If you have a smart camera at home or a small website for your business, you could be helping hackers without even knowing it, as cyber criminals are breaking into thousands of everyday devices using the RondoDox botnet. They are building a botnet, which is basically a giant army of hijacked computers that they control from far away.
According to a report from CloudSEK, these attackers are now exploiting a critical flaw called React2Shell (CVE-2025-55182). This flaw is found in Next.js, a popular tool used to build websites. It is very dangerous because it lets hackers take over a computer or server without needing a password.
A Calculated Three-Step Takeover
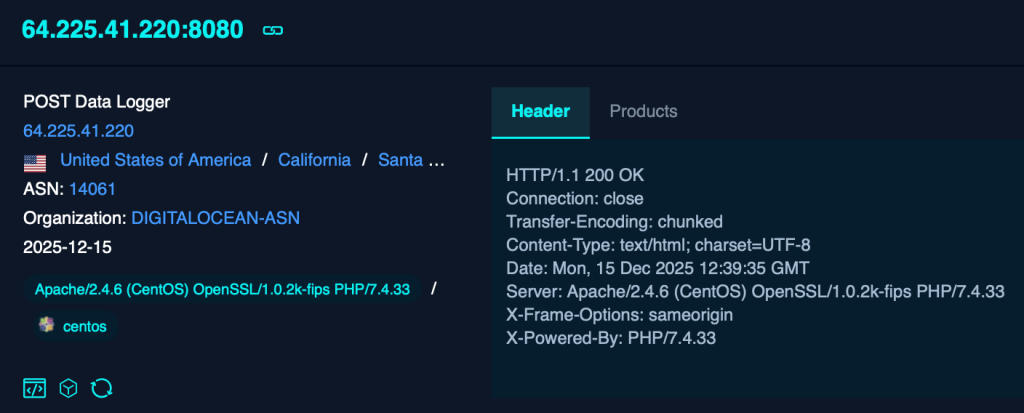
Right after this security flaw was discovered in December 2025, the RondoDox group began hunting for victims. Data from the Shadowserver Foundation shows that over 90,300 systems were left wide open by the end of the year. While the US has the most at-risk devices (over 68,000), thousands of others are vulnerable in Germany, France, and India.
Further investigation revealed that the hackers didn’t just start overnight; they used a three-step plan to grow, starting in early 2025 when they tested for basic website weaknesses like SQL injection to trick databases. By the summer, they began mass-scanning for popular platforms like WordPress and Drupal, while also targeting home Wavlink routers. By the end of the year, the attack became fully automated.
In their blog post, researchers noted six control centres sending out ten different versions of the virus to hit almost any type of machine architecture, from high-end cloud servers to basic home equipment.
Who is at Risk?
RondoDox can infect almost any device. The most common targets are:
- Websites: Any site built with Next.js or WordPress.
- Home Routers: Brands like D-Link, Netgear, and TP-Link.
- Smart Tech: IP cameras and other gadgets connected to your Wi-Fi.
The Hacker’s Toolkit
Once inside, the hackers install hidden programs with strange names. They use “/nuts/poop” to steal the device’s power to mine digital currency and “/nuts/x86,” a version of the infamous Mirai malware, to help the botnet spread.
Perhaps the most aggressive tool is “/nuts/bolts.” This “health checker” scans the device every 45 seconds to kill any other rival viruses. It even wipes out old digital footprints to make RondoDox the sole owner of your device.
The best way to stay safe is to keep your technology updated. If you run a website, install the latest security fixes for Next.js right away. For your home, it is a smart move to connect gadgets like smart cameras to a separate Wi-Fi network so that if a hacker gets into a camera, they cannot reach your private phone or computer. Also, you should check your router’s settings and install any new software updates immediately.