A collaborative effort by international cybersecurity agencies, including the National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC), Canadian Centre for Cyber Security (CCCS), and New Zealand National Cyber Security Centre (NCSC-NZ), has highlighted a critical security issue known as Fast Flux.
According to a joint advisory, both cybercriminals and state-sponsored actors are exploiting this new technique, which allows them to conceal malicious server locations and maintain persistent command and control (C2) infrastructure and has been declared a national security threat.
Understanding fast flux
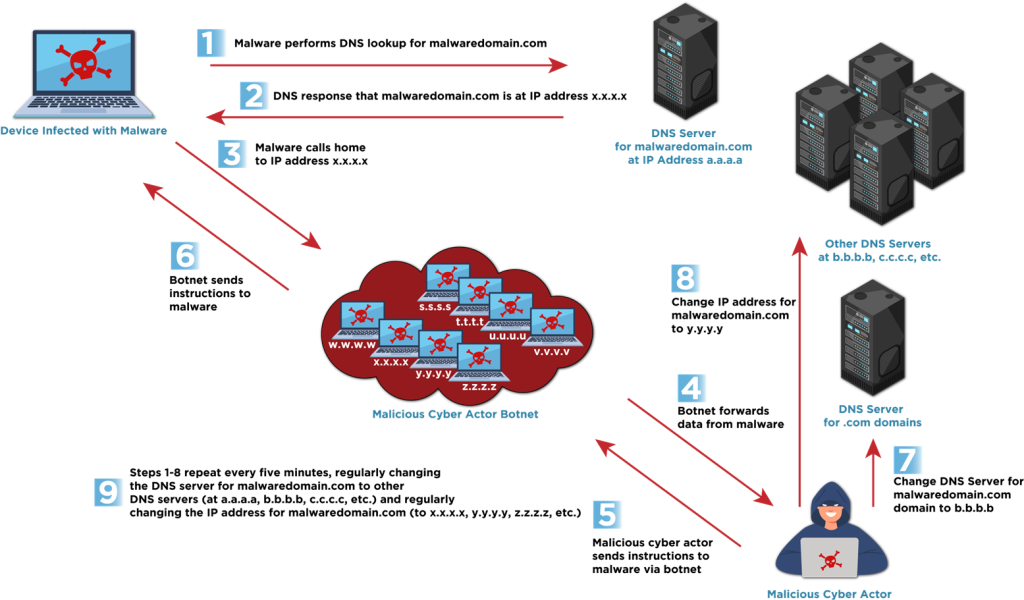
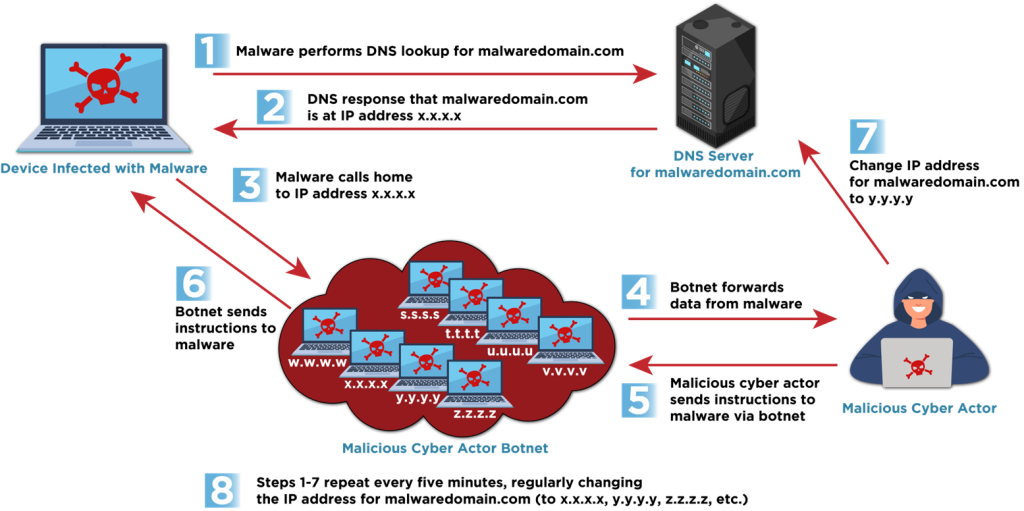
Fast flux’s core mechanism lies in the dynamic manipulation of Domain Name System (DNS) records. By rapidly altering the IP addresses associated with a single domain, attackers effectively obfuscate the true location of their malicious servers. This rapid rotation renders traditional IP-based blocking methods ineffective, as the target IP address becomes obsolete almost immediately.
Research reveals that cybercriminals are employing two methods of fast flux- Single flux and Double flux. Single flux involves linking a single domain name to numerous, frequently rotated IP addresses, ensuring that even if one IP is blocked, the domain remains accessible.
Conversely, Double flux further enhances this obfuscation by also frequently changing the DNS name servers responsible for resolving the domain, adding another layer of anonymity.
“These techniques leverage a large number of compromised hosts,” CISA notes, often forming botnets, which act as proxies to hide the malicious traffic’s origin.
Malicious Applications and the Role of Bulletproof Hosting
CISA emphasizes that Fast Flux is not solely used for maintaining C2 communications. It plays a significant role in phishing campaigns, making social engineering websites difficult to take down.
Furthermore, “bulletproof hosting” (BPH) providers, who disregard law enforcement requests, are increasingly offering it as a service to their clients. This allows for the seamless operation of malicious activities like botnet management, fake online shops, and credential theft, all while providing a layer of protection against detection and takedown, and has been used in Hive and Nefilim ransomware attacks. One BPH provider even advertised the service’s ability to bypass Spamhaus blocklists, highlighting its appeal to cybercriminals.
Detection and Mitigation
The agencies strongly recommend a multi-layered approach to detect and mitigate “fast flux” attacks. This includes leveraging threat intelligence feeds, implementing anomaly detection for DNS query logs, analyzing DNS record time-to-live (TTL) values, monitoring for inconsistent geolocation, and using flow data to identify unusual communication patterns.
For organizations, agencies recommend DNS and IP blocking, reputational filtering, enhanced monitoring and logging, and phishing awareness training as potent mitigation strategies. It is crucial for organizations to coordinate with their Internet service providers and cybersecurity providers, particularly Protective DNS (PDNS) providers, to implement these measures, the advisory concludes.
John DiLullo, CEO at Deepwatch, a San Francisco, Calif.-based AI+Human Cyber Resilience Platform, commented on the latest development, stating: This latest advisory will hit many organizations like a double espresso. Any enterprise relying on IP reputation as a credible means of securing their infrastructure or proprietary data is a soft target for this type of exploit.”
“Fortunately, correlative detection techniques, especially those leveraging ‘low and slow’ Machine Learning methods, can defeat these intrusions handily. However, many companies’ infrastructures simply aren’t there yet. This is a significant wake-up call,” he warned.