Recent findings from the research firm Recorded Future’s Insikt Group reveal that it only takes two seconds of distraction for a professional’s private data to fall into the wrong hands.
According to Recorded Future’s latest blog post, a Russian state-sponsored hacking group, known as BlueDelta (or Fancy Bear), has been carrying out sneaky campaigns to steal login information from professionals worldwide.
Reportedly, betweet Feburary and September 2025, BlueDelta targeted individuals is specialised frields like energy and nuclear research, particularly in Türkiye and Europe. Researchers observed that the campaign’s objective seems to be credentials harvesting.
How the Scams Work
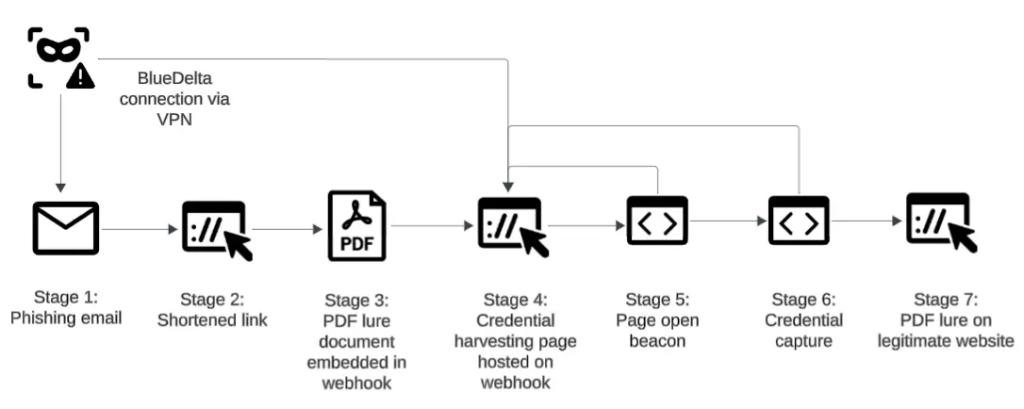
Researchers noted that the hackers are becoming much more convincing because, instead of using obvious fake links, they show the victim a real document first. For example, a target may receive a link that opens a legitimate-looking PDF about climate change or international politics, such as a report from the Gulf Research Centre (GRC) regarding Israel and Iran.
Another such lure was a report from the EcoClimate Foundation titled “Climate Action as a Strategic Priority,” which specifically targeted scientists working on renewable energy. While the victim is distracted by these documents, the website is actually working in the background. After just two seconds, the page automatically switches to a fake login screen.
Further investigation revealed that these fake pages were designed to look like:
- Google: Using Portuguese-language pages to trick users.
- Sophos VPN: Aimed at staff within a European think tank.
- Microsoft Outlook (OWA): Specifically targeting military staff in North Macedonia and IT experts in Uzbekistan.
Simple but Effective Tactics
It is worth noting that BlueDelta doesn’t use expensive equipment for these attacks; they rely on free internet services like Webhook.site, ngrok, and InfinityFree. According to researchers, this makes the attacks a “low-cost, high-yield” way to steal data because when a victim enters their details, the hackers’ code automatically saves the info and then sends the user back to the real website.
“The use of Turkish-language and regionally targeted lure material suggests that BlueDelta tailored its content to increase credibility,” the blog post reads. By the time the victim is redirected to the real login page, their credentials have already been stolen.
This activity represents a major expansion of BlueDelta’s operations, showing their commitment to collecting information from government and research networks.
That’s why, experts urge you to always check links for suspicious addresses like webhook.site, and never trust login prompts that appear suddenly while reading a PDF. It also helps to ensure you have multi-factor authentication active on all professional accounts to stay protected.
(Photo by KOBU Agency on Unsplash)