The IT security researchers at CloudSEK have reported that millions of mobile app users may have exposed their private and payment data due to API security vulnerabilities discovered in several applications.
The report revealed that around ten mobile apps using Razorpay payment gateway exposed secret transaction keys. This jeopardizes users’ data safety and makes them vulnerable to a wide range of attacks.
For your information, Razorpay is a widely used platform, serving over 8 million businesses across the globe.
A Case of Mishandled APIs
CloudSEK revealed in its report titled ‘Exposed Payment Integration API Keys Imperil Millions of User’s Transaction Details and PII’ that around 13,000 apps were uploaded on its BeVigil security search engine. Out of these, nearly 250 apps used the Razorpay API for processing financial transactions. Around 10 (5%) of these apps exposed the payment integration key ID and key secret.
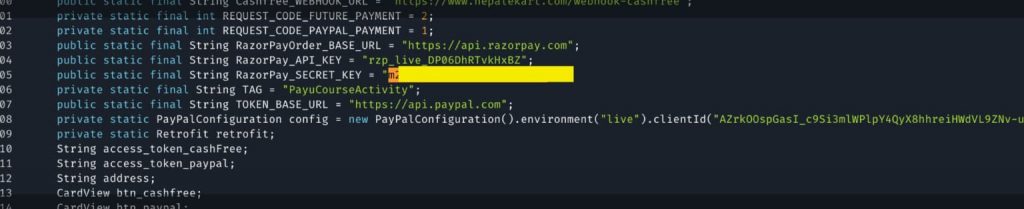
The API key is a combination of a key secret and a key ID. Both are needed to make an API request to the payment service provider. In this case, the developers “accidentally” embedded the API key in their source code that led to this issue, CloudSEK researchers noted in their blog post authored by Arshit Jain and Sai Ahladini Tripathy.
“While developers might be aware of exposing API keys in their mobile apps, they might not be aware of the true impact this has on their entire business ecosystem,” researchers explained.
Razorpay Cannot Be Blamed!
Razorpay, researchers observed, is not to be blamed for this fault, and instead, the companies are responsible. In its defense, Razorpay’s Head of Corporate Communication and Branding, Hepsibah Rosario, released the following statement:
“Razorpay clearly mentions in contracts signed with merchants that such keys should not be exposed on any public platform.”
The Leaky Apps!
The ten leaky mobile apps include Jaggi Vasudev’s Isha Foundation, Steeloncall.com (steel trading e-commerce app), Zify (vehicle hiring app), Ruptok (fintech platform), and Spark Live. All these apps were found to be exposing API keys.
During their research, CloudSEK researchers could access transaction information and payment IDs for Rs 1,82,813, and these two details were enough to carry out a refund.

Dangers of Exposed API Keys
Researchers noted that various small and large companies catering to millions of users have mobile applications with hardcoded API keys in their app packages. For an attacker, it is pretty easy to discover these keys and use them to compromise user data or company networks. Data exposed in this manner may include sensitive user details such as email IDs, phone numbers, transaction IDs and amount, order/refund details, etc.
Since most users integrate data with other apps and wallets, this could be even more devastating as cybercriminals can use exposed API keys to perform bulk purchases, initiate refunds, use stolen data to launch social engineering attacks and phishing attacks, or sell the data on the Dark Web.
How to Stay Protected?
Although the company has deactivated the 10 apps, it urges developers to realize the impact of such issues and implement effective review processes to protect sensitive user data. Researchers explained that regenerating API keys is a complex process. Therefore, payment providers should design APIs that offer options to minimize a key’s permissions and access controls even if it hasn’t been invalidated.
“App developers should be given a mechanism to limit what can be done using a key at a granular level, as AWS does. AWS has put in place identity and access management (IAM) policies that can be used to configure the permissions of every operation on an S3 bucket. This practice should be more widely adopted to minimize what threat actors can do with exposed API keys,” the blog read.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.









