- The FBI and the US DoJ dismantled the Qakbot botnet, which is one of the largest and most sophisticated botnets in the world.
- The botnet was used to carry out financial fraud, ransomware attacks, and other cybercrimes, resulting in losses of hundreds of millions of dollars to businesses and individuals across the US and abroad.
- The dismantling of the botnet was a multinational operation involving law enforcement agencies from France, Germany, Romania, the Netherlands, Latvia, the US, and the UK.
- The FBI obtained lawful access to the botnet’s infrastructure and redirected its traffic to Bureau-controlled servers. This instructed the compromised computers to download an uninstaller file that removed the malware.
- The department also confirmed seizing around $8.6 million in cryptocurrency in illegal profits (extorted funds).
The US Federal Bureau of Investigation (FBI) has confirmed the dismantling of notorious malware and botnet called Qakbot (QBot and Pinkslipbot). The FBI and the US DoJ (Department of Justice) announced in a joint press release on August 29 that the dismantling was possible through a multinational operation in which law enforcement agencies from France, Germany, Romania, the Netherlands, Latvia, the US, and the UK participated.
Per the DoJ’s press release, this is the largest ever botnet infrastructure’s financial and technical disruption facilitated by the USA. Qakbot botnet was developed in 2008 and used to carry out financial fraud, ransomware attacks, and other cybercrime.
The botnet was used in countless ransomware attacks and cybercrimes, resulting in losses of hundreds of millions of dollars to businesses and individuals across the US and abroad. Many ‘prolific ransomware groups’ such as REvil, Conti, Egregor, Black Basta, and MegaCortex used the Qakbot botnet for initial infection.
The malware was distributed through spam emails containing malicious links/attachments. When the victim clicked on the link and downloaded the malware, it fetched additional payload, including ransomware, on the device and made it a part of Qakbot’s ever-expanding botnet army.
This allowed the attackers to control the device remotely while the victim remained unaware of the intrusion and exploitation.
According to FBI director Christopher Wray, the bureau ‘neutralized’ this extensive ‘criminal supply chain,’ the victims of which were extremely diverse, including financial institutions on the East Coast, medical device manufacturers on the West Coast, and a critical government infrastructure contractor based in the Midwest.
“This botnet provided cybercriminals like these with a command-and-control infrastructure consisting of hundreds of thousands of computers used to carry out attacks against individuals and businesses all around the globe.”
Christopher Wray – FBI
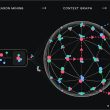
During the operation, the FBI obtained lawful access to the botnet’s infrastructure and detected that it comprised more than 700,000 infected computers worldwide. Around 200,000 were located in the US.
The disruption process involved redirecting Qakbot botnet’s traffic to Bureau-controlled servers, which instructed the compromised computers to download the uninstaller file created to remove the malware.
The uninstaller untethered the computers from the botnet and prevented them from accepting additional malware. The department also confirmed seizing around $8.6 million in cryptocurrency in illegal profits (extorted funds).
Wray appreciated the efforts of FBI Los Angeles, the bureau’s Cyber Division, and participating agencies within and outside the USA.
“The cyber threat facing our nation is growing more dangerous and complex every day. But our success proves that our own network and our own capabilities are more powerful,” the FBI director said.