North Korean state-sponsored threat group, Jumpy Pisces, collaborated with the Play ransomware group to carry out cyberattacks. Learn about the tools and techniques used, the impact of the attack, and how to protect your organization from similar threats.
A recent incident response case by Palo Alto Networks Unit 42 sheds light on a concerning development– a collaboration between a North Korean state-sponsored group and a financially motivated ransomware gang.
Jumpy Pisces, also known as Onyx Sleet and Andariel (also known as the “Guardians of Peace” APT which was behind the infamous HBO data breach), has a history of cyberespionage, financial crimes, and deploying custom-made ransomware like Maui. Unit 42’s investigation revealed a change in Jumpy Pisces’ tactics, suggesting they may be increasingly involved in ransomware attacks.
The incident involved an attack using Play ransomware, a threat first identified in mid-2022. While the group behind Play, Fiddling Scorpius, is thought to operate under a Ransomware-as-a-Service (RaaS) model, they have denied this on their leak site.
The Attack
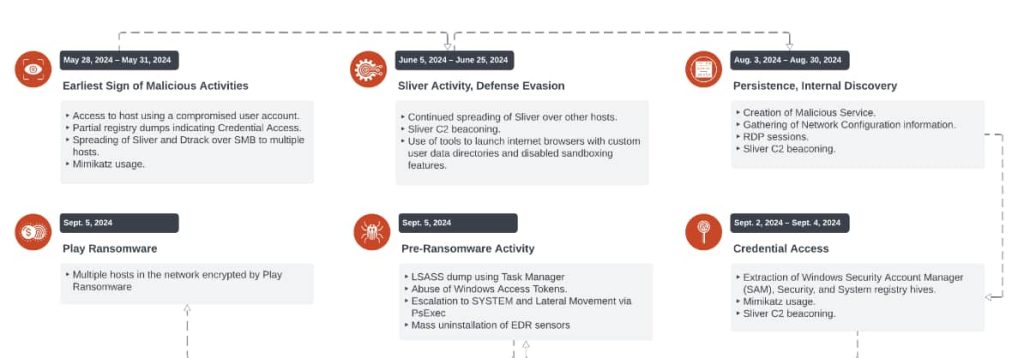
Unit 42’s investigation revealed a sequence of events that culminated in the deployment of Play ransomware. In May 2024, Jumpy Pisces gained initial access using a compromised user account. Between May and September 2024, they utilized tools such as the open-source Sliver and their custom DTrack malware to move laterally and maintain persistence across the network.
In early September 2024, an unidentified actor accessed the network through the same compromised account, likely building on Jumpy Pisces’ groundwork. This actor conducted pre-ransomware activities, including credential harvesting and EDR sensor removal, before deploying the Play ransomware later that month.
The customized version of the open-source Sliver C2 Framework enabled them to maintain persistent command and control (C2) communication, allowing remote command execution. The custom-built DTrack malware functioned as an infostealer, collecting sensitive information from affected systems and compressing it into disguised GIF files to avoid detection.
According to Palo Alto Networks Unit 42’s report, the attackers used PowerShell scripts to execute commands, transfer files, and interact with the system, while Mimikatz facilitated credential dumping by extracting plaintext passwords from memory for additional account access.
Researchers also noted the use of PsExec, a command-line tool that allows the execution of processes on remote systems, supporting lateral movement and privilege escalation. Additionally, TokenPlayer, a tool used in manipulating and abusing Windows access tokens, was utilized to steal tokens, enabling attackers to impersonate privileged users.
Collaboration or Opportunity?
Unit 42 believes that Jumpy Pisces collaborated with the Play ransomware group/Fiddling Scorpius in this attack because the same compromised account was used by both Jumpy Pisces and the Play ransomware actor. Jumpy Pisces ceased activity just before the ransomware deployment, and TokenPlayer and PsExec, are commonly seen in Play ransomware incidents.
Whether Jumpy Pisces acted as an official affiliate of Play ransomware or simply sold network access as an Initial Access Broker (IAB) remains unclear. However, this is the first documented instance of such a collaboration, raising concerns about the potential for increased participation of North Korean groups in ransomware campaigns as it poses a greater threat to businesses and organizations worldwide.
Erich Kron, a security awareness advocate at KnowBe4, noted that North Korea’s recent involvement in ransomware shows strategic collaboration due to financial motivations. Although North Korean actors are skilled at network access, their partnership with an established group is beneficial as they are new to ransomware operations. Kron emphasized the need for organizations to focus on combating email phishing, given the heavy reliance of ransomware on social engineering.