Mobile phones are now also being utilized for the purpose of managing some important personal assets such as money. According to a recent report that has been published by the Federal Reserve of US, around 48 percent of the smartphone users in the last 12 months have used the mobile banking platform for carrying out their monetary transactions with banks. This number has gone up by 6 percent as it was around 42 percent back in December last year. Approximately half of the smartphone devices users have installed mobile banking transaction apps in their devices and are using them for such activities.
Anti-virus and online security provider Mcafee reported recently that a Trojan has replaced a famous South Korean mobile banking app with some malware. Well this is quite alarming for the ones using that app. This malware steals confidential information of the user for the purpose of conducting various types of financial frauds. It is very much similar to other mobile threats that have been reported in South Korea. This malware uses the SMS Phishing or smishing (SMS phishing) attacks by sending fake messages to users on behalf of the commission of financial services asking such users to set up new anti-malware app for their devices. The short URL that it provides for the purpose when clicked starts downloading the malware which appears like a Google application with the play store symbol but no other label.
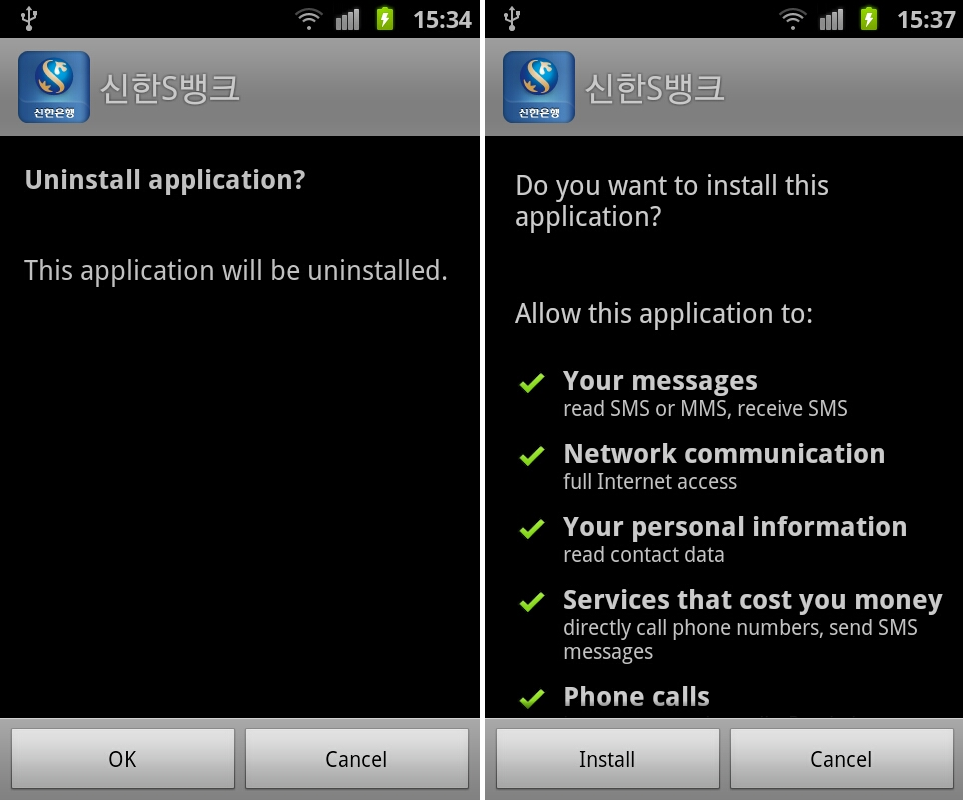
The victim when executes this malware, it scrolls the device and checks that if the users has any of the following banking applications installed i.e. KB Kookmin Card ( by the largest credit card corporation of the country), Shinhan Bank, Woori Bank, Nonghyup Bank, Hana Bank, KFCC or SC First Bank. If any or all of such banking apps are detected by the malware, the device will be routed and a de-installation of the banking app will be performed without notifying the user. The following commands for rooting are executed of the purpose.
-
mount -o remount rw /data (remount the data partition as read/write)
-
chmod 777 /data/app/<package_name_banking_app>.apk (changes permissions of APK file)
-
pm uninstall <package_name_banking_app> (silently removes the application)
However if the user has not got the device rooted, the malware or the fake app will ask the user to de-install the original banking app. In exchange it will offer the user to install another banking application with similar icon but with suspicious permissions.
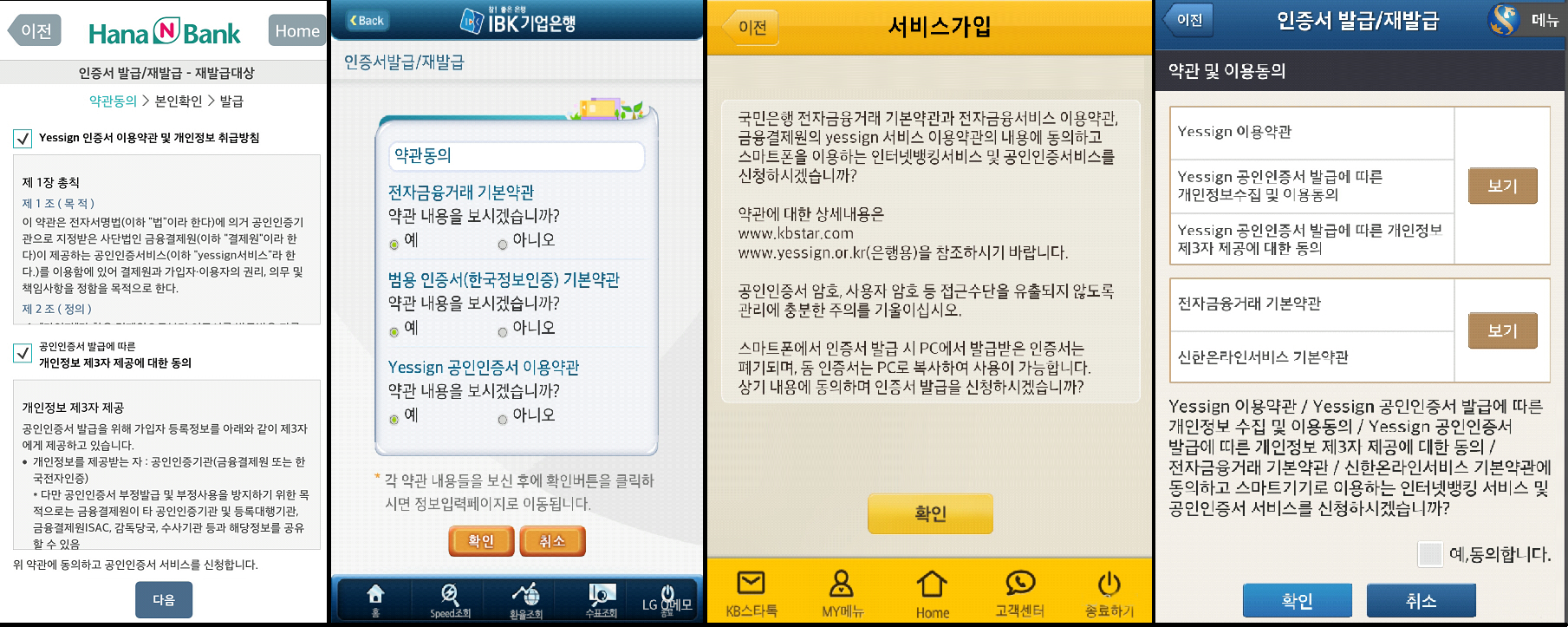
This newly installed fake app will be contained in assets folder of the malware app that the victim originally installed under instruction of the fake SMS. The newly installed replacement app is basically the original malware but has menus and icons which have been customized with reference the legitimate banking apps as have been mentioned above. This allows the malware to catch on the confidential financial information of the victim user. For some of the banks that have been mentioned earlier, the Phishing attack also renders a report to the user that the app link being provided has been certified and attested by Yessign which is a certification authority of South Korea. This certification or report asks the user to give assent to the terms that have been mentioned in the certificate for allowing it to collect personal information for use. This ensures the user that the app being offered is an authentic app of the banking company though it isn’t.
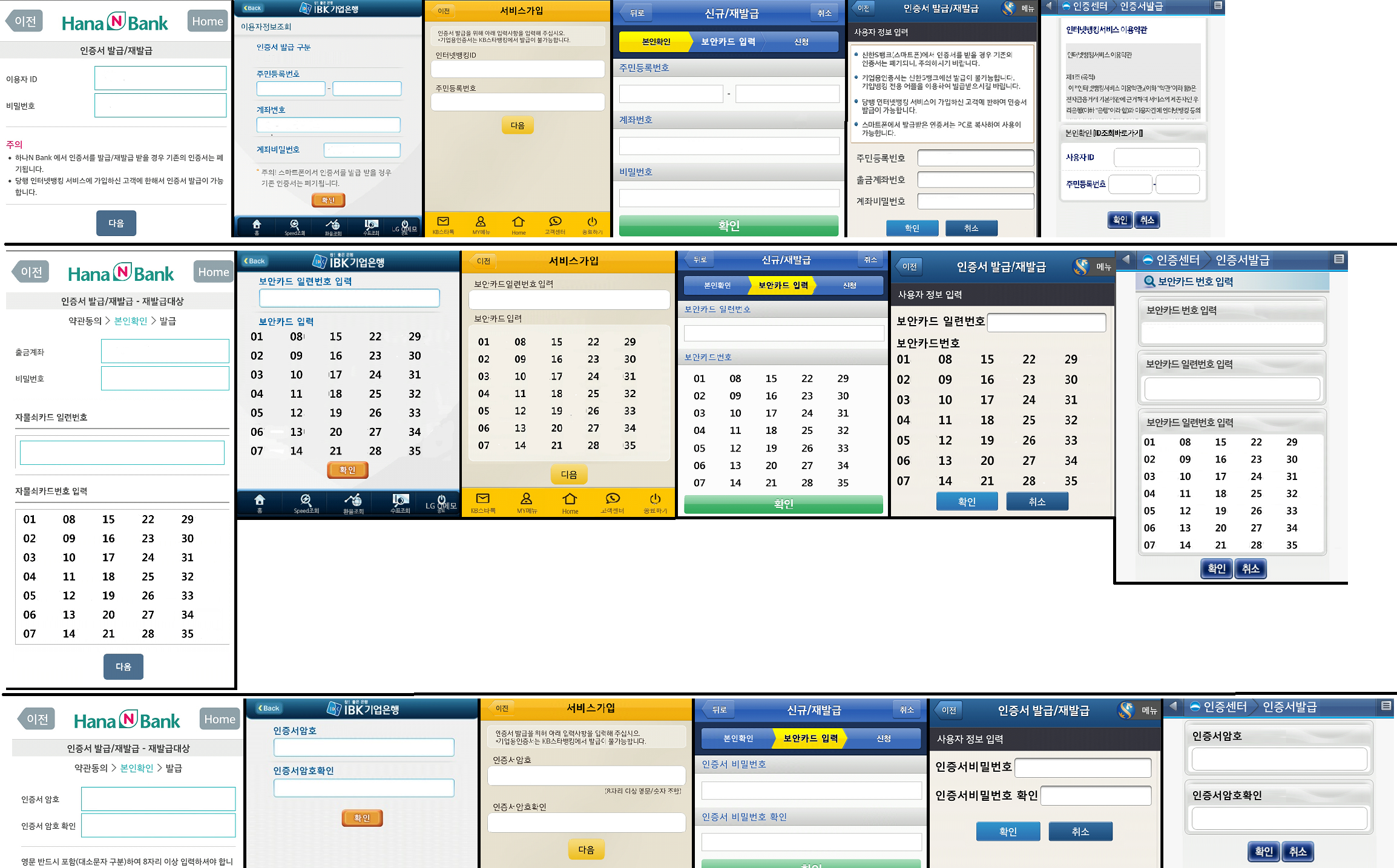
The malware app sometimes even ask the user to feed in banking credential like social security no, account password, account no, withdrawal account no, banking ID, User ID, Resident registration no and password etc.
Then the malware tries to gain the values and serial number of the grid card followed up by asking for certificate password which is another factor for authentication.
For KFCC and Nonghyup banks, it only asks for information in one interface: social security no, name, cell phone no, user password and ID, serial number and security card no, user password and account no.
The acquired information is later transmitted to a server through HTTP along with the victim’s cell phone number. Apart from the Phishing attack, following functions can also be performed at the backend by this malware and that too without any permission or approval from the victim.
-
Detects when the user makes or receives a call and obtains the number of the incoming call. It also changes the ringer mode by making it silent and disconnects the call without the user’s notice.
-
It intercepts the messages received by the user and transmits the same to some remote server.
-
If the legitimate banking application still remains, it conducts a background operation for its uninstallation and also sends messages to numbers that are premium rated, using data that has been sent by control server using HTTP.
Considering the fact that the use of android mobile applications for conducting banking transaction has increased so much, there is a prominent risk that such malware can emerge in other regions of the world such as America and Europe and can cause huge loss of funds to people. The malware threat which is targeting banking transaction through mobile has emerged from a joint PC attack for mobiles e.g. Spitmo and Zitmo. Similarly it uses Phishing attacks through the use of apps like the Fake token and via using SMS messages where a URL is provided for downloading an infected replacement app in place of the legitimate or authentic app of the baking company for the purpose of obtaining various authentication factors. These authentications as has been discussed above include account password, certificate password, mTANs sent through SMS and information about the grid card. This malware also operates in a conventional android malware manner i.e. it sends SMS without the permission of the victim.
Now comes the point of how to detect if any such malware has infected your device or how to get rid of it. Mcafee Android mobile security indicates any such threat or malware as Andriod/FakeBankDropper.A and as Andriod/FakeBank.A. It notifies the victim if any such threat is found and also protects the device from any sort of data loss. For acquiring further information related to this McAfee security system for mobiles, just follow the link.










Comments are closed.