Discover the Complete Story Behind the Collapse of the LockBit Ransomware Gang – From Infrastructure Seizures and Freezing Cryptocurrency Accounts to European Arrests, Charges, Indictments, and the Release of a Recovery Tool by Authorities.
In a groundbreaking operation, the United Kingdom’s National Crime Agency (NCA) has dismantled the notorious LockBit ransomware, one of the world’s most prolific ransomware groups – The takedown was part of “Operation Cronos.”
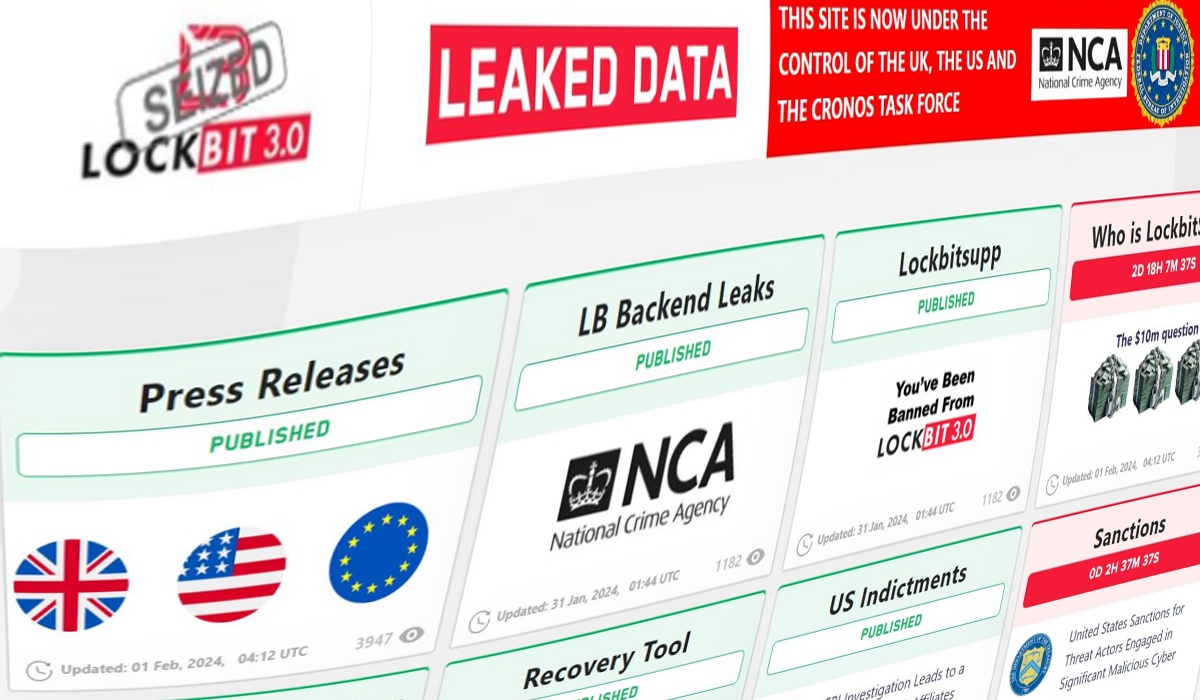
On 19 February 2024, Hackread.com’s in-depth report revealed that all dark web domains of LockBit ransomware had been seized. Now, according to the NCA’s press release, the latest development in this ongoing saga sees the agency taking control of LockBit’s primary administration environment, effectively cutting off the group’s ability to carry out further attacks.
Additionally, the agency has seized control of LockBit’s public-facing leak site on the dark web, repurposing it to expose the group’s tactics and operations.
LockBit Source Code and Backend
Crucially, the NCA has obtained the source code of the LockBit platform and a wealth of intelligence on the group’s activities and affiliates. This trove of information not only sheds light on LockBit’s modus operandi but also provides insight into the individuals and organizations complicit in their criminal enterprises.
One noteworthy disclosure from the NCA’s investigation is the discovery that some of the data on LockBit’s systems belonged to victims who had already paid ransom demands. This highlights the harsh reality that even compliance with ransom demands does not guarantee the safe return of stolen data—a fact often glossed over by cybercriminals.

Arrests and Indictments
The crackdown on LockBit extends beyond digital infiltration, with law enforcement agencies in multiple countries executing arrests and freezing cryptocurrency accounts linked to the group.
In a coordinated effort led by Europol, two LockBit actors from Poland and Ukraine have been apprehended, while the US Department of Justice has brought criminal charges against two Russian nationals Artur Sungatov and Ivan Kondratyev, alias Bassterlord, for deploying LockBit against multiple victims across the United States.
These victims include businesses spanning various industries nationwide, such as manufacturing, alongside global victims in sectors like semiconductors.
It is worth noting that in June 2023, Ruslan Magomedovich Astamirov (20), a Russian national, was also arrested and charged with conspiring to commit LockBit ransomware attacks against U.S. and foreign businesses. To date, the LockBit ransomware gang targeted over 2,000 victims and received more than $120 million in ransom payments.
A platform for LockBit victims
It is also crucial to mention that the FBI has established an online platform for victims of LockBit ransomware. This platform caters to both U.S. victims and non-U.S. victims interested in engaging with the U.S. LockBit prosecutions. Whether it’s to submit a victim-impact statement or to claim restitution, individuals can access the platform here: Lockbitvictims.ic3.gov.
Japanese LockBit Recovery Tool
The Japanese Police, with support from Europol, has developed a specialized recovery tool aimed at restoring files encrypted by the LockBit 3.0 Black Ransomware. To utilize this recovery solution effectively, users are instructed to execute the provided binary file on their affected machines, initiating an initial assessment process.
The tool will be available on the No More Ransomware platform soon. Alternatively, if you are a victim and based in the United Kingdom send an email to the NCA at lockbit@nca.gov.uk. Those in the United States can visit Lockbitvictims.ic3.gov.
The NCA’s Director General, Graeme Biggar, hailed the operation as a testament to the agency’s relentless pursuit of cybercriminals, emphasizing that no criminal enterprise is beyond its reach. Home Secretary James Cleverly echoed this sentiment, commending the NCA for disrupting LockBit’s operations and signalling the UK’s unwavering commitment to combatting cyber threats.
US Attorney General Merrick B. Garland emphasized the collaborative nature of the operation, highlighting the partnership between US and UK law enforcement agencies in dismantling LockBit’s criminal infrastructure. FBI Director Christopher A. Wray echoed these sentiments, underscoring the bureau’s dedication to defending against cyber threats and holding perpetrators accountable.
The NCA reveals details of an international disruption campaign targeting the world’s most harmful cyber crime group, Lockbit.
— National Crime Agency (NCA) (@NCA_UK) February 20, 2024
Watch our video and read on to learn more about Lockbit and why this is a huge step in our collective fight against cyber crime. pic.twitter.com/m00VFWkR9Z
Reaction from Experts
For insights into the latest development, we reached out to Ryan McConechy, CTO of Barrier Networks, who expressed appreciation for law enforcement’s role in combating cybercrime, particularly the escalating threat of ransomware.
“These actions demonstrate the efforts law enforcement is placing on fighting ransomware, but the seizure of LockBit’s servers is undoubtedly one of the biggest accomplishments so far.”
Ryan warned that seizing infrastructure and arrests does not mean the gang can not return. However, strengthening your cybersecurity measures can defend businesses against such threats.
“Organisations must act before it is too late,” he emphasised. “This involves training on threats, implementing MFA to secure employee credentials, keeping systems up to date with patches, and getting a well-oiled and comprehensive incident response plan in place, so everyone can step straight into effective action, even when attacks do occur,” Ryan advised.
As the dust settles on this major takedown, the NCA and its international partners stand ready to assist LockBit victims in recovering encrypted data and pursuing justice. With LockBit now effectively locked out, the NCA remains alert, knowing that the group may attempt to regroup and rebuild its criminal empire.
However, with the combined efforts of law enforcement agencies worldwide, the message to cybercriminals is clear: there is no safe haven for those who seek to profit from extortion and cybercrime.