this account.”
Mandiant
ClinkSink: The Drain Behind the Curtain
In a commendable display of transparency, Mandiant publicly acknowledged the breach and shared its findings in a detailed blog post published on Wednesday 11, 2024. The cybersecurity giant revealed that a “weak password” was the likely culprit, emphasizing the importance of password best practices. Additionally, they confirmed that only their X account was compromised and no other systems were breached.
Mandiant’s investigation also revealed the attack was part of a larger operation dubbed “ClinkSink.” This campaign utilized a “Drainer-as-a-Service” (DaaS) model, where pre-built phishing kits and tools are readily available for purchase by cyber criminals. ClinkSink specifically targeted owners of Solana cryptocurrency, a popular blockchain platform.
According to the company, so far, malicious threat actors have stolen hundreds of thousands of dollars worth of Solana cryptocurrency assets in the recent ClinkSink drainer campaigns.
A Defender Breached: Lessons Learned
While Mandiant eventually regained control of its X account and the immediate threat was neutralized, the incident served as a harsh reality check and points out several crucial cybersecurity lessons:
- No one is invincible: Even the most secure systems are vulnerable to determined attackers.
- Password hygiene is paramount: Strong, unique passwords and robust two-factor authentication are essential defence mechanisms.
- Vigilance is key: Constant monitoring and quick response are crucial in mitigating damage from cyberattacks.
Nevertheless, this is not the first time that a cybersecurity firm fell prey to hackers or was targeted by malicious threat actors. In March 2023, a Swiss technology and cybersecurity company, Acronis, experienced a data breach, with over 21 GB of files and folders being leaked by a hacker known as Kernelware.
In February 2023, the Singapore-based Group-IB cybersecurity firm revealed that it has been constantly targeted by malicious threat actors based in the People’s Republic of China. In February 2021, the French cybersecurity company Stormshield suffered a data breach in which its source code and customer data were stolen by unknown hackers.