SUMMARY
- Infoblox discovered widespread domain spoofing in spam campaigns while investigating ‘Muddling Meerkat.’
- Collaboration with the cybersecurity community linked Muddling Meerkat’s DNS activities to spam distribution.
- Researchers identified multiple spam campaigns through abuse reports and domain analysis.
- Techniques included phishing with QR codes, impersonating brands, extortion, and mysterious financial spam.
- The findings show domain spoofing remains highly effective, bypassing current security measures.
In its latest report, cybersecurity firm Infoblox has revealed how scammers use domain spoofing in spam campaigns, a discovery made through a collaboration between the cybersecurity and networking community on research about the Chinese Great Firewall.
This research project was initially aimed at understanding the activities of a threat actor known as a Muddling Meerkat. Muddling Meerkat is known for conducting strange DNS operations involving fake Chinese Great Firewall responses. The researchers could not determine the ultimate purpose of Muddling Meerkat’s activities, but they did learn a lot about how domain spoofing is used in malspam.
The research team, initially perplexed by Muddling Meerkat’s activities, sought external perspectives by sharing their findings with the broader security community. One key observation pointed towards a potential connection between Muddling Meerkat’s operations and spam distribution.
Several organizations reported receiving abuse notifications for domains they owned, often internal domains with limited external exposure. These notifications indicated large-scale spam campaigns originating from Chinese IP addresses, targeting major email providers. This observation resonated with the team’s own findings, as they had previously observed Muddling Meerkat generating fake mail server (MX) records emanating from Chinese IP space.
A significant breakthrough occurred when the researchers discovered that they owned several of the “target” domains identified in the Muddling Meerkat research. By analysing abuse reports related to their own domains, leveraging their authoritative DNS server logs, and examining their internal spam collection, the researchers gained unprecedented insights into the tactics employed by spammers.
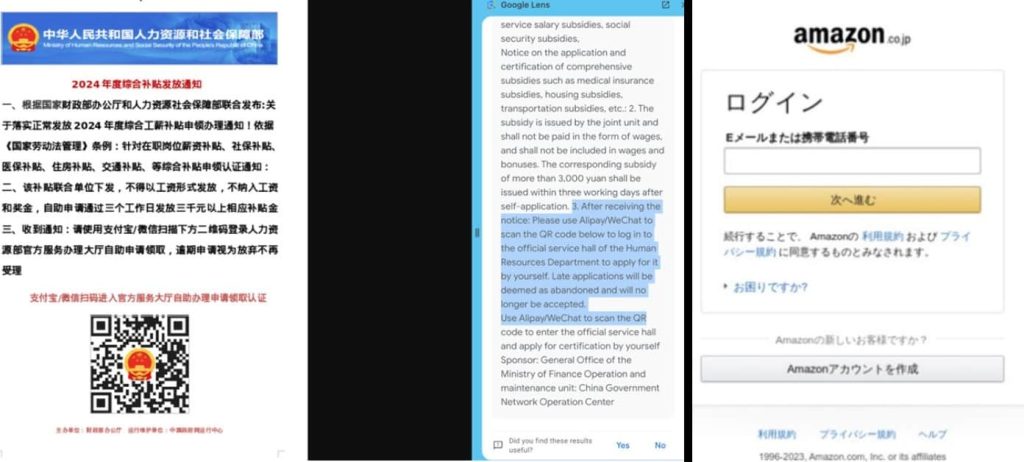
The investigation yielded a treasure trove of information about modern malspam techniques. Several distinct campaigns were identified, each employing sophisticated domain spoofing tactics to deceive recipients. These include QR Code Phishing, targeting Chinese citizens with emails containing QR codes, which redirect victims to phishing websites. Japanese Phishing campaigns impersonate reputable brands like Amazon and major Japanese banks and lure users to fake login pages.
Extortion campaigns demand ransom payments in cryptocurrency to prevent exposure. Mysterious Financial Campaigns, originating from China, send seemingly innocuous spreadsheet attachments purporting to be from a Chinese freight company. The purpose of these campaigns remains unclear, as they lack clear malicious content or motive, Infoblox researchers noted in their technical blog shared with Hackread.com.
Nevertheless, the research reveals a disturbing reality: domain spoofing remains a highly effective and prevalent tactic for spammers. Despite the existence of various security mechanisms designed to detect and prevent spoofing, these campaigns continue to evade detection and successfully reach their targets.
Infoblox’s research came just days after another domain abuse-related report was published by WatchTowr, which exposed more than 4,000 active hacker backdoors in expired domains and abandoned infrastructure worldwide. This shows the ongoing challenge of combating sophisticated spam techniques and the need for continuous implementation of cybersecurity measures.