Palo Alto Networks’ Unit 42 security researchers have discovered that Russian state-sponsored hackers are abusing the latest Brute Ratel C4 or BRc4 attack simulation/penetration testing tool in their recent and active attacks.
Hackers Using BRc4 to Evade Detection?
Unit 42 threat intelligent experts wrote in their report that the malicious payload linked with the BRc4 tool allows it to evade detection by most commonly used security products. Moreover, researchers believe that hackers are targeting entities worldwide, but primarily their targets are located in South and North America.
In a warning issued by the researchers, they have urged the cybersecurity fraternity to look for signs of malware, including the BRc4 tool. Researchers dubbed it a “uniquely dangerous” tool designed to avoid detection by EDR (endpoint detection and response) and AV (antivirus) scanners.
How was The Abuse Detected?
According to Palo Alto Networks’ researchers, someone uploaded a document to the VirusTotal website for inspection in May 2022. This document included a BRc4-associated payload. Surprisingly, 56 of VirusTotal scanners couldn’t recognize the malware, after which it was assigned Benign status.
Possible Perpetrator?
Researchers identified that the malicious payload’s packaging hinted at the involvement of the APT29 group (Advanced Persistent Threat group 29) The Dukes or Cozy Bear as the deployed tactics were similar to this group. CozyBear is a Russian state-sponsored hacker group. Previously it was involved in the devastating Solar Winds attacks in 2020.
What is BRc4 Tool, and What are its Capabilities?
Dark Vortex sells this penetration testing tool. It is similar to the commercially available, legit Cobalt Strike attack simulation tool, which IT departments mainly use in testing defenses and staff training.
Previously, attackers used illegal versions of Cobalt Strike for scanning victims in their attacks, and now they are abusing BRc4. This tool has been used since 2020, mainly by Indian security engineer Chetan Nayak (aka Paranoid Ninja) who used to work for red teams at mainstream western security vendors.
However, the product was recently commercialized. Nayak explained that this tool was designed for reverse-engineering major security products. But Unit42 researchers claim it is a relatively new tool that boasts similar capabilities as Cobalt Strike. Once installed, BRc4 can capture screenshots, create Windows system services, patch AMSI, and upload/download documents.
Attack Delivery Mechanism
The malicious, self-contained, and benign ISO file is included in the primary lure file, which is a Windows shortcut file (LNK) disguised as an MS Word file, complete with the fake Word icon. The file is sent to the target via spear-phishing, or the victim downloads it by a second-stage downloader.
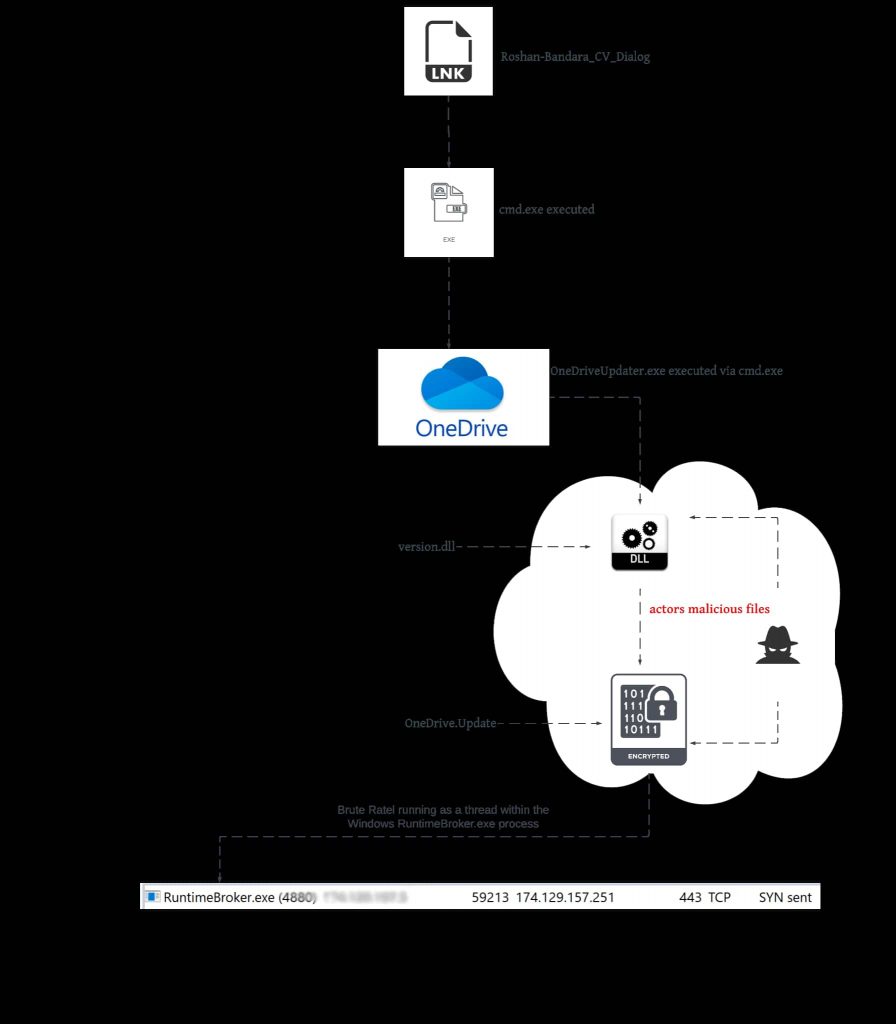
An analysis of the files shows it appears to be a CV for someone named Roshan Bandara, but this is actually the main malicious file. This file appears on the user’s hard drive after double-clicking, and when the lure file is clicked, it installs the BRc4.
Researchers discovered 41 malicious IP addresses, 9 BRc4 samples, and three impacted organizations.
“While we lack insight into how this particular payload was delivered to a target environment, we observed connection attempts to the C2 server originating from three Sri Lankan IP addresses between May 19-20.”
Unit 42
More Russian Hackers Topic
- Russian language hacking forums warming up to Chinese hackers
- Pro-Russia Killnet Group Hit Top Lithuanian websites with DDoS Attacks
- BlackGuard Password Stealing Malware Sold on Russian Hacking Forums
- New Russian Android Malware Tracks GPS Location and Spies on Victims
- Feds Dismantle Russian Rsocks Botnet Powered by Millions of IoT Devices








