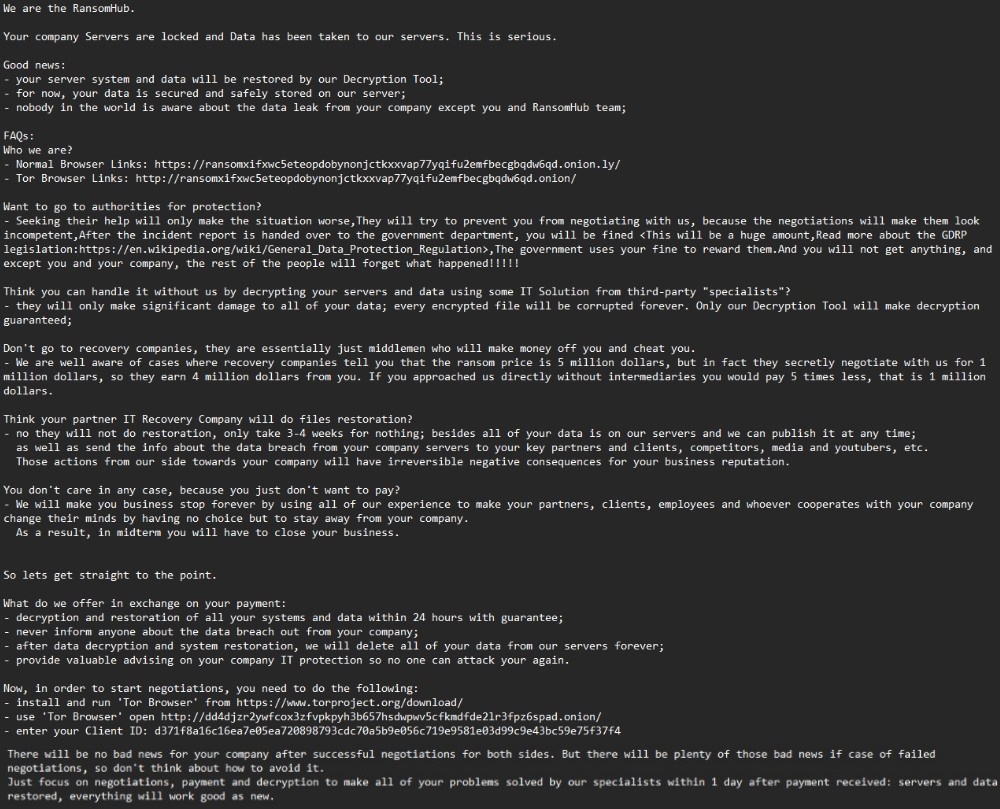
RansomHub emerges as a major ransomware threat in 2024, targeting 600 organizations after ALPHV and LockBit disruptions. Group-IB reveals its rapid rise in cybercrime.
Group-IB’s latest research, shared exclusively with Hackread.com, highlights the sudden rise of ransomware-as-a-service operations, with one group being very active in this domain, identified as RansomHub. Emerging in early 2024, RansomHub quickly established itself as a major player, capitalizing on the disruption of other prominent groups like ALPHV and LockBit.
Group-IB’s investigation reveals that RansomHub strategically advertises its partnership program on underground forums like the RAMP forum, actively recruiting affiliates from disbanded ransomware operations, which helps them rapidly expand their reach and impact.
Further investigation suggests that RansomHub likely acquired its ransomware and web application source code from the Knight group (aka Cyclops), demonstrating the interconnected nature of the world of cybercrime. By leveraging existing resources, RansomHub accelerated its development and deployment, quickly becoming a significant threat. Their ransomware is designed for cross-platform compatibility, targeting various operating systems and architectures, including Windows, ESXi, Linux, and FreeBSD. This versatility allows them to maximize their potential targets.
RansomHub’s operations reflect a high degree of sophistication. They utilize advanced techniques, such as exploiting zero-day vulnerabilities and employing tools like PCHunter to bypass endpoint security solutions. Their adaptability is evident in their rapid weaponization of newly discovered vulnerabilities, often outpacing defenders’ ability to patch systems. They also demonstrate proficiency in traditional attack methods, such as brute-force attacks against VPN services when necessary.
Following initial reconnaissance and exploitation of vulnerabilities, they establish persistence within the compromised network and proceed with internal reconnaissance, identifying and targeting critical assets like network-attached storage (NAS) and backup systems. Data exfiltration is a key objective, with tools like Filezilla used to transfer sensitive information to external command and control servers.
The final stage of a RansomHub attack typically involves data encryption and extortion. They disable backup services and deploy ransomware to render data inaccessible, effectively crippling the victim organization. The ransomware itself boasts advanced features, including the ability to terminate virtual machines, delete shadow copies, and clear system event logs. This comprehensive approach aims to maximize the impact of the attack and increase the likelihood of a ransom payment.
According to Group-IB’s report, different variants of the ransomware are tailored for specific platforms, each with its own set of command-line options. The Windows variant, in particular, offers extensive control over execution, including safe mode execution and network spreading capabilities.
“RansomHub has targeted over 600 organizations globally, spanning sectors such as healthcare, finance, government, and critical infrastructure, firmly establishing it as the most active ransomware group in 2024.”
Group-IB
A specific RansomHub attack, lasting under 14 hours, was investigated by Group-IB. The attackers initially exploited a vulnerability in a Palo Alto firewall (CVE-2024-3400) and then brute-forced VPN credentials to gain access. They then compromised the domain controller using vulnerabilities CVE-2021-42278 (sAMAccount Spoofing) and CVE-2020-1472 (ZeroLogon) to gain control, moved laterally within the network accessing NAS servers and shared folders, and exfiltrated data using Filezilla.
The attack culminated in disabling backups, deploying ransomware, and ultimately encrypting critical data. The attackers then left, leaving behind traces of their activity, which Group-IB’s DFIR team investigated further. This attack sequence, from initial compromise to final data encryption, is visually represented in this image by Group-IB.
This highlights the importance of patching known vulnerabilities, as emphasized by Martin Jartelius, CISO at Outpost24: “It’s difficult to victim-blame when it comes to zero-day exploits or supply chain breaches, but when an organization is hit by a vulnerability that has been patched for over four years, it’s clear that someone within the team has knowingly taken on a significant risk,” explained Martin.
“The kill chain doesn’t begin with this exploit; it starts with initial access. Organizations must focus on hardening their external attack surface and training staff to reduce the likelihood of breaches. Leaving systems unpatched or intentionally vulnerable is a serious security misstep.”