Spyware and Google have shared a pretty close relationship of late and the recent discovery from researchers at Trend Micro further establishes the fact that no matter how hard Google tries Android spyware keeps haunting its digital offerings.
Reportedly, Trend Micro security researchers have identified a number of games and apps containing built-in spyware that can steal personal data and transfer it to malicious threat actors.
Dubbed as Mobstspy, the Android spyware is identified in utility apps and games that have been disguised successfully to appear legitimate. The spyware has information stealing and phishing capabilities. Most of the infected devices are identified in India but the spyware seems to have been distributed globally as it has managed to infect devices in around 196 countries.
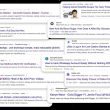
A total of 7 apps contain Mobstspy Android spyware namely:
Flappy Bird
HZPermis
Pro Arabe
FlashLight
Flappy Birr Dog
Win7Launcher
Win7imulator
One of these apps has been installed over 100,000 times.
With its phishing capabilities, the attacker can easily launch a fake login screen when the victim attempts to use his/her Google or Facebook account. Since a majority of the users cannot differentiate between fake and genuine login screens, therefore, they are bound to fall for the trap.
“If the user inputs his/her credentials, the fake pop-up will only state that the log-in was unsuccessful. At which point the malware would already have stolen the user’s credentials,” the researchers said in a blog post.
As soon as they provide their login credentials, the malware displays a failed login attempt but actually, the attackers have stolen the username and password. In case the user has enabled 2FA authentication the attacker would find it difficult to hijack the account. Luckily, both Google and Facebook offer 2FA authentication.
Mobstspy is different from other Android spyware because it steals a wide range of data from infected devices such as contacts, call logs, images, recorded voice conversations, and text messages records. It particularly looks for data from apps like Snapchat, WhatsApp, Viber, and similar call recording applications. Furthermore, Bluetooth storage location, sound directories, and camera folder are also searched by the malware.
Trend Micro researchers have located the C&C servers where Mobstspy transfers all the stolen data. There are two servers mobistartappcom, coderoutema, hizaxytvcom, and seepanocom that act as the C&C servers for the attackers.
Mobstspy delivers the information using Google’s developed Firebase Cloud Messaging system that works on Android, iOS, and web apps. After the infected app is launched on the device, the malware checks for the device’s network and then reads/parses an XML configuration file from the C&C server after which it collects the information and sends to the attackers. After delivering the data, the device starts receiving commands via the Firebase service and executes them.
“This case demonstrates that despite the prevalence and usefulness of apps, users must remain cautious when downloading them to their devices. The popularity of apps serves as an incentive for cybercriminals to continue developing campaigns that utilize them to steal information or perform other kinds of attacks. In addition, users can install a comprehensive cybersecurity solution to defend their mobile devices against mobile malware,” Trend Micro concluded.
The infected apps were available on Google Play Store in 2018 and five of them have already been suspended by Google while the last one is also not available for downloading anymore on its official marketplace. However, third-party app stores are still offering them and it is currently unclear how many users have so far been affected by Mobstspy malware.