Kransom ransomware hides within the StarRail game using DLL side-loading and a legitimate certificate from COGNOSPHERE PTE. LTD. Bypassing detection, this malware delivers an encrypted payload. Analyze it in ANY.RUN’s interactive sandbox.
Researchers at ANY.RUN have discovered that the Kransom ransomware is being disguised as a game to evade detection. This malware employs DLL side-loading to execute its payload, using a legitimate certificate from COGNOSPHERE PTE. LTD. The latter adds an extra layer of deception to its attack.
Overview of Kransom Ransomware
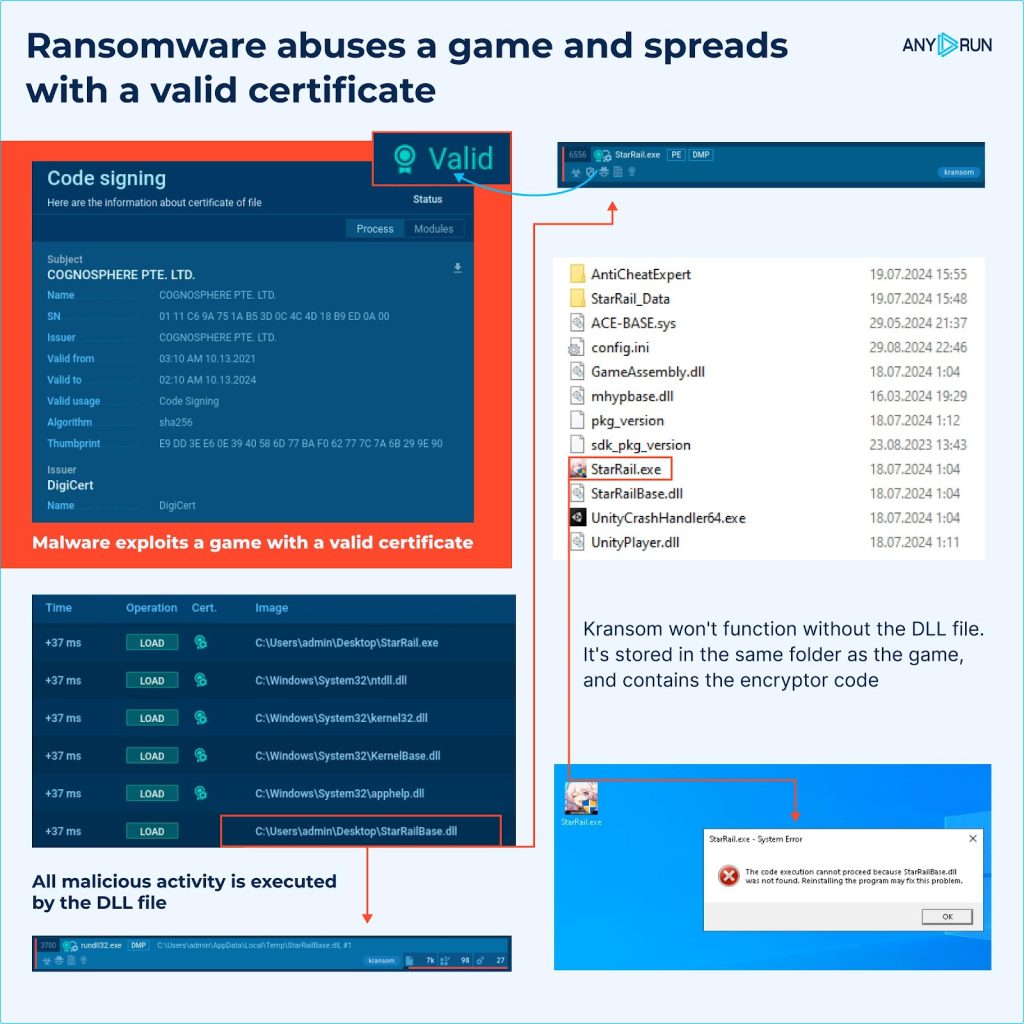
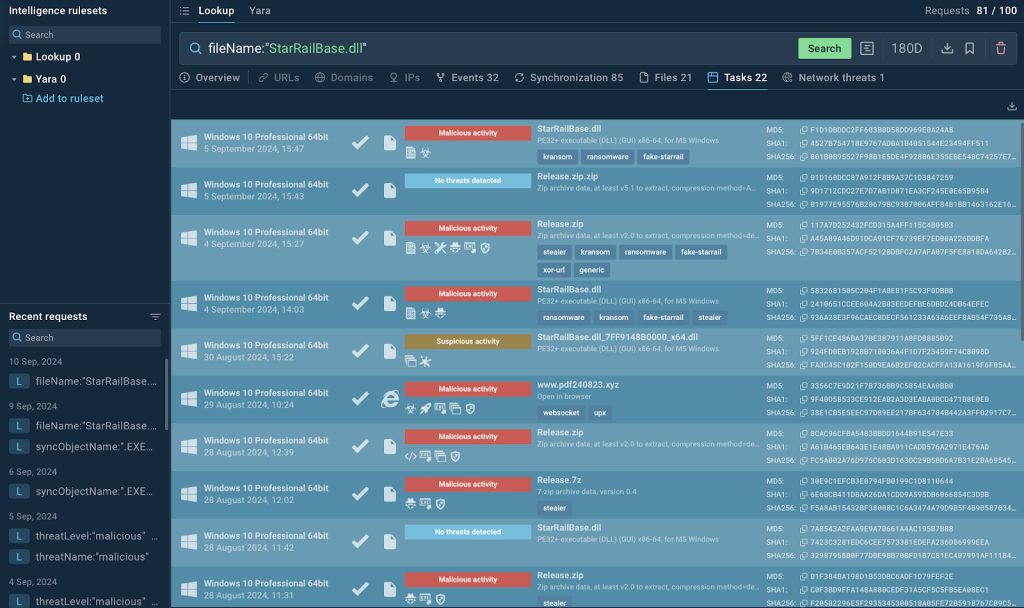
Kransom ransomware is cleverly disguised within the game StarRail, a legitimate software used as a front to trick users. The malware relies on a DLL file stored in the same directory as the game, which contains its encrypted ransomware code.
This is a classic case of DLL side-loading, where a legitimate executable file loads a malicious DLL, allowing the ransomware to hijack the execution flow.
Legitimate Certificate with Malicious Intent
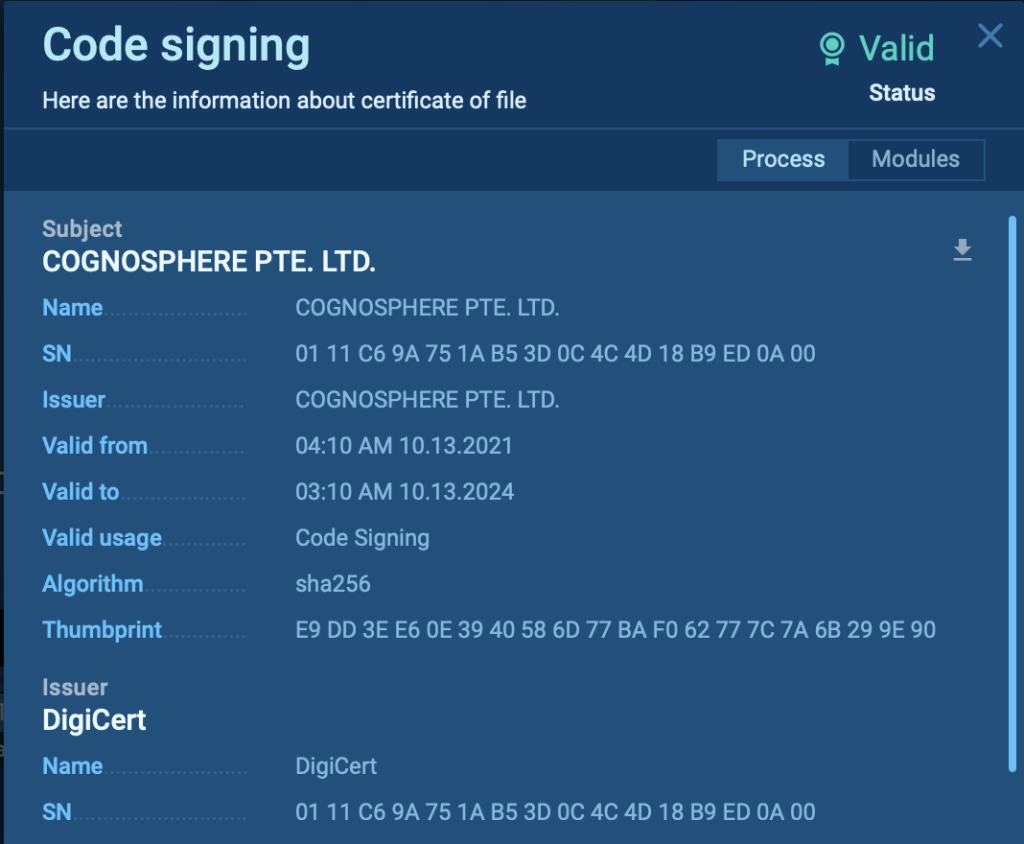
One of the most deceptive elements of Kransom is its use of a legitimate certificate from COGNOSPHERE PTE. LTD. By using a trusted certificate, the malware is able to bypass many traditional security measures, as the system recognizes the software as harmless.
However, malicious actions take place once the StarRailBase.dll is loaded by the executable, initiating the ransomware attack.
How Kransom Ransomware Works
To observe how Kransom ransomware works, a sample of this malware can be uploaded to a malware sandbox like ANY.RUN. The sandbox allows anyone to carry out a full analysis of the malware’s execution process, from its initial stages to the completion of its payload.
The legitimate StarRail game serves as a mask for the ransomware, which won’t function without the presence of the malicious StarRailBase.dll file. This DLL contains the ransomware’s encrypted payload, which is then executed by the game’s EXE file.
It should be noted that the game StarRail, developed by HoYoverse, is completely safe when used in its original form. However, Kransom takes advantage of the game’s structure to embed its malicious code in the same folder, making it difficult for users to notice anything unusual.
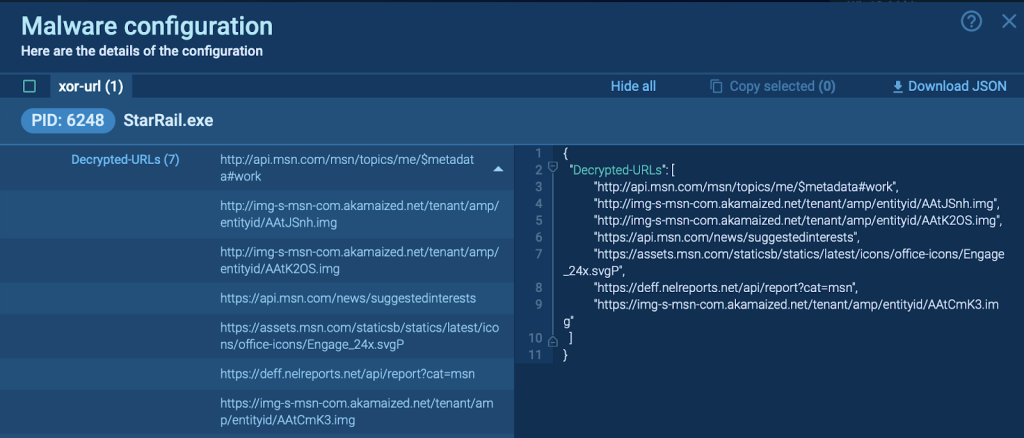
The ransomware code within the DLL is encrypted using XOR, making it harder to detect. Tools like ANY.RUN can help security analysts uncover what’s been XORed, providing crucial insight into the malicious content.
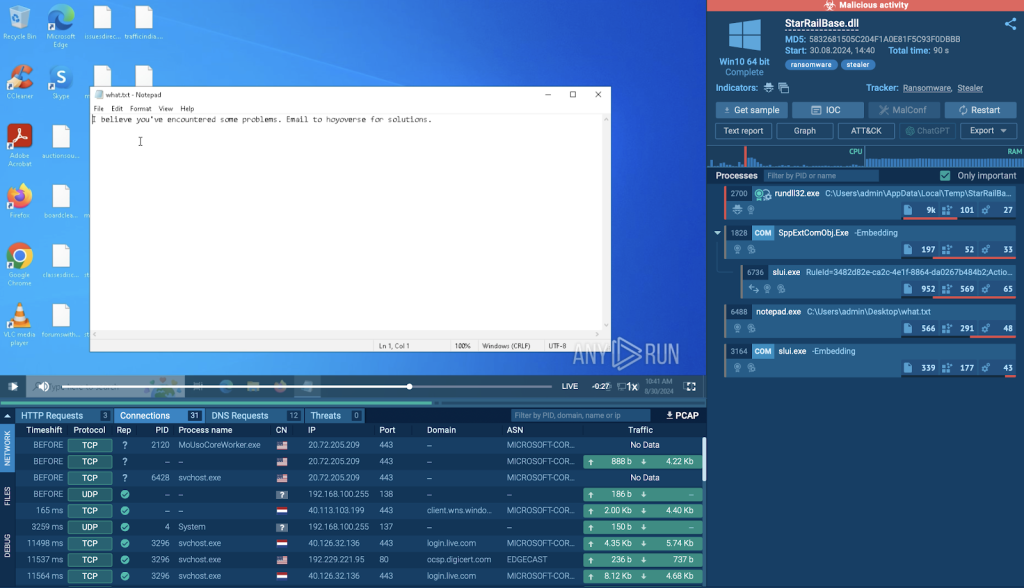
Once the ransomware is activated, users are met with a message: “I believe you’ve encountered some problems. Email to hoyoverse for solutions.”
You can have a more comprehensive analysis of this malware by searching for additional samples in ANY.RUN’s TI Lookup tool.
Try ANY.RUN Sandbox for Free
To analyze your own malware and phishing samples in a fully interactive Windows 10 x64 or Linux VM environment, create a free ANY.RUN account using your email.
ANY.RUN’s cloud sandbox allows you to interact with files, URLs, and the system as if you were using a standard computer. You can download attachments, solve CAPTCHAs, and even reboot the entire system during analysis.
For advanced features like private mode and collaboration tools, you can request a 14-day free trial directly from ANY.RUN’s official website.
RELATED TOPICS
- Analysis of Top Infostealers: Redline, Vidar and Formbook
- New ransomware locks files & asks victims to play PUBG game
- This Ransomware tells users to play a Japanese game – That’s all
- PythonAnywhere Cloud Platform Abused for Hosting Ransomware
- New Ransomware Asks User to Play a Game while Encrypting Data