SUMMARY
- A sophisticated phishing campaign is targeting employees of 30+ companies across 12 industries worldwide.
- Over 200 malicious links have been distributed, designed to steal user login credentials.
- Attackers use trusted domains, dynamic company branding, and document platform impersonation to evade detection and trick users.
- Stolen credentials are sent to attackers in real time via C2 servers or Telegram bots.
- Organizations are urged to implement multi-factor authentication, train employees, and use advanced email filtering systems to protect against such attacks.
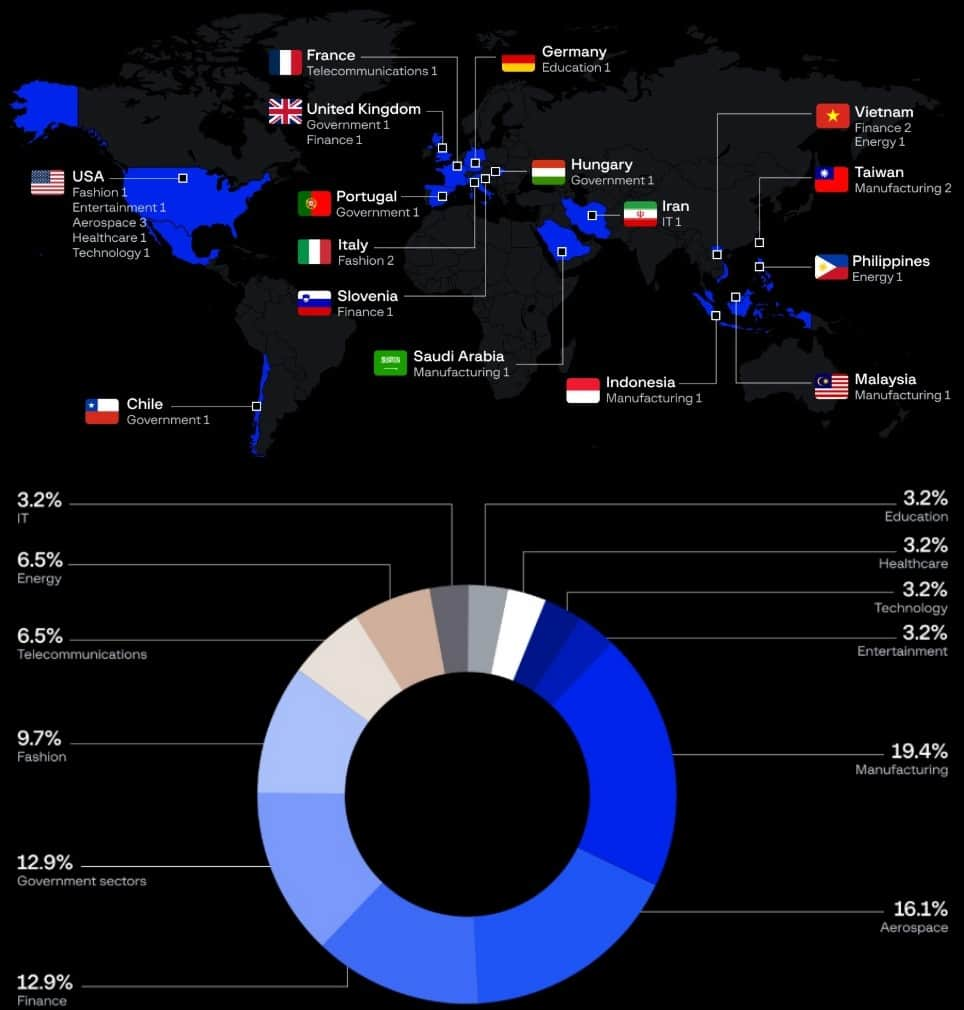
Cybersecurity researchers at Group-IB have exposed an ongoing phishing operation that has been targeting employees and associates from over 30 companies across 12 industries and 15 jurisdictions.
So far, the campaign has successfully distributed over 200 malicious links designed to steal login credentials. The industries targeted in this phishing operation include the following:
- Energy
- Fashion
- Finance
- Aerospace
- Manufacturing
- Telecommunications
- Government sectors
What makes this campaign dangerous is the use of advanced techniques designed to bypass Secure Email Gateways (SEGs) and evade detection. In particular, the attackers are using three main techniques to bypass email security:
- Trusted Domain Abuse
- Dynamic Company Branding
- Document Platform Impersonation
In the trusted domain abuse tactic, attackers embed malicious URLs within legitimate services like Adobe.com and Google AMP, making it harder for security tools to detect. In document platform impersonation, fake DocuSign and Adobe notifications are used to lure users into clicking links for what seem to be important documents.
Meanwhile, with dynamic company branding, phishing pages cleverly display the victim’s company logo and branding by pulling them directly from legitimate websites. It’s important to note that DocuSign has long been a target for cybercriminals to deliver malicious documents. While the platform works diligently to combat scammers, the abuse of its API has become a significant challenge in recent years.
Last month, a report revealed a staggering 98% increase in DocuSign phishing scams, including impersonation attempts and aggressive phishing attacks targeting the United States government.
In the ongoing attack, much like the previous campaign, users who click the malicious links are directed to convincing login pages that are pre-filled with their email addresses. Once credentials are entered, the data is sent to the attackers through either Command-and-Control (C2) servers or Telegram bots, giving them real-time access to the stolen information.
“The Telegram bot’s history log revealed that the collected credentials were not limited to a single company. Instead, they spanned a wide range of business email addresses belonging to various brands and countries, all impacted by an ongoing email phishing campaign,” Group-IB wrote in a blog post shared with Hackread.com heard of its publishing on Wednesday.
Protecting Against Email-Based Attacks
This campaign is ongoing therefore, companies need to watch out for what comes to their inbox. To stay protected, organizations should:
- Enable multi-factor authentication for an added layer of security.
- Train employees to verify unexpected document requests before taking action.
- Implement advanced email filtering systems to detect and block threats.
- Regularly monitor accounts for unauthorized access to quickly identify and address breaches.
RELATED TOPICS
- EvilProxy Phishing Kit Hits 100+ Firms, Bypasses MFA
- 99% of UAE’s .ae Domains Exposed to Phishing and Spoofing
- Black Basta Uses MS Teams, Email Bombing to Spread Malware
- Hackers Hit Job Seekers with AppLite Trojan with Fake Job Emails
- Phishers Impersonating Police Arrested in Multi-Million Euro Scam