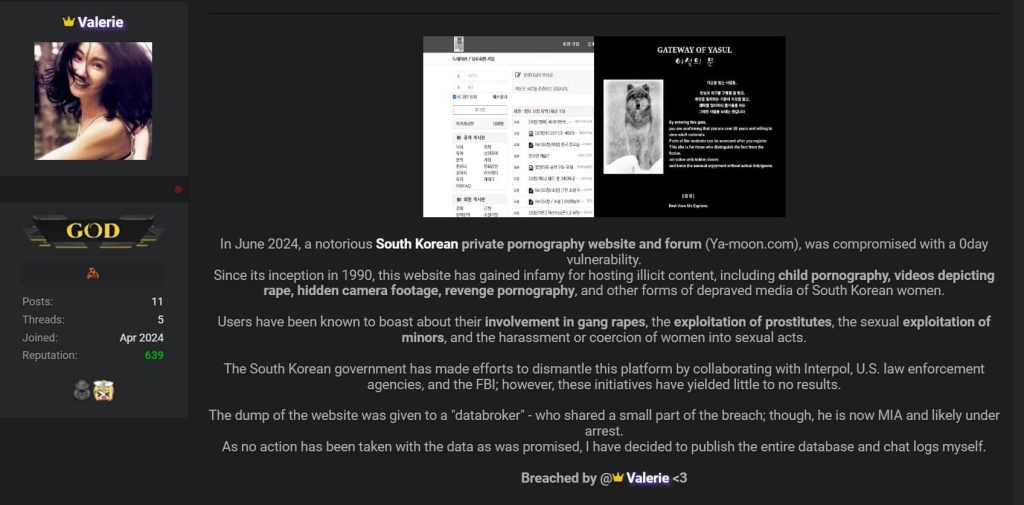
A hacker using the alias “Valerie” is claiming to have hacked Ya-moon, a notorious South Korean private pornography website and forum. According to the hacker, the hack took place in June 2024 using a zero-day vulnerability, but the details of it have only been shared earlier today.
The site, which has been operating since 1990, is infamous for hosting illicit content, including Child Sexual Abuse Material, also known as CSAM, hidden camera footage, revenge porn, and videos depicting rape. Its users often brag about gang rapes, the sexual exploitation of minors, and the intimidation of women into sexual acts.
The hacker claims that despite multiple attempts by South Korean authorities, Interpol, and U.S. law enforcement to dismantle the site, efforts had previously failed to bring it down. Now, a massive data breach has exposed the platform’s users, including 326,000 lines of data.
The Hack and Leaked Data
According to the hacker, the website’s entire database and chat logs have been published online. Initially, the data was handed over to a “databroker” who leaked a small portion but then disappeared, allegedly arrested. Frustrated with the inactivity surrounding the breach, the hacker decided to release the full dataset independently.
Key Data Exposed in the Ya-moon.com Breach
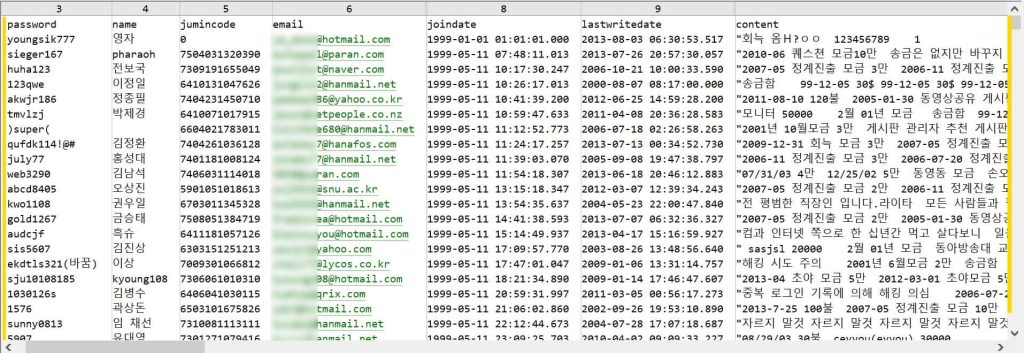
As seen and analysed by Hackread.com’s research team, the leaked database includes personally identifiable information (PII) and incriminating activity logs, making this quite a sensitive leak. The dataset contains:
1: User Identification
- Usernames
- IP addresses (revealing user locations)
- Email addresses (52,000 – some linked to real identities)
- Plain-text passwords (suggesting weak security measures)
2: Activity & Behavior
- Date of joining the forum
- Last activity timestamps (showing recent usage patterns)
- Chat logs, containing discussions of illegal activities
- Published content, including uploaded media and discussion posts
3: Private Communications
- Inbox messages exchanged between users
- Potential evidence of coordination or transactions
- Discussions about law enforcement activity, security concerns, and evasion tactics.
If verified, this could be a major blow to users who engaged in illegal activities on the platform, as law enforcement agencies could track down those involved.
Korean-Based User Activity Revealed in the Breach
The majority of users’ IP addresses trace back to South Korea. This confirms that Ya-moon.com is largely a domestic operation, based on South Korean users who engaged in illegal content distribution and discussions. While some may have used VPNs or proxies, many users relied on their real IP addresses, suggesting a lack of security within the forum.
This dataset could also become a crucial investigative tool for South Korean authorities, who have struggled for years to take down networks like this one. If acted upon, it may lead to important arrests and legal action against individuals involved in the platform’s criminal activities.
South Korea and Online Sex Crimes
South Korea has a long history of tackling online sex crimes, including high-profile cases like the Nth Room scandal, where perpetrators exploited victims through encrypted chatrooms. However, forums like Ya-moon.com continued to exist, exposing gaps in enforcement and digital policing.
If authorities acquire and verify the data, arrests and prosecutions could follow, similar to previous dark web takedowns like Operation Dark HunTor and Playpen. This breach may deter users from engaging in illicit activities online, knowing they can be exposed.
Not The First Time
This is not the first instance of hackers targeting sites linked to CSAM and other forms of abuse. In February 2017, Anonymous hacktivists breached Freedom Hosting II, the largest dark web hosting provider at the time, resulting in the shutdown of thousands of CSAM sites. The hosting service managed approximately 11,000 websites, accounting for nearly 20% of all dark web sites that year.