360XSS campaign exploits Krpano XSS to hijack search results & distribute spam ads on 350+ sites, including government, universities, and news outlets.
A widespread campaign exploiting a vulnerability within a virtual tour framework Krpano has been uncovered by cybersecurity researcher Oleg Zaytsev. The attack, dubbed “360XSS,” involved search engine manipulation and mass advertisement distribution.
For your information, Krpano is a widely used software tool that enables the creation of immersive 360° experiences, allowing users to explore panoramic images and videos in a virtual environment.
Zaytsev’s research, shared with Hackread.com, revealed that the attack leverages a reflected cross-site scripting (XSS) flaw in the Krpano VR library tracked as CVE-2020-24901. The vulnerability resided in a configuration setting within the Krpano framework (passQueryParameter) that, by default, allowed query parameters to be passed directly into the framework’s configuration.
This enabled attackers to inject arbitrary XML, leading to the reflected XSS. The default setting enabled this flaw, leading to widespread exploitation until patches were released. Unfortunately, it remained unpatched on numerous websites, including the framework developer’s own site.
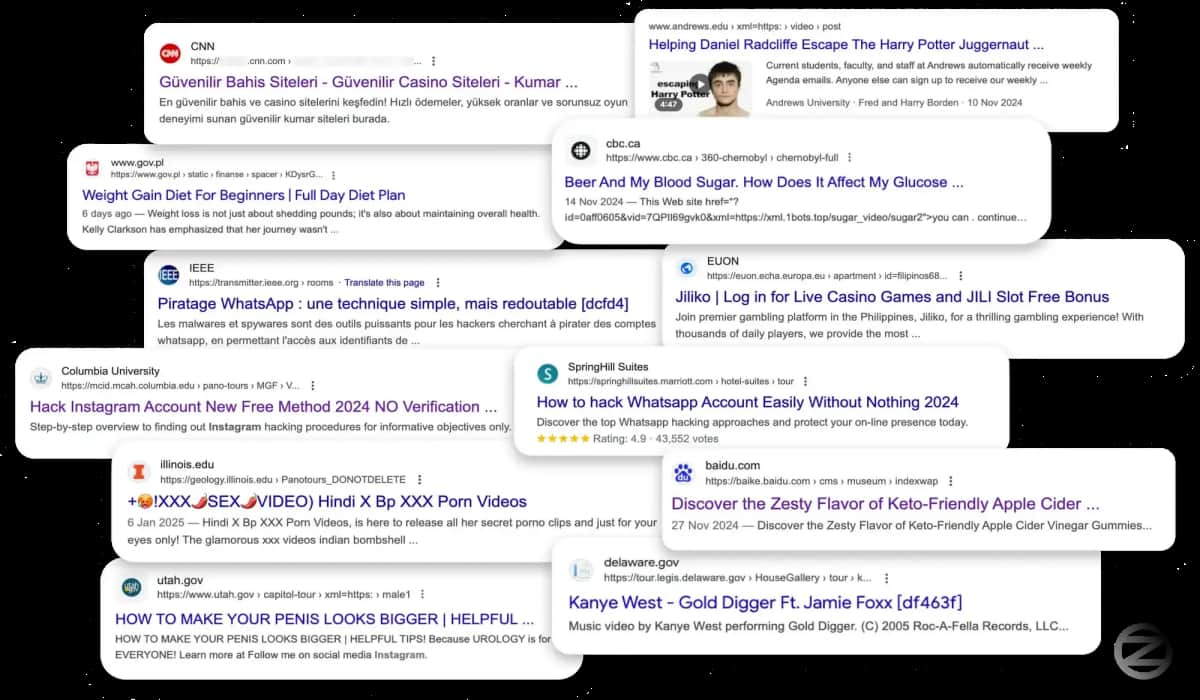
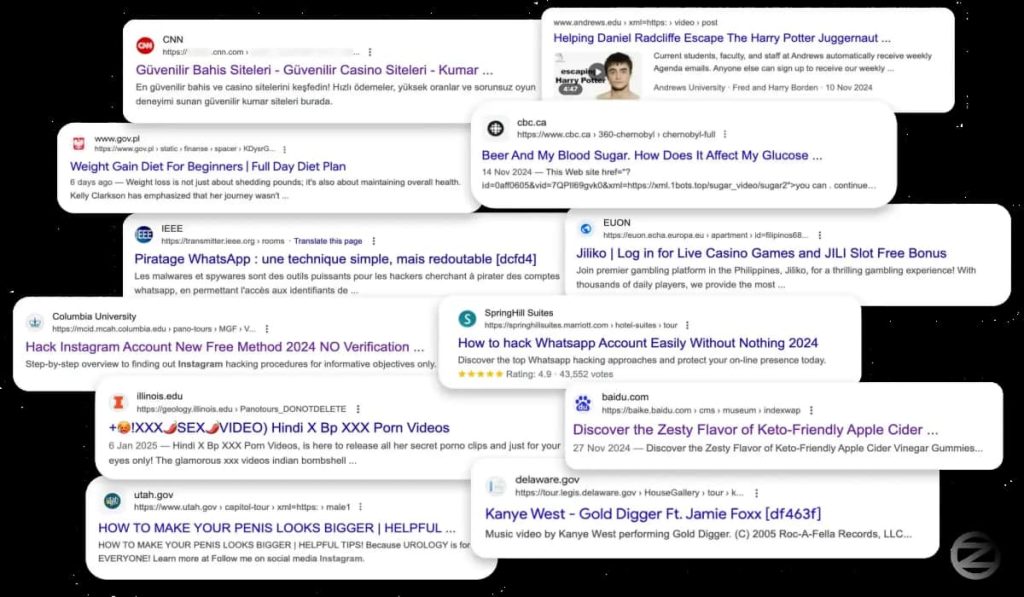
The campaign’s discovery began with an unexpected search result for adult content appearing under a prestigious university’s domain. Further investigation revealed that the site was utilizing the Krpano framework for virtual tours and that a specific parameter within the URL was being exploited to inject malicious code. This code redirected users to spam advertisements, indicating a sophisticated attack beyond simple website defacement.
The scale of the campaign was significant, with hundreds of websites, including government portals, educational institutions, news outlets, and major corporations, being compromised. Attackers used the XSS vulnerability to inject malicious scripts that manipulated search engine results, pushing spam advertisements to the top of search listings. This technique, known as SEO poisoning, allowed them to leverage the authority of compromised domains to boost the visibility of their advertisements.
The campaign had a wide-reaching impact, compromising over 350 websites across diverse sectors. This included sensitive government portals and state government sites, major American universities, prominent hotel chains, reputable news outlets like CNN and Geo.tv, car dealerships and Fortune 500 companies. Attackers’ focus on advertisement distribution, rather than direct attacks on user data, suggested a calculated approach probably by an Arab group.
“The people behind this campaign remain a mystery, but from what I’ve seen, many clues suggest it was run by an Arab group—based on the ads, patterns, and random breadcrumbs I found during my investigation,” Zaytsev noted in their blog post.
He further notes that efforts to report the vulnerability to affected organizations proved challenging, with many lacking formal disclosure programs. However, some organizations responded positively, and the Krpano developers addressed the issue with a patch in a subsequent release. Organizations using the Krpano framework are advised to update to the latest version and disable the vulnerable configuration setting.
Eran Elshech, Field CTO at Seraphic Security, highlights that attackers are shifting from malware to exploiting browser vulnerabilities and web frameworks. The 360XSS campaign demonstrates how easily a known XSS flaw was used to compromise trusted sites, manipulate search results, and hijack web properties for spam ads.
He warns that the scalability and stealth of such attacks make them highly effective, as attackers infiltrate high-traffic sites with minimal effort, reaching large audiences without direct access to user devices.