AT&T Cybersecurity warns of a new threat: Microsoft Teams targeted for phishing and malware attacks. Learn how to protect your organization against these evolving cyber threats.
Cybersecurity experts from AT&T Cybersecurity have uncovered a concerning trend: Microsoft Teams, the widely used collaboration platform, being exploited as a vector for phishing scams and malware attacks.
While traditional phishing via email remains a pervasive threat, the integration of External Access in Microsoft Teams has opened up a new frontier for malicious actors to exploit. For your information, External Access enables streamlined communication and collaboration with individuals outside your organization using Teams, Skype for Business, or Skype.
In a recent incident reported by AT&T Cybersecurity’s Managed Detection and Response (MDR) team, a client raised alarms after an external user, not affiliated with their organization, initiated unsolicited Microsoft Teams chats with internal members. Suspicions were raised, and upon investigation, it was confirmed that the chats were indeed phishing lures.
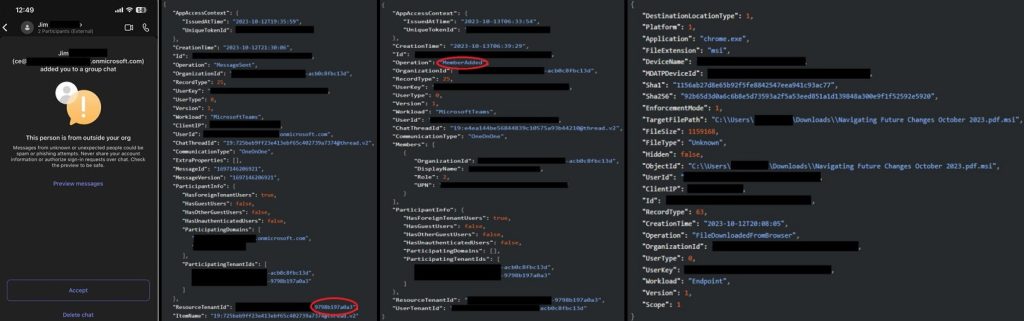
The sophistication of the attack was revealed in a blog post published on January 30, 2024, as the MDR team delved deeper into the incident. Analysis of the tactics and indicators of compromise (IOCs) employed by the attacker uncovered associations with DarkGate malware, a notorious threat in the large as well we small businesses.
The DarkGate malware first emerged on December 25th, 2017, initially functioning as a password stealer and cryptocurrency miner, primarily spreading through Torrent files. It was identified by enSilo researcher Adi Zeligson, who observed its targeting of Windows workstations.
In October 2023, DarkGate resurfaced, this time associated with threat actors based in Vietnam. Their latest campaign focused on infiltrating META accounts, particularly in India, the United States, and the United Kingdom.
As for the latest attack, the timely intervention of the MDR SOC team thwarted the attack before significant damage could occur, showcasing the importance of proactive cybersecurity measures.
Key to the investigation was the identification of suspicious activities within the Teams environment. Over 1,000 Microsoft Teams events were flagged, indicating the scope of the phishing attempt. By leveraging Microsoft 365 tenant IDs and meticulously tracing chat interactions, the MDR SOC team successfully pinpointed compromised accounts and assets for remediation.
Further examination revealed that some users had unwittingly downloaded double-extension files, a common tactic used by attackers to conceal malicious executables. Armed with this information, the client swiftly took action, initiating password resets and isolating infected assets to contain the threat.
As organizations increasingly rely on collaboration platforms like Teams for remote work, they must remain alert against emerging threats. Recommendations from AT&T Cybersecurity include considering the disabling of External Access in Microsoft Teams, unless essential for business operations, and reinforcing user training to recognize and report phishing attempts across all communication channels.









