Discover the RAMBO attack, a groundbreaking method that uses electromagnetic waves to steal data from air-gapped systems. Learn how hackers exploit isolated networks using electromagnetic emissions to extract sensitive information securely.
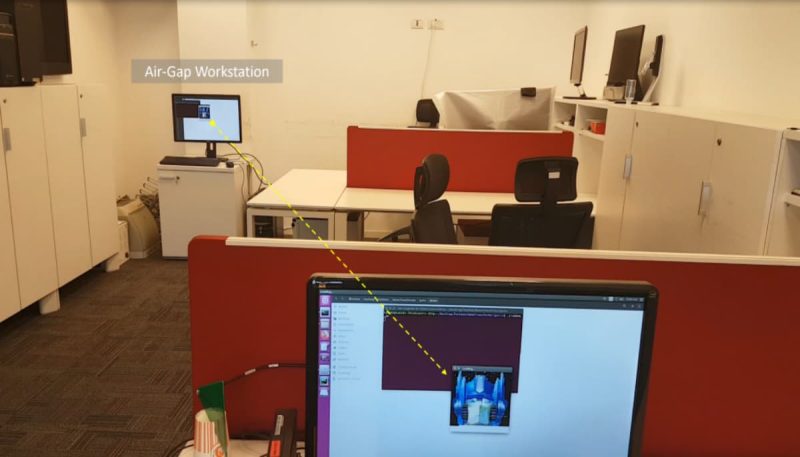
Researchers at the Ben-Gurion University of the Negev, Israel have identified a new method to compromise the security of air-gapped systems. For your information, air-gapped systems are physically disconnected from the wider network and internet, limiting the transmission of sensitive data. Even if a user introduces malware through a compromised USB device, the malware cannot transmit the data to the outside world.
However, according to university researcher Mordechai Guri, malware can tamper with RAM components and the newly discovered attack method dubbed “RAMBO” (Radiation of Air-gapped Memory Bus for Offense) exploits the electromagnetic emissions from the computer’s memory buses to transmit sensitive information.
It makes sense because RAM data transfer generates electromagnetic fields, radiating energy at a frequency influenced by clock speed, data width, and architecture, and a transmitter can modulate memory access patterns to create an electromagnetic covert channel, Guri noted in a recently published paper.
How the Attack Works
The attack involves deploying malware on an isolated system, either through an infected USB drive, an insider, or by compromising the supply chain. The malware will manipulate memory operations to generate radio signals that encode sensitive data such as files, images, keystrokes, biometric information, and even encryption keys.
These signals, transmitted through the air, can then be intercepted by an attacker using a simple software-defined radio (SDR) device and a basic, off-the-shelf antenna. RAMBO will then exfiltrate encoded files, exposing the data at 1,000 bits per second. Tests were conducted from up to 7 meters distance.
The method is slow and requires a person to be relatively close, and file transfer is slower than dial-up. Keylogging can be done in real-time with 16 bits per key (Unicode), and a 4096-bit RSA encryption key can be exfiltrated at 41.96 sec at low speed and 4.096 bits at high speed.
However, biometric information, small files, and documents take 400 seconds at low speed to a few seconds at fast speeds. While it may not be suitable for stealing large files or databases, it can still be used to steal keystrokes, passwords, or other data that doesn’t take up too much space.
“By precisely controlling the memory-related instructions, arbitrary information can be encoded and modulated on the electromagnetic wave. An attacker with a software-defined radio (SDR) can receive the information, demodulate it, and decide.”
Mordechai Guri
The Threat to Security
In his previous research, Dr. Guri and his team demonstrated how attackers can steal data from air-gapped PCs through SATA Cables. Another research released by Dr. Guri demonstrated how an air-gapped PC could be compromised by turning its RAM into Wi-Fi card.
Now RAMBO can have significant implications given that Air-gapped systems are often used in highly sensitive environments, such as military installations, financial institutions, and critical infrastructure. The ability to exfiltrate data from these isolated systems poses a serious threat to national security, privacy, and economic stability.
The researcher proposes countermeasures such as physical isolation techniques like Faraday cades, advanced intrusion detection systems, and external radio monitoring. However, these measures may have limitations or introduce additional overhead. Further research is needed to develop more effective countermeasures and develop new techniques for detecting and preventing such attacks.
RELATED TOPICS
- Malware can extract data from air-gapped PC via power supply
- Night Vision Enabled Security Cameras Secretly Transfer Your Data
- Hackers can steal data from air-gapped PC using screen brightness
- Malware can Convert your Headphones into Microphone for Hackers
- Hackers can steal data from Air-Gapped PCs with microphones, speakers