Spanish speakers beware! A new campaign using the Agent Tesla RAT targets Spanish-speaking individuals. Learn how to protect yourself from this and other malware attacks.
FortiGuard Labs has discovered a phishing campaign targeting Spanish-speaking individuals to spread a new Agent Tesla malware variant. The campaign uses various techniques to target Windows-based systems and deliver the core module, including MS Office vulnerabilities, JavaScript code, PowerShell code, and fileless modules, wrote FortiGuard Labs’ researcher Xiapeng Zhang in their report.
Here is how the attack works:
A Spanish-language phishing email posing as a SWIFT transfer notification from a large financial institution is sent to MS Windows users. The email, translated into English, appears to be a message with a disguised Excel attachment in OLE format with crafted embedded data that exploits the CVE-2017-0199 vulnerability.
The attachment contains an embedded OLE hyperlink, opened automatically once the victim starts the Excel file. Later, it automatically downloads an RTF document, which is opened by the Word program.
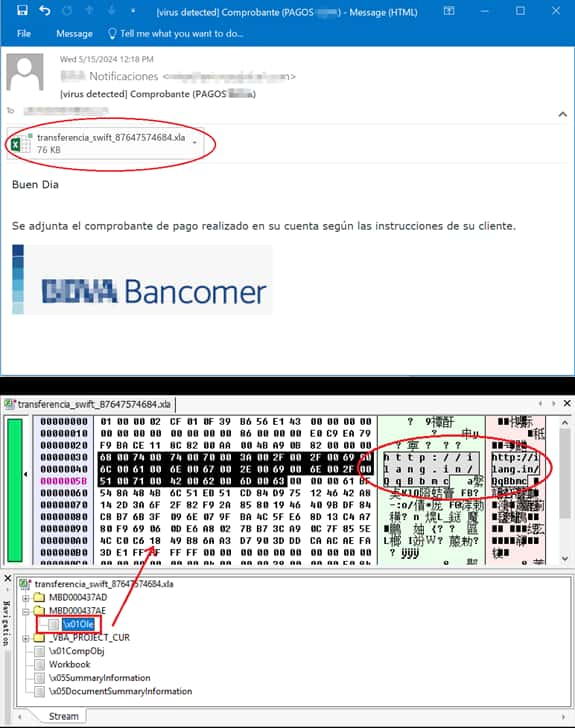
Another vulnerability exploited in this attack is CVE-2017-11882, a Remote Code Execution vulnerability in Microsoft Office’s Equation Editor component, allowing attackers to execute arbitrary code on a victim’s computer by overriding a return address in the stack.
This Agent Tesla variant is a powerful, versatile 32-bit, .NET-based Remote Access Trojan (RAT) granting attackers complete control over infected devices. Once installed, it can steal sensitive information from 80 software applications, focusing on login credentials, banking details, and email contacts.
Additionally, it checks if the email client is Thunderbird, cookies from a wide range of web browsers such as Chromium-based and Mozilla-based browsers, system clipboard data, computer name, OS/CPU/RAM information, and saved credentials. It can also spy on you by capturing keystrokes and screenshots. The malware is assigned a critical severity level.
As per the report published by FortiGuard Labs, the Agent Tesla core module is a fileless module downloaded by a malicious JavaScript base64-encoded Powershell code as a normal JPG file from this URL:
uploaddeimagens[.]com[.]br/images/004/773/812/original/js.jpg?1713882778.This module is never saved in the local folder, making it difficult for researchers to detect. Surprisingly, this variant uses FTP protocol for data submission, unlike past variants that used HTTP POST and SMTP protocols.
Moreover, it “detects whether it’s running in an analysis environment, like sandboxes, virtual machines, etc., or where there is AV software running, like Avast, Comodo, etc.,” Zhang noted.
To stay protected, be cautious of phishing emails, update the operating system regularly, use strong passwords, and invest in reputable anti-malware solutions.








