Summary
- Massive Data Leak: Propertyrec exposed over 644,000 records, totaling 713 GB of sensitive data.
- Sensitive Information: Leaked data includes background checks, personal details, and property reports.
- No Security Measures: The database lacked basic password protection, leaving it publicly accessible.
- Cyber Risks: Exposed data increases risks of identity theft, fraud, and social engineering scams.
- Call for Better Security: Experts stress the need for encryption, access controls, and regular audits.
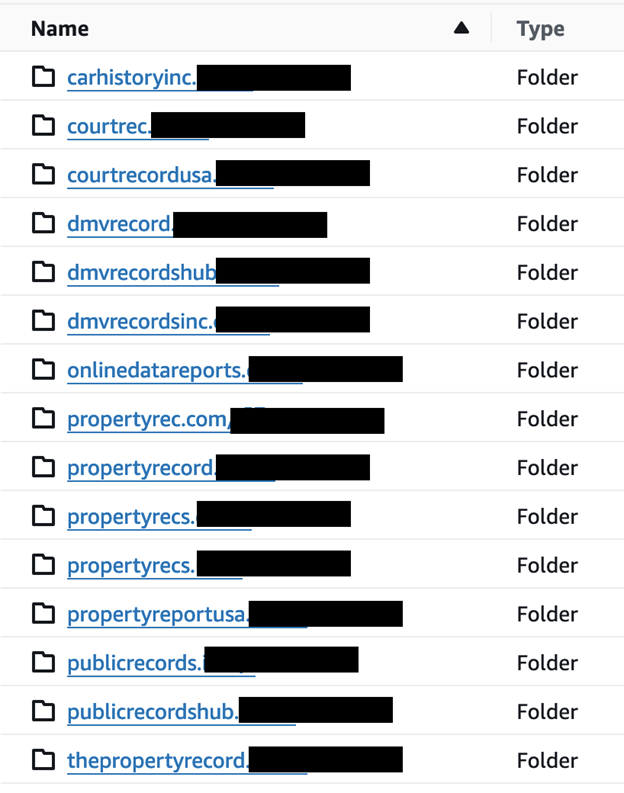
A critical data security lapse has left a massive trove of personal information vulnerable, raising concerns about identity theft and targeted attacks. The exposed data belongs to SL Data Services, LLC, which is doing business as Propertyrec, which offers real estate and criminal record search services.
Security researcher Jeremiah Fowler discovered a publicly accessible database containing over 644,000 files, totalling a whopping 713 GB of data. Notably, this database lacked even basic password protection, leaving it wide open for anyone to access.
What Information Was Exposed?
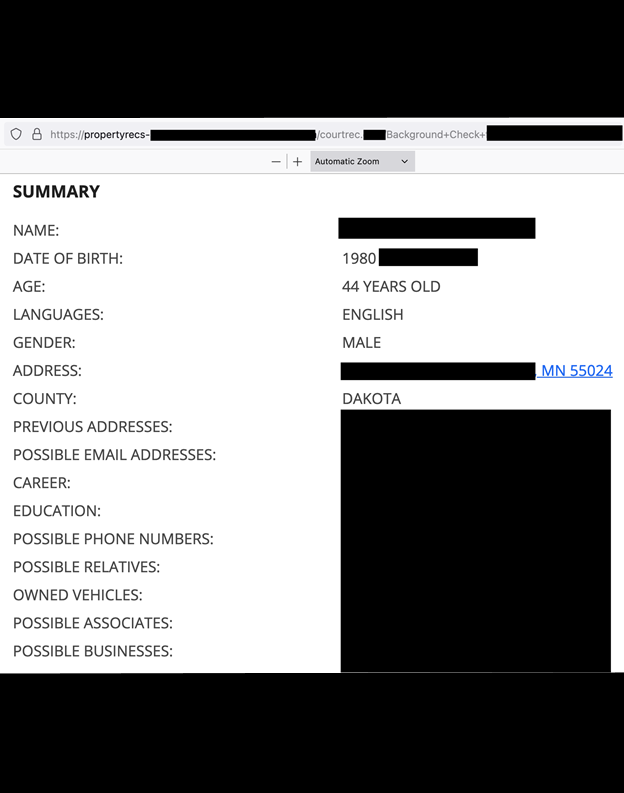
The exposed database contained a goldmine of sensitive personal information, including:
- Full names
- Phone numbers
- Home addresses
- Email addresses
- Employment history
- Family member details
- Social media accounts
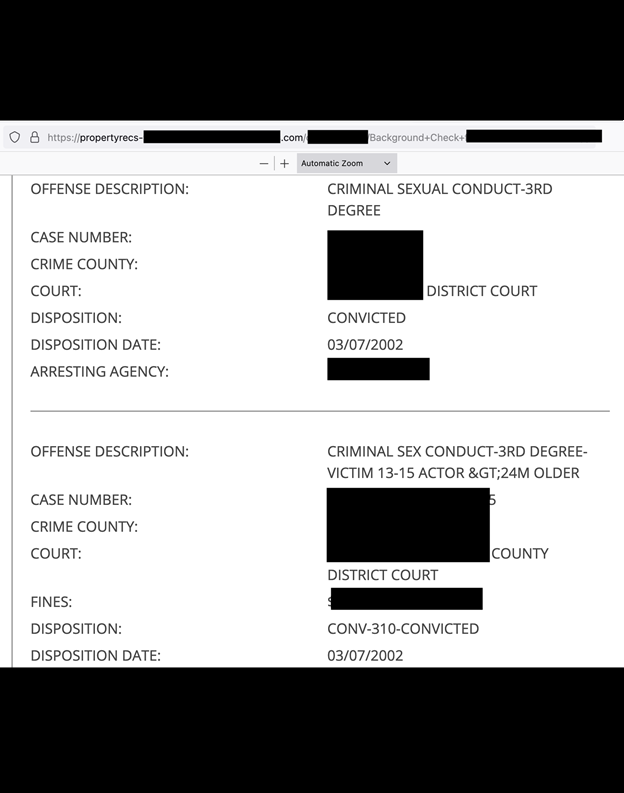
- Criminal record history
- Property ownership reports
- Vehicle records (license plate and VIN)
“Around 95% of the limited sample of documents I saw were labelled as “background checks” Fowler noted in his report shared with Hackead.com ahead of its publishing.
This treasure trove of personal data paints a complete picture of individuals’ lives, making them vulnerable to a multitude of threats. Furthermore, this data breach creates a breeding ground for malicious activity as with a wealth of personal information, cybercriminals can create highly personalized phishing emails or social engineering scams. These scams could trick victims into revealing sensitive information like passwords or financial details.
That’s not all! possessing a person’s full name, address, and social security number (if obtained elsewhere) gives criminals the tools to impersonate that person and potentially commit financial fraud. And, criminals could use the exposed information to impersonate an individual and gain access to their accounts or personal information from friends, family, or employers.
The incident reflects the importance of adopting stronger security measures for companies handling sensitive data. Fowler suggests that organizations should avoid storing personal information in file names, implement strong access controls, and conduct regular security audits to identify and address security vulnerabilities, even if files are encrypted.
This incident follows the National Public Data data breach incident from August 2024, which compromised millions of individuals’ personal information by hackers who accessed the company’s systems and sold the stolen data on the dark web for USD 3.5 million.
RELATED TOPICS
- Best Paid and Free OSINT Tools for 2024
- Fuel Industry Software Provider Exposes SSNs, PII Data
- US and UK Military Social Network Exposes SSN, PII Data
- AI Firm’s Server Exposed 5.3 TB of Mental Health Records
- UK Criminal Records Office Crippled by Ransomware Attack
- Instant Checkmate, TruthFinder Hacked: 20M Accounts Leaked
- Mexico’s Largest ERP Provider ClickBalance Leaks 769M Records